Kraken 1.52 Ransomware served by compromised Anti Spyware site
The SonicWall Capture Labs Threat Research Team have been recently tracking new a ransomware family known as Kraken. This ransomware has reportedly been served by a compromised anti spyware site superantispyware.com. The operators demand 0.75 BTC for file decryption and are quick to tell you not to waste their time if you are not serious.
Infection Cycle:
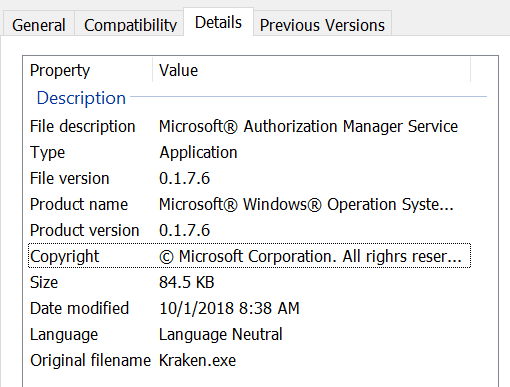
The malware executable file contains the following metadata:
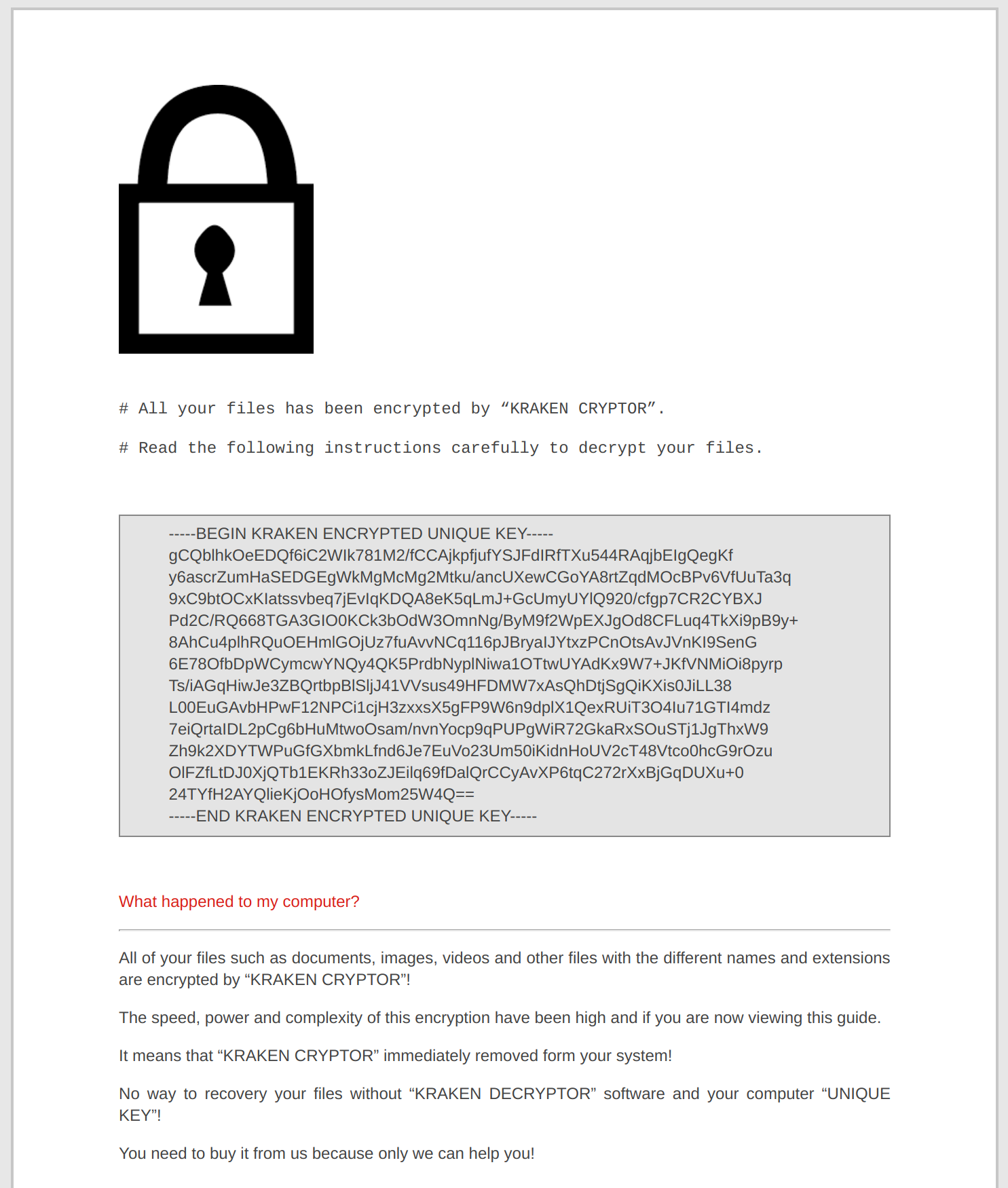
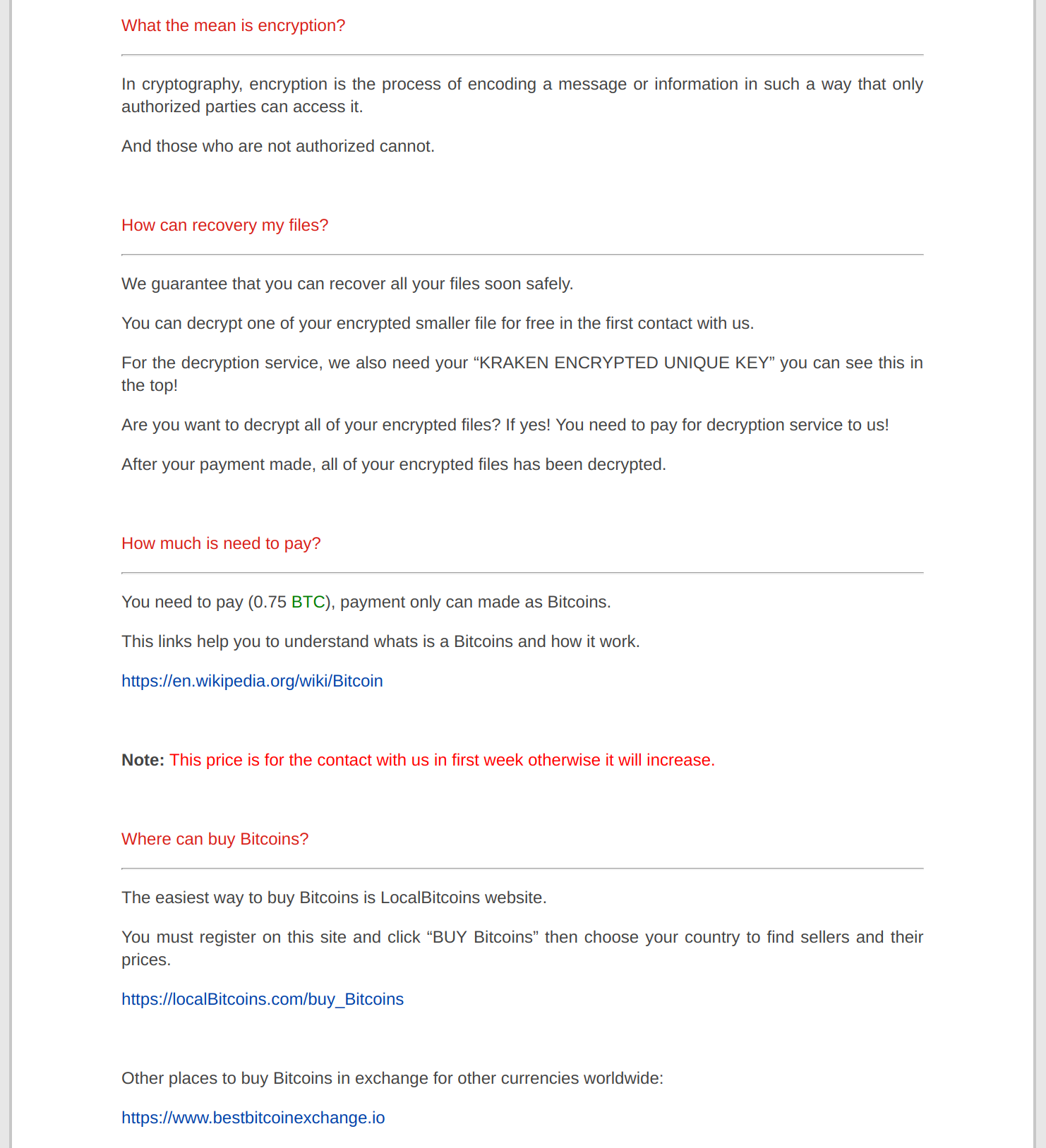
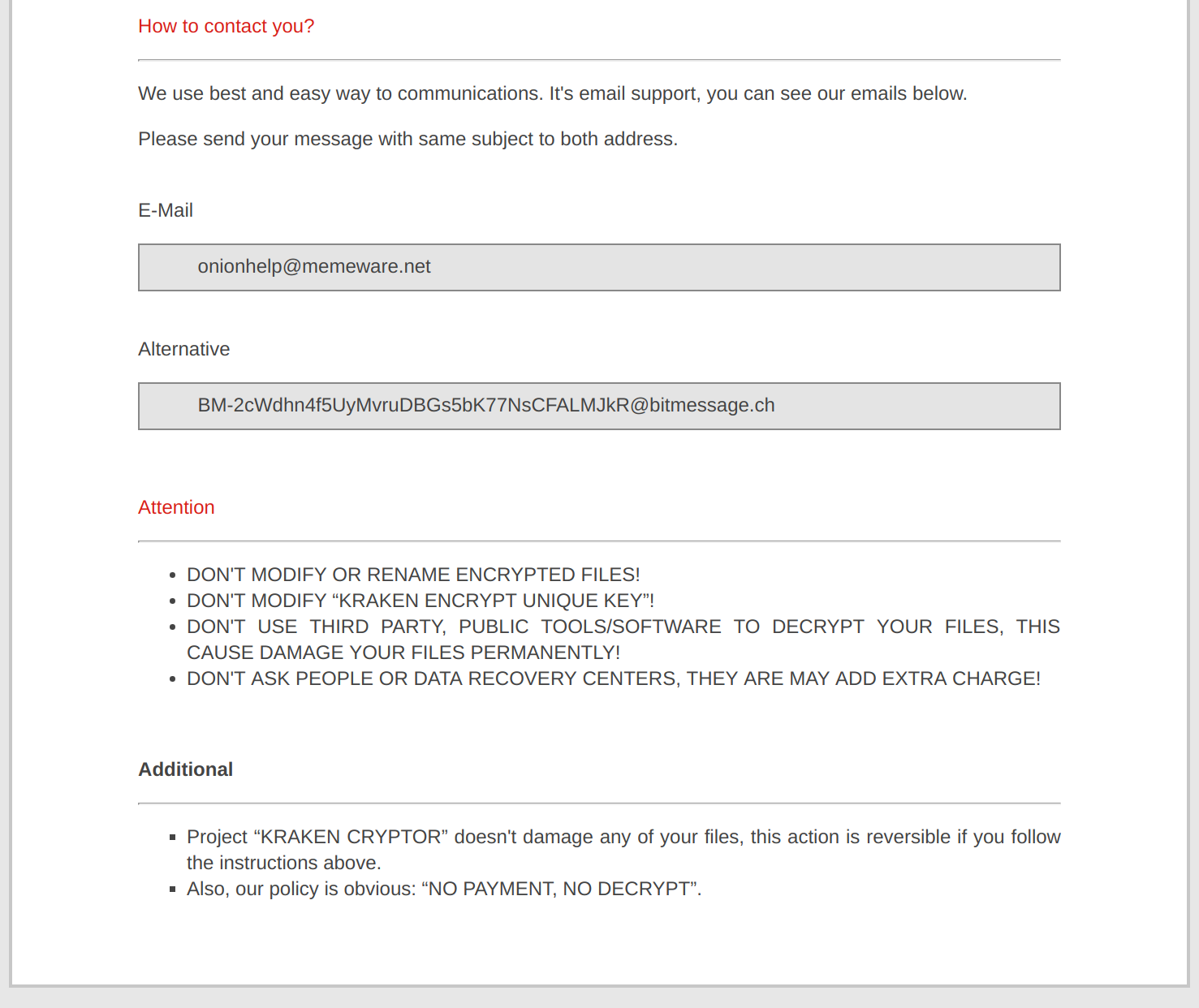
Upon infection, the trojan encrypts files on the system and drops # How to Decrypt Files.html into every directory containing encrypted files. # How to Decrypt Files.html contains the following html page:
Encrypted files are named <numericvalue>-lock.onion. eg. 00000001-lock.onion, 00000002-lock.onion etc. The numeric value is incremented for each file encrypted.
