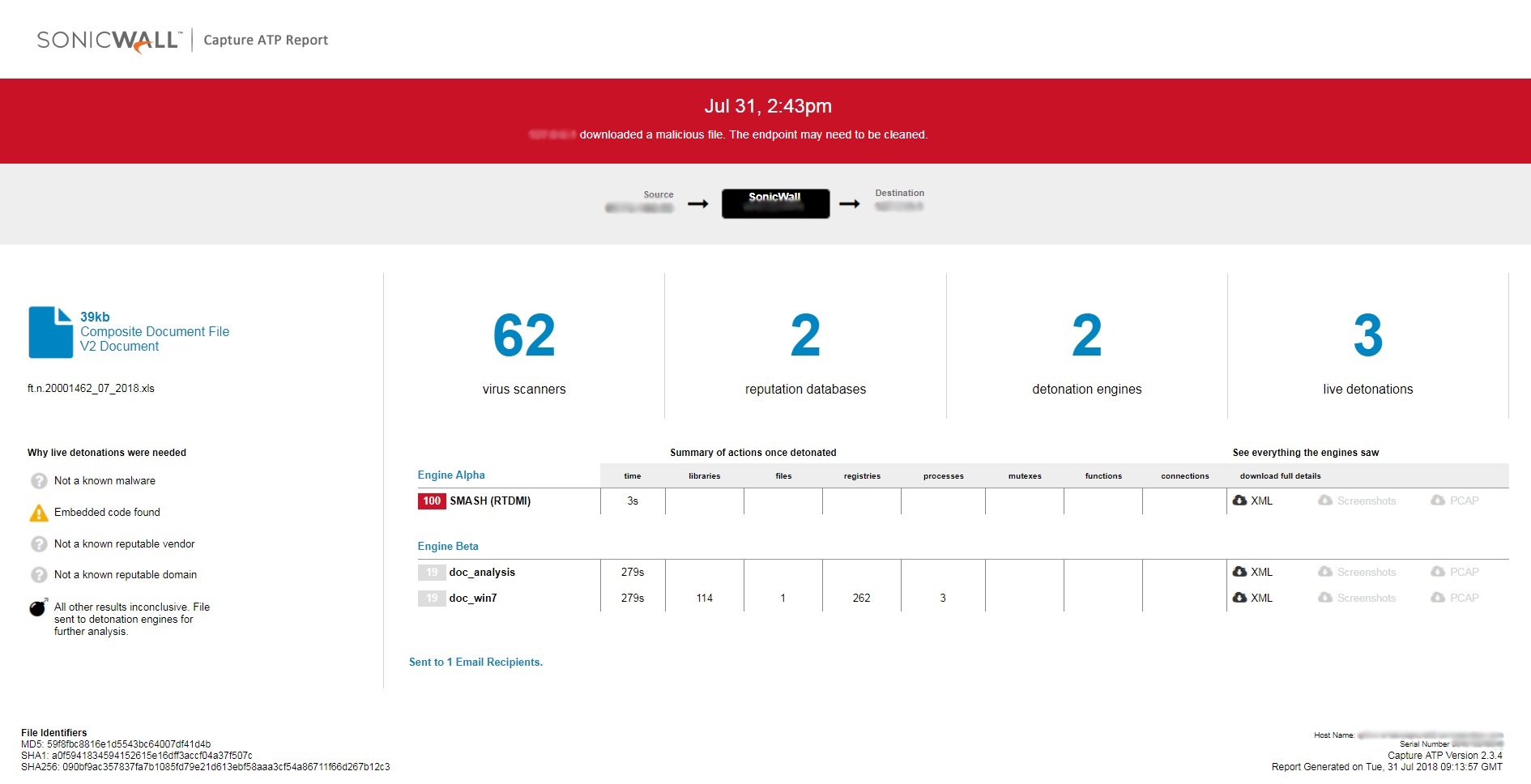
Italy is targeted again by Ursnif delivered via malicious Microsoft Excel Documents
SonicWall RTDMI engine detected multiple targeted attacks using Microsoft Excel documents directed towards Italy. Similar attacks were observed a month back as well. Information about these fresh attacks were not available in any of the popular threat intelligence sharing portals like the VirusTotal and the ReversingLabs.
Fig-1 : Virustotal results for the malicious file
Upon closer analysis of one of the detected samples, it is found to be using a malicious macro which downloads payload if the victim happens to be from a particular geographical area (Italy in this case). The payload malware is not downloaded directly to avoid detection. The download happens in multiple stages. In the first stage the VBA macro code executes a command present in a cell of the excel spreadsheet. This cell containing code has a very small visible size to hide from the user. We are observing this new evasion mechanism being used on recent malicious office documents where the actual malicious elements are part of the sheet data and not on the VBA macro code.
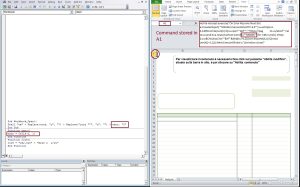
Fig-2 : command inside a cell in excel
In the second stage, the code on the hidden cell downloads an encrypted powershell script. The downloaded script is then decrypted using a hard coded key shown in Fig-2. Below image shows both the encrypted and decrypted versions of the powershell script.
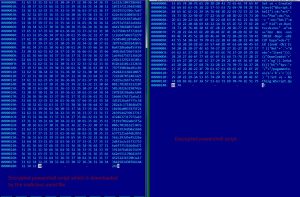
Fig-3 : Encrypted and decrypted script
This second stage again downloads another powershell script which is then in-turn used to identify victim geographical location as shown below:
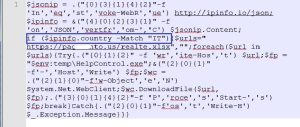
Fig-4 : script finding Geo-location of user
The payload which belongs to the Ursnif family at the time of analysis, is being delivered if the victim is from the specific geographical area.
Indicators of Compromise (IOC):
- 090bf9ac357837fa7b1085fd79e21d613ebf58aaa3cf54a86711f66d267b12c3 : Malicious Excel File
- hxxps://pag[xxx]nto.us/abcd
- hxxps://pag[xxx]nto.us/abc
- hxxps://pag[xxx]nto.us/realte.xlsx
- e1e1ec90f643619c1001504897e7b00ed0906d102d8730975b9d0db1a87ec5c1 : Ursnif Malware
Hashes of similar malicious excel files:
- 150564c5252c417c093814e7b965d327d342098bc80d4c64667df143703ed274
- e43c3adfe2b117abbabc735e2bfe1d95b2fcac86d4b3aecffbbc6d793942f044
- 96cede3e965bec5d4d6a558ddd01256ea160cb98ebfa6d4f431f46117c975496
Capture ATP report for this file: