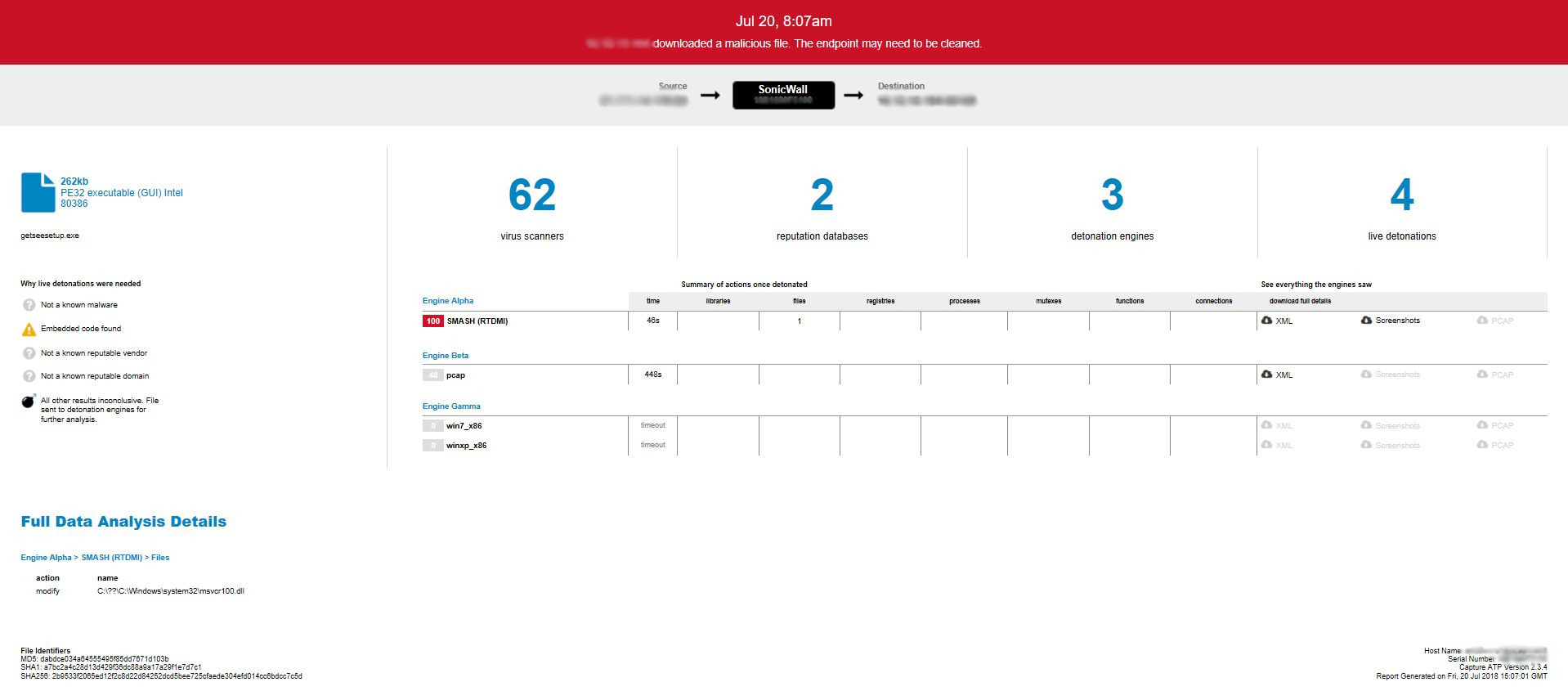
AZORult infostealer first spotted by Sonicwall RTDMI engine
SonicWall RTDMI engine observed a malware campaign delivering a new variant of AZORult Stealer. AZORult is an infostealer, which collects various information from the infected system and sends it to the server. The non-existence of this malicious file at the time of detection on popular malware search portals (VirusTotal or Reversing Labs) indicates the effectiveness of the RTDMI engine.
