Panini Adware for Android soaks network bandwidth, bad news for users with limited data
SonicWall Capture Labs Threats Research Team has been observing an Android adware that spreads using different app names and icons, this adware does not ask for a plethora of permissions (like most malware) and its network activity typically starts after it downloads a jar file after few minutes of execution. Upon further investigation we found more than 500+ samples that exhibit this behavior from the last two months alone indicating that this campaign is very active in the wild. We named this adware campaign Panini because of the filename of the jar file that gets downloaded.
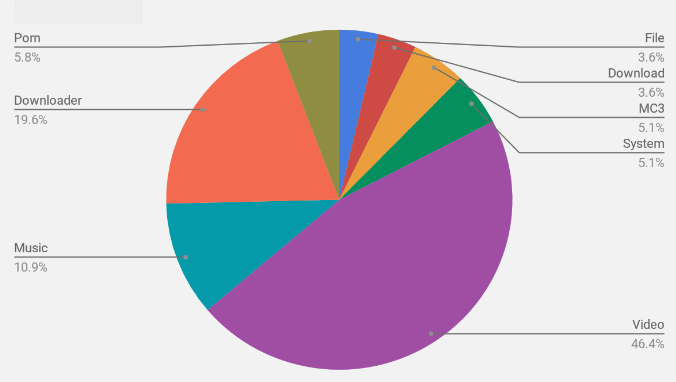
Most of these samples use generic and simple app names such as Video, Downloader and Music; we have been tracking samples belonging to this campaign for a while and below is a chart that shows the breakup of different app names used by samples belonging to this campaign that we analyzed:
As visible above, the app names are fairly generic in nature and might have been chosen to keep the adware hidden in the crowd of Android apps with unique and attractive app names.
Birds of the same feather
There are few similarities among the different samples belonging to this campaign:
Code structure
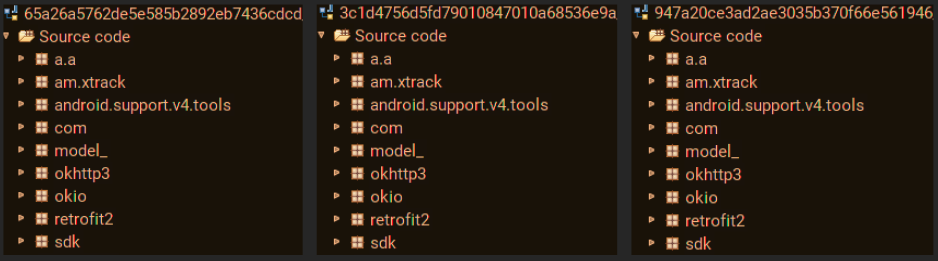
Below is a comparison of code structure from 3 different samples with different app and package names belonging to the Panini Adware campaign:
List of permissions
All of the samples belonging to this campaign request for the following permissions:
- android.permission.INTERNET
- android.permission.ACCESS_NETWORK_STATE
- android.permission.WRITE_EXTERNAL_STORAGE
Similar folder structure from the install location
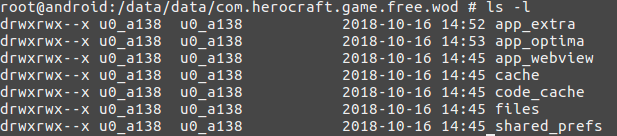
The folder structure on the device post-installation is same for all the samples from this campaign:
Icons being used
All the samples belonging to this campaign use icons from the following set, these set of icons are present in every sample in the resource folder mipmap-xxhdpi-v4:
Icon mind games
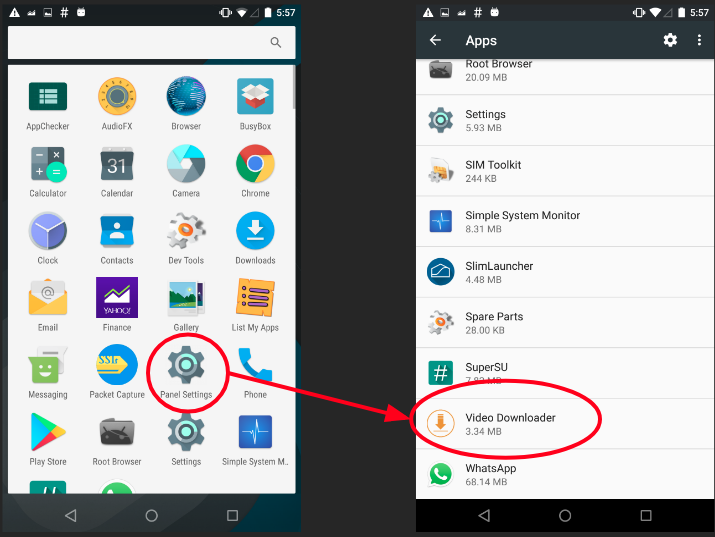
For apps belonging to this campaign, the icon that gets displayed in the app drawer post installation is different from what appears before installation.