The trojan makes a DNS request to ipinfo.io and obtains the victims external ip address. Apart from this there is no other network traffic.
Upon inspecting the malware executable file we came across an embedded configuration file. This suggests that it may be generated from a ransomware creation kit. The configuration file contains the following data in JSON format:
"project":{
"name":"kraken",
"version":1.52,
"comment":"When the researchers party hard, our parties harder!"
},
"module":{
"anti_forensic":true,
"anti_revere":true,
"anti_virtual": false,
"anti_smb":false,
"anti_rdp":false,
"country_check":true,
"keyboard_check":true,
"registry_check":true,
"fix_device":true,
"network_device":true,
"flash_device":true,
"extension_bypass":true,
"rapid_mode":true
},
"core": {
"public_key": "2kHjgBUx6QQSkwRnLs5c/AdbjroDU4j5AanCabrpjBLnKCWGKwmlWQZR/
RcCRF5KyAfMmPIks1JYEvh9bMh1Mv1CvbofBi4/HAttuictsmiVSRvMxRNDw3U29W0Li/PoSOYfBPUvHP58BhLTt3G5/
AikhhHmf4FGtigUEkq5n/u60Zh0362s2nY1Ev0qEx+d45oDnYaoMIlihrcxtho7uqbu1sZPsgezzyEBl7f2BKOjXxD4ML8Cpwv69EHH
+3tgt2gn9ys921NI3d3gjI8Z+GRSYnKNx1qRCoiCPQqL6MjUHEEOXkMOWITh/CacwQDMEEn2SlxDDisLvybdjw9y1Q==",
"support_email_1": "onionhelp@memeware.net",
"support_email_2": "BM-2cWdhn4f5UyMvruDBGs5bK77NsCFALMJkR@bitmessage.ch",
"price": 0.75,
"price_unit": "BTC",
"new_extension": "onion",
"main_cipher_key_size": 128,
"session_cipher_key_size": 64,
"aes_cipher_key_size": 32,
The configuration contains the following files and directories to be skipped:
"skip_files": [
"bootsect.bak",
"desktop.ini",
"iconcache.db",
"ntuser.dat",
"thumbs.db"
],
"skip_directories": [
"$recycle.bin",
"system volume information",
"$windows.~bt",
"boot",
"drivers",
"programdata",
"all users",
"windows",
"windows.old",
"appdata",
"programdata",
"sample videos",
"sample pictures",
"sample music",
"my videos",
"my pictures",
"my music",
