Gandcrab Ransomware actively spreading in the wild
The SonicWall Capture Labs Threat Research Team observed reports of a new variant family of Gandcrab Ransomware [Gandcrab.RSM] actively spreading in the wild.
Gandcrab Ransomware encrypts the victims files with a strong encryption algorithm until the victim pays a fee to get them back.
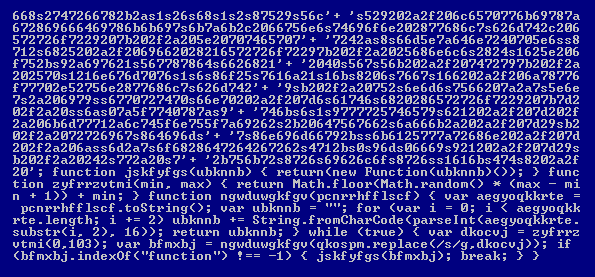
An example of a Script file that leads to the Gandcrab ransomware.
Infection Cycle:
The Malware adds the following files to the system:
- Malware.JS
- %Userprofile%\ Local Settings\Temp\[Random Numbers].exe
- Executable dropper File
- %Userprofile%\Desktop\ CRAB-DECRYPT.txt
- Instruction for recovery
- %Userprofile%\ Local Settings\Temp\[Random Numbers].exe
Once the computer is compromised, the Ransomware downloads its own executable file from its own C&C server and copies into %Temp% folder and runs following commands:

While Ransomware is encrypting files, it will encrypt all files and append the .CRAB extension onto each encrypted file’s filename.
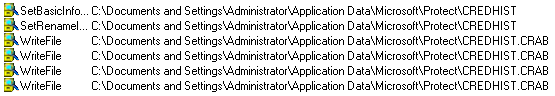
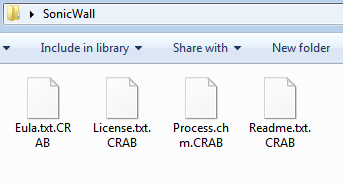
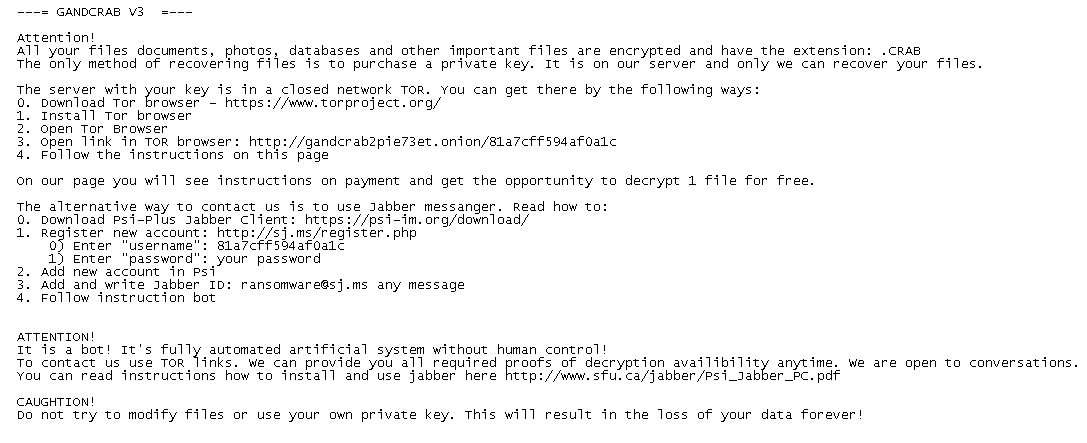
The Ransomware encrypts all personal documents and files it shows the following webpage containing a message reporting that the computer has been encrypted and to contact its developer for unlock instructions.
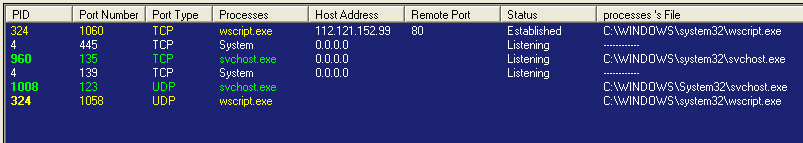
Command and Control (C&C) Traffic
Gandcrab performs C&C communication over HTTP protocol.
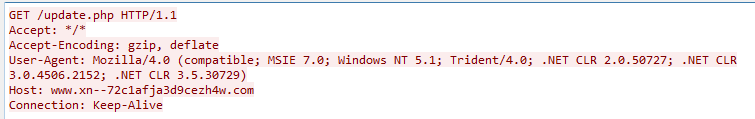
The malware sends HTTP request to its own C&C server with following formats, here is an example:
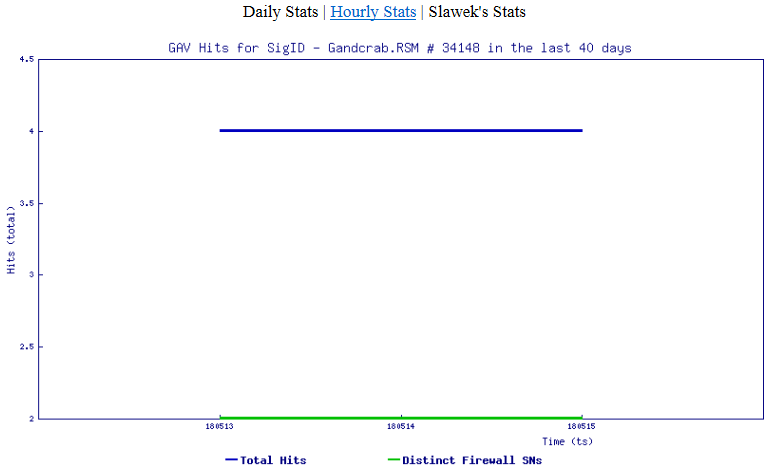
We have been monitoring varying hits over the past few days for the signature that blocks this threat:
Sonicwall Capture Labs provides protection against this threat via the following signature:
- GAV: Gandcrab.RSM (Trojan)