Example – For apk com.cradiff.devilfighter (MD5 – c43a22306e1f34bd7ed59f5272e2012b) the icon that appears for this apk is:
Post installation the icon visible in the app drawer is different:
Most likely, the reason for this might be the fact that a user notices a new icon in the app drawer and might click on the new icon out of curiosity to find out when he installed this new app/what this app is about. This is a clever tactic that makes the victim open the app and thereby execute the adware.
We found a folder – mipmap-xxhdpi-v4 – within the resources folder for the apk that contains icons for most of the samples belonging to this campaign:
![]()
The icons are shown (from the list above) based on what is coded in the Android Manifest.xml file:
![]()
Once the adware begins execution, the icon disappears from the app drawer. If the victim tries to remove this app from settings he would see a different icon than the one that appeared in the app drawer. This is most likely a ploy to confuse the victim when he tries to uninstall the apk:
Permissions
Apps belonging to this campaign request for the following permissions:
- android.permission.INTERNET
- android.permission.ACCESS_NETWORK_STATE
- android.permission.WRITE_EXTERNAL_STORAGE
Among these permissions the only dangerous permission is its request to write data to external storage. Usually malware tend to request for a number of normal and dangerous permissions and based on the permission usage we can often determine the behavior of the malware. Considering the only permission requested by this adware is the ability to write to an external storage, we can fairly assume there will be some sort of file that gets downloaded.
That is exactly what happens once the adware begins execution.
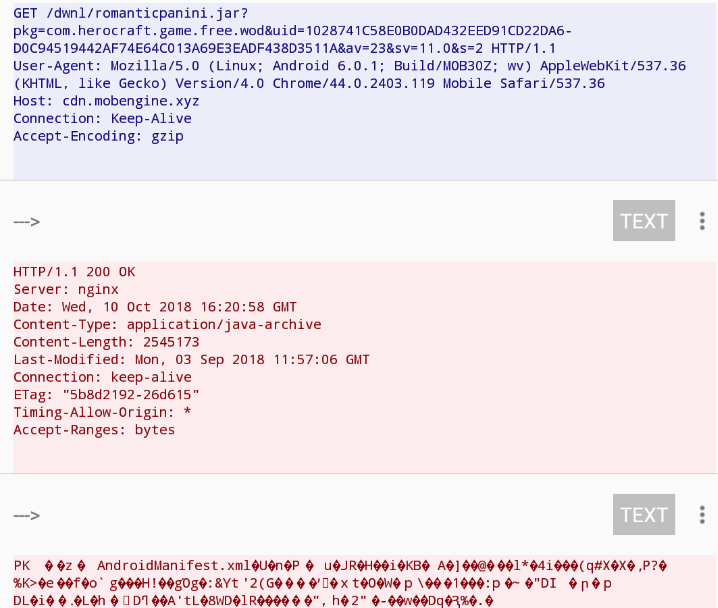
After a few minutes of execution the adware initiates a GET request for a jar file named romanticpanini [Blocked by GAV: JScript.A_161 (Trojan) ]:
The Panini
The file romanticpanini is saved locally in the folder app_extra:
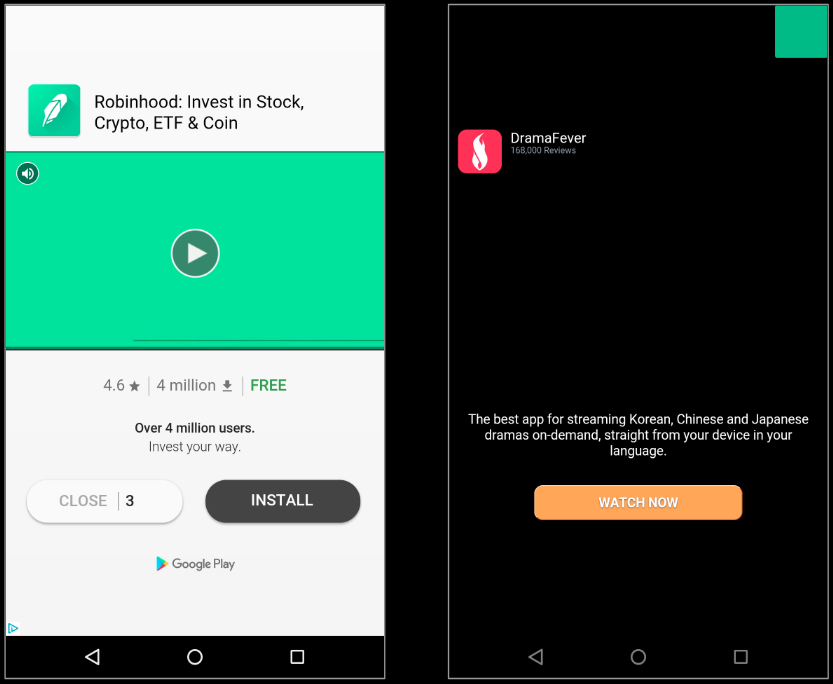
Once the jar file is saved, the network activity on the device multiplies and we start seeing heavy advertisement related traffic, soon enough we saw full screen advertisements pop up regularly on our infected device:
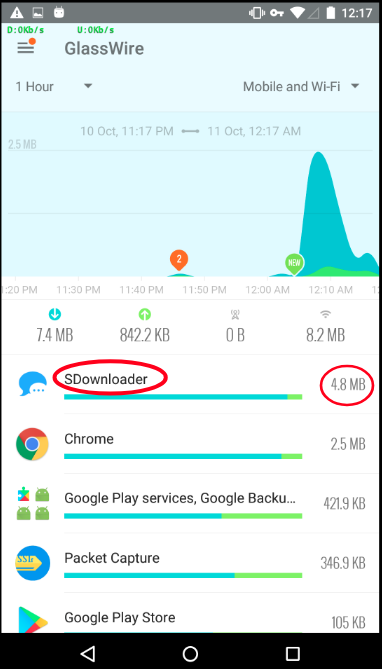
We measured the network traffic in different test conditions and observed a sharp rise in network traffic originating from the adware samples. We ran the test for 10 minutes after an adware sample is installed and executed on the device.
On average we saw data consumption of close to 5MB post infection (as shown in the image below). This does not bode well for users who have limited/capped data plans on their devices as additional data consumption leads to extra charges on the mobile phone bill.