"test folder"
],
It will also kill the following processes if running:
"process_stop": [
"agntsvcagntsvc",
"agntsvcencsvc",
"agntsvcisqlplussvc",
"dbeng50",
"dbsnmp",
"firefoxconfig",
"msftesql",
"mydesktopqos",
"mydesktopservice",
"mysqld",
"mysqld-nt",
"mysqld-opt",
"ocomm",
"ocssd",
"oracle",
"sqbcoreservice",
"sqlagent",
"sqlbrowser",
"sqlservr",
"sqlwriter",
"sqlwb",
"synctime",
"tbirdconfig",
"xfssvccon"
],
The configuration has a “target_extensions” section. Files with the following extensions will be encrypted:
1cd 3dm 3ds 3fr 3g2 3gp 3pr 7z 7zip aac ab4 abd accdb accde accdr accdt ach acr act adb adp
ads agdl ai aiff ait al aoi apj arw ascx asf asm asp aspx asx atb avi awg back backup backupdb
bak bank bay bdb bgt bik bin bkp blend bmp bpw c cdb cdf cdr cdr3 cdr4 cdr5 cdr6 cdrw cdx
ce1 ce2 cer cfg cfn cgm cib class cls cmt config contact cpi cpp cr2 craw crt crw cs csh cs
csl css csv dac dat db db3 dbf dbx db_journal dc2 dcr dcs ddd ddoc ddrw dds def der des design