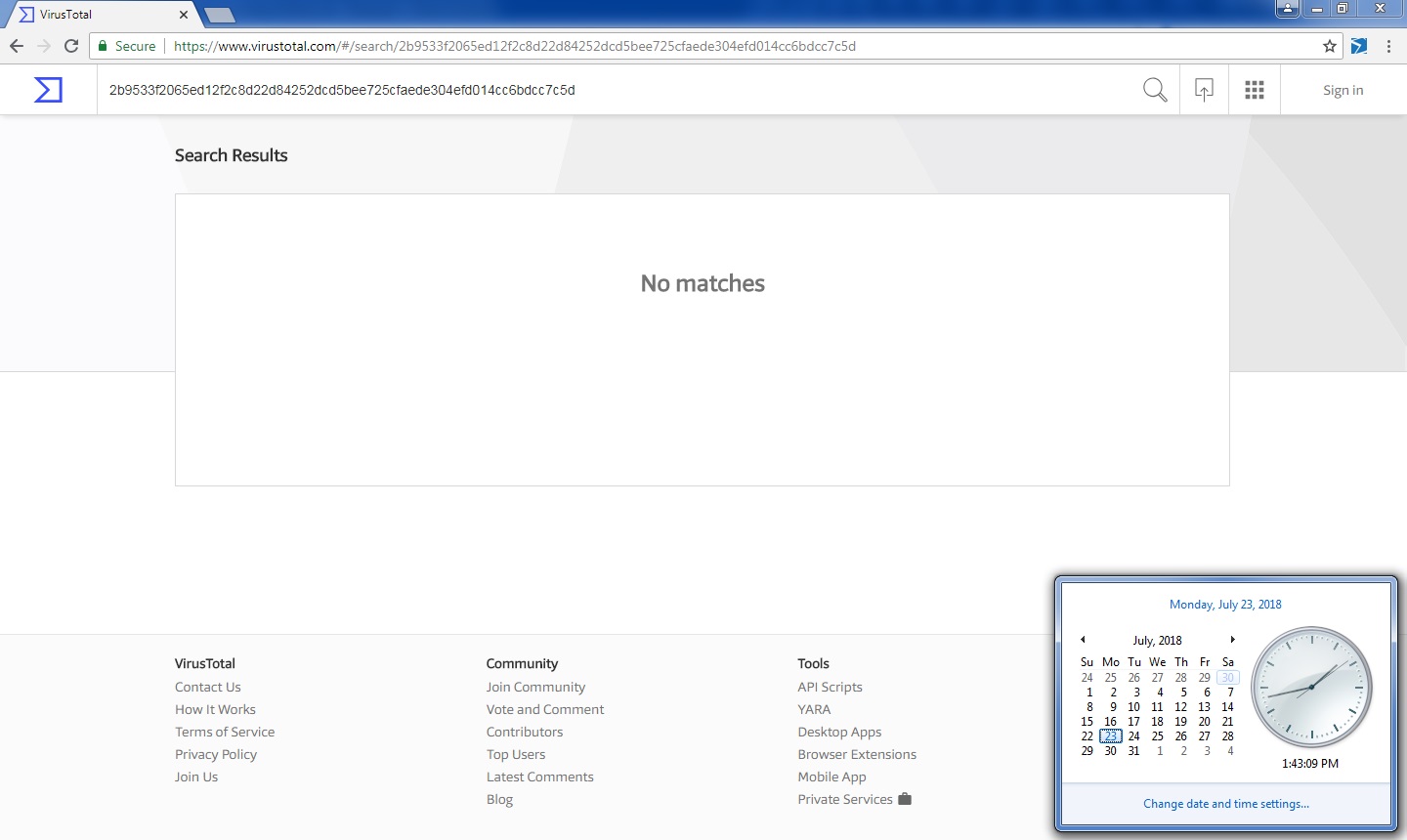
Analysis of AZORult
Upon analysis, it is found that to avoid detection the malware is packed with a custom packer.