Adware Domains
Every sample from this campaign contains a hardcoded domain, few domains that we encountered during our analysis of Panini adware are:
- cdn.mobengine.xyz
- ccthi.enconfhz.com
- first.luckshery.com
- cthi.nconfhz.com
- three.nameapp.xyz
- api.jetbudjet.in
- api.mobengine.xyz
- con.rsconf.site
- one.nameapp.xyz
- get.confhz.space
- mi1k.io
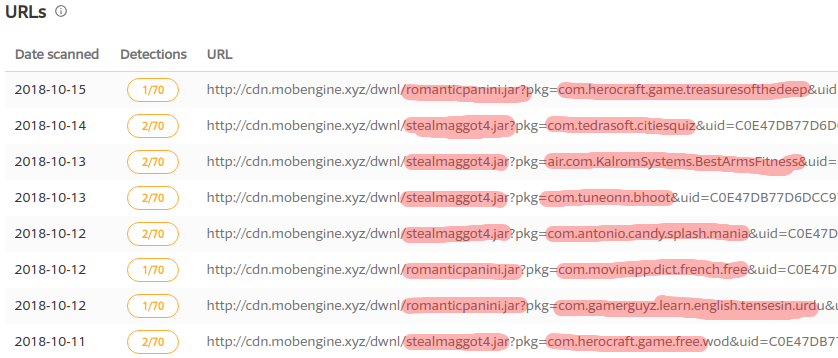
VirusTotal URL scan of one of the domains – cdn.mobengine.xyz – revealed another jar file that is hosted on this domain along with romanticpanini – stealmaggot4.jar:
The image above additionally shows different apps that harbor this campaign.
Distribution
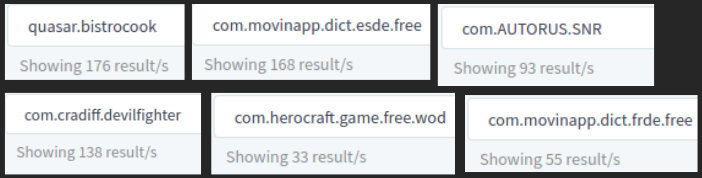
The apps belonging to this campaign use different package and app names, among the samples we observed for the last few weeks few package names repeated a number of times. A quick search on the Android malware collaboration portal Koodous gives us results for a high number of samples from this campaign, below image shows the number of results for apps with a particular package name:
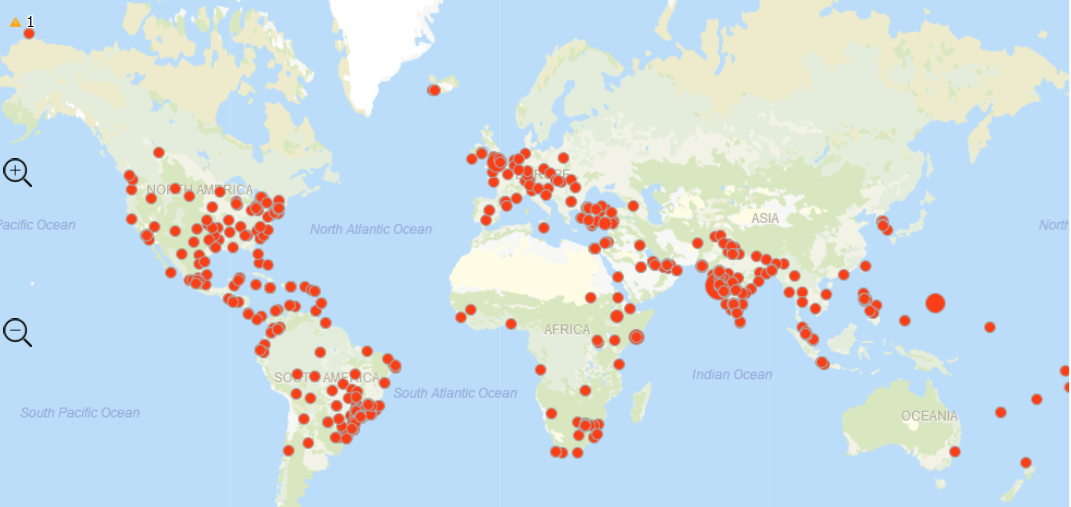
Below image shows the geographical distribution of the hits for the signatures belonging to this campaign:
Conclusion
Traditionally adware has always fallen in the grey area in terms of calling them malicious/blocking them. Most of the times they do not pose a risk towards user’s data and privacy like traditional malware but are more of a ‘nuisance’ when they pop full-screen ad’s and/or consume large amounts of data. The Panini adware campaign falls under the same umbrella where it poses a risk in terms of data consumption. This particularly hits users who use a mobile plan with restricted data limits, for users with unlimited data plans usually the data speeds reduce once a particular limit is reached so they are affected as well.