dgc dit djvu dng doc docm docx dot dotm dotx drf drw dtd dwg dxb dxf dxg edb eml eps erbsql
erf exf fdb ffd fff fh fhd fla flac flb flf flv flvv fpx fxg gif gray grey groups gry h hbk
hdd hpp html ibank ibd ibz idx iif iiq incpas indd info info_ ini jar java jnt jpe jpeg jpg js
json kc2 kdbx kdc key kpdx kwm laccdb lck ldf lit lock log lua m m2ts m3u m4p m4v mab mapimail
max mbx md mdb mdc mdf mef mfw mid mkv mlb mmw mny moneywell mos mov mp3 mp4 mpeg mpg mrw msf
msg myd nd ndd ndf nef nk2 nop nrw ns2 ns3 ns4 nsd nsf nsg nsh nvram nwb nx2 nxl nyf oab obj
odb odc odf odg odm odp ods odt ogg oil omg orf ost otg oth otp ots ott p7b p7c p12 pab pages
pas pat pbf pcd pct pdb pdd pdf pef pem pfx php pif pl plc plus_muhd pm! pm pmi pmj pml pmm
pmo pmr pnc pnd png pnx pot potm potx ppam pps ppsm ppsm ppsx ppt pptm pptm pptx prf ps psafe3
psd pspimage pst ptx pwm py qba qbb qbm qbr qbw qbx qby qcow qcow2 qed qtb r3d raf rar rat raw