After unpacking, it first retrieves the information from the system which includes following:
- Machine GUID
- User Name
- Machine Name
- Windows version
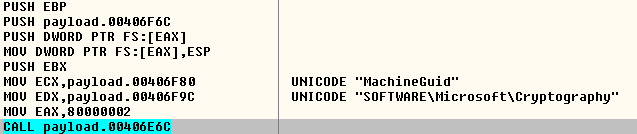

Fig-3 : Querying GUID
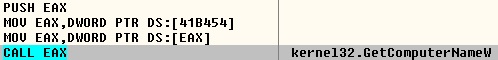
Fig-4 : Get computer name
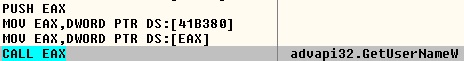
Fig-5 : Get user name
After retrieving the information it creates a mutex name to ensure only one instance is running on the system.
The malware encrypts the information with a hardcoded XOR key “0x6521458A” and concatenates them.
After concatenating the encrypted data, it urlencodes them. The urlencoded data is as below:
“%39%34CA%38%32%31%2D%31%38%35%37%39%31%31E%2D%37%36%31%30%37%37A%32%2D%30%36%37%36D%36%36%
39%2DBAB%36%39%36E%30%37”
All these stolen information are sent to the C&C server.
The malware connects to this IP address “37.48.105.177”.
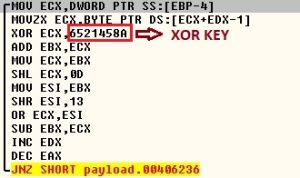
Fig-6 : XOR loop to decrypt stolen information
The malware also steals the accounts stored in browsers and various software that are present on the infected machine example skype, telegram etc.
On further analysis, it is also found that the malware looks for cryptocurrency information stored on the infected machine and steals these information along with the passwords.
The following image shows the strings related to the information the malware looks for in the system: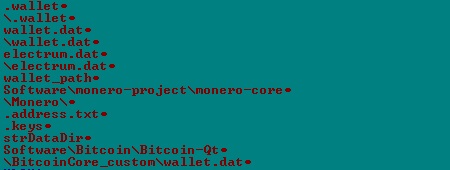
Fig-7 : Cryptocurrency related string
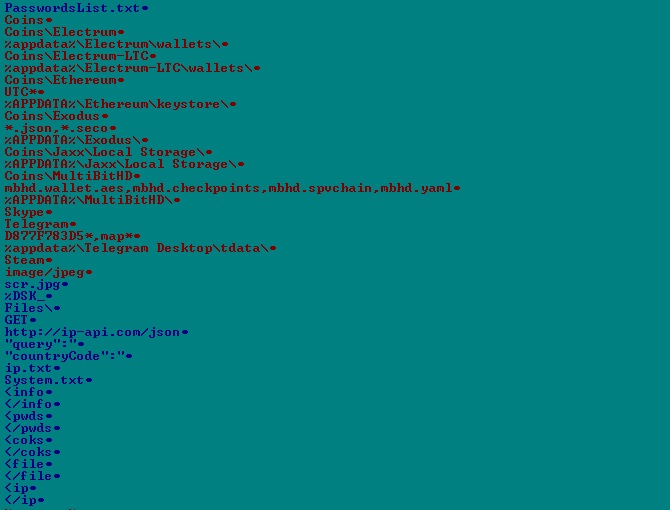
Fig-8 : Cryptocurrency and password related strings
The malware also takes the IP address and country code of the infected machine by querying the following URL:
“http://ip-api.com/json”
All the above information are stolen and are sent to the C&C.
Indicators of Compromise: 2b9533f2065ed12f2c8d22d84252dcd5bee725cfaede304efd014cc6bdcc7c5d