It is a good habit to routinely check the network data consumption on our devices. Running a routine check using Network Monitoring apps can give an idea if a particular app is consuming a lot of network data and can potentially uncover an adware on the device.
SonicWall Capture Labs provides protection against this threat via the following signatures:
- GAV: AndroidOS.Panini.AD (Trojan)
- GAV: AndroidOS.Panini.AD_2 (Trojan)
- GAV: JScript.A_161 (Trojan)
Below are few samples belonging to this campaign:
- 778e132ed56527e775fb9029603968c3 – com.AUTORUS.RetroDrag
- 89a7e6a607be86c702b6f4a1126f5002 – com.AUTORUS.RetroDrag
- 215de7aab595fb4bb2d41faa555dc467 – com.AUTORUS.RetroDrag
- c43a22306e1f34bd7ed59f5272e2012b – com.cradiff.devilfighter
- a359526b2c7ae82c25d1182ea583cea5 – com.cradiff.devilfighter
- 791adeb47a81a94e50e84bb5c78a21d3 – com.cradiff.devilfighter
- b3ead04496567b171be4953ba20f90ce – com.cradiff.devilfighter
- 927bac83d1c8df5dd160d6687fe8cc40 – com.cradiff.devilfighter
- ab4483a82c1bbe3022c935b36cf38ba3 – com.cradiff.devilfighter
- 49e0bb2f5347693b897a212615973e0a – com.cradiff.devilfighter
- 8a23ad4b9777319a08e8b68a3c99bdab – com.cradiff.devilfighter
- 4778de1b22cf844dd182fa062013b5b7 – com.cradiff.devilfighter
- 74515dc638dd0ba76ea0513e1c026767 – com.cradiff.devilfighter
- 9d355e11199335beeeec6267ff47a995 – com.gameloft.android.GAND.GloftM3HP
- 0c99a2cb99e946b3cac401fce4619d65 – com.gameloft.android.GAND.GloftM3HP
- ee641d3491110767edba029527c63200 – com.herocraft.game.free.gibbets2
- aa98977c4360c04d5b0f9f63b314076a – com.movinapp.dict.enit.free
- 7a2d3c11965e676d926091ffec9f36f5 – com.movinapp.dict.enit.free
- 5816d134ea058d5ec30f5760ea19cb39 – com.movinapp.dict.enit.free
- cae85059276a70c436942f2b4dc7aec4 – ch.nth.android.contentabo_l01_sim_univ
- 2d8eaf4c9b20810166fc216ee4558e56 – ch.nth.android.contentabo_l01_sim_univ
- 341188b0810d2943dfa0f419fd3d66ef – com.pnr.engproverbsandsayings
- b8dd1dd5aa2e73cdf90880ea2211a565 – com.pnr.engproverbsandsayings
- 867f97568eb4ff260c679a6f51508372 – com.pnr.engproverbsandsayings
- 0b734a3f4d934b0859aa0e65733bd99f – com.pnr.engproverbsandsayings
- 789d63e0d80c31c99b412b01ee460578 – com.tedrasoft.enigmas
- a78befd074b562e94655cd76c6d82dc7 – com.tedrasoft.enigmas
- 53a3415d888966d2efc8d6d4b5a8faec – com.tedrasoft.gravity.pipes
- d305b2a8107a253f0a4cfbe5a381d120 – com.zddapps.beststatus