rdb rm rtf rvt rw2 rwl rwz s3db safe sas7bdat sav save say sd0 sda sdb sdf sh sldm sldx sql
sqlite sqlite-shm sqlite-wal sqlite3 sqlitedb sr2 srb srf srs srt srw st4 st5 st6 st7 st8 stc
std sti stm stw stx svg swf sxc sxd sxg sxi sxm sxw tbb tbn tex tga thm tlg tlx txt usr vbox
vdi vhd vhdx vmdk vmsd vmx vmxf vob wab wad wallet war wav wb2 wma wmf wmv wpd wps x3f x11 xis
xla xlam xlk xlm xlr xls xlsb xlsm xlsx xlt xltm xltx xlw xml ycbcra yuv zip
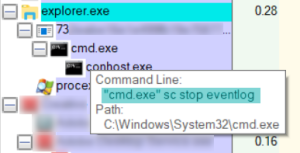
The Trojan attempts to stop the event log service by issuing the command “sc stop eventlog”:
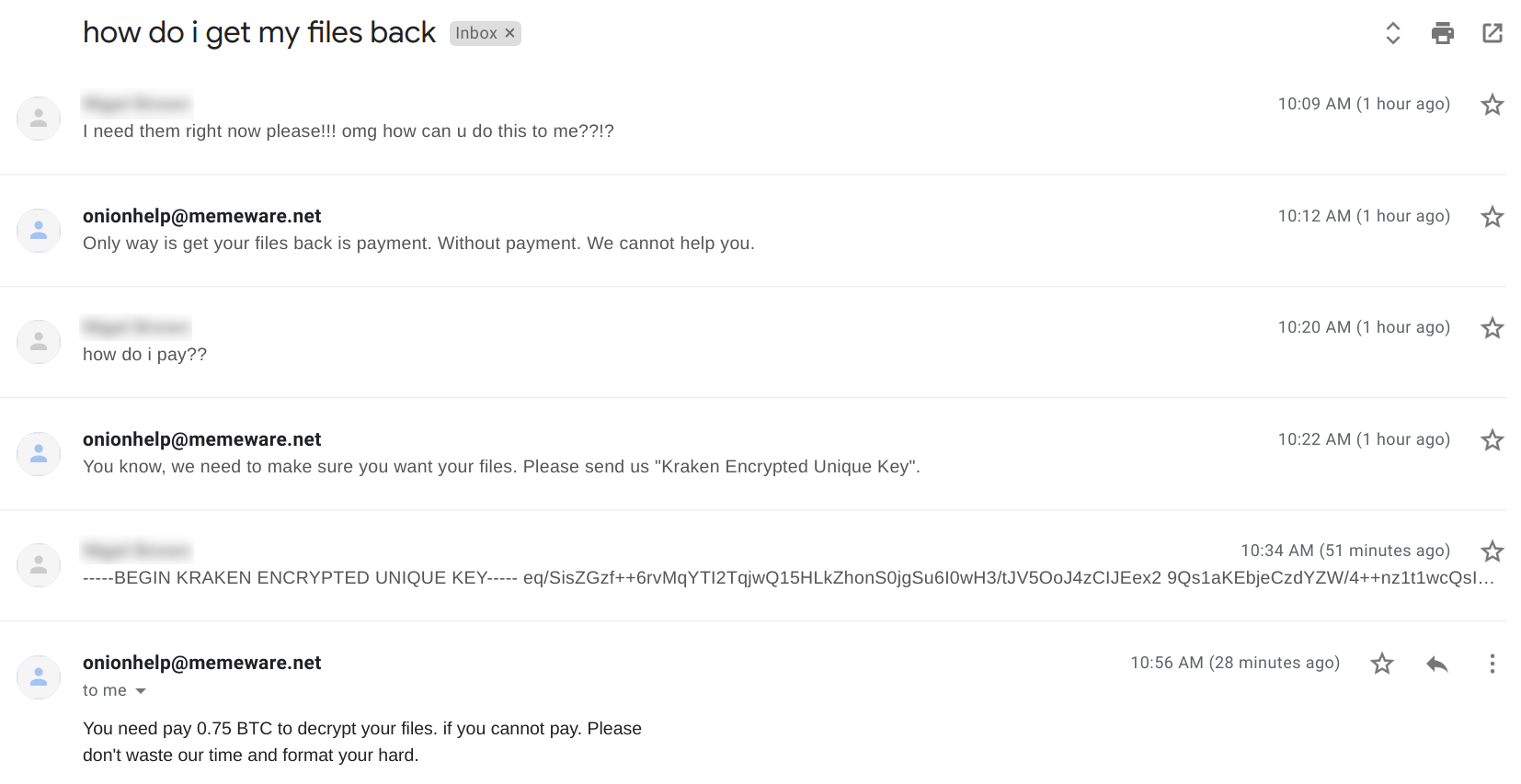
We had the following conversation with the operator via email. The operator demands 0.75 BTC ($4,923USD) for file recovery:
SonicWALL Gateway AntiVirus provides protection against this threat via the following signatures:
- GAV: Kraken.RSM (Trojan)
- GAV: Kraken.RSM_2 (Trojan)
- GAV: KrakenCryptor.KJ (Trojan)




