Fake UPS label creator drops Java-based jRAT Trojan
This week, the SonicWall Capture Labs Threat Research Team has seen a java-based trojan delivered via malware spam. These unsolicited emails came very similar as other malspam campaigns, disguised as important messages containing links to download official documents. The sample we analyzed however, came with a link to download a fake UPS shipping label creator.
Infection cycle:
This trojan may use the following variations of filenames:
- uspslabel.jar
- Order_2018.jar
- contract332178.jar
- scanned_copy.jar
- receipt_02092018.jar
- DHL delivery.jar
- invoice.jar
Upon execution it makes a DNS query to a domain associated with the anonymous hidden service accessibile via the TOR network.
![]()
It creates a randomly named directory within the %TEMP% directory where it makes a copy of itself.

It also creates a text file named “ID.txt” which contains a GUID as an infection marker. Another empty placeholder directory was also observed created.
It also drops a class file within the %TEMP% directory. It then spawned java.exe to execute the file using the following command:
- “C:Program FilesJavajre7binjava.exe” -jar C:DOCUME~1USERLOCALS~1Temp_0.83800868772929068034313497563112697.class”
This then initiated a copy of the full Java folder and its content from the Program files directory into the AppData directory using xcopy.exe.
- xcopy “C:Program FilesJavajre7” “C:Documents and SettingsUsersApplication DataOracle” /e
![]()
From here on, another class file was then executed. This time using the java.exe copy from the AppData directory.
- “C:Documents and SettingsUsersApplication DataOraclebinjava.exe” -jar C:DOCUME~1USERSLOCALS~1Temp_0.1308514375193299350395911777849595.class”
It then spawned cmd.exe which then executed the following command:
- WMIC /Node:localhost /Namespace:\rootcimv2 Path Win32_PnpSignedDriver Get /Format:List
This command will use WMI to show the list of signed drivers which is a known malware sandbox detection technique to check for VMWare, VirtualBox or any sandbox drivers.

Several other instances of java.exe was then observed running, syn flooding from localhost.

These java.exe instances, each launched a copy of the class file from the %Temp% directory. After just a few minutes of executing this Trojan, the following copies of class files have been created in the %temp% directory.

We have also observed it kept a constant connection to another remote server. Sending encrypted data, using the following certificate as seen on the screenshot below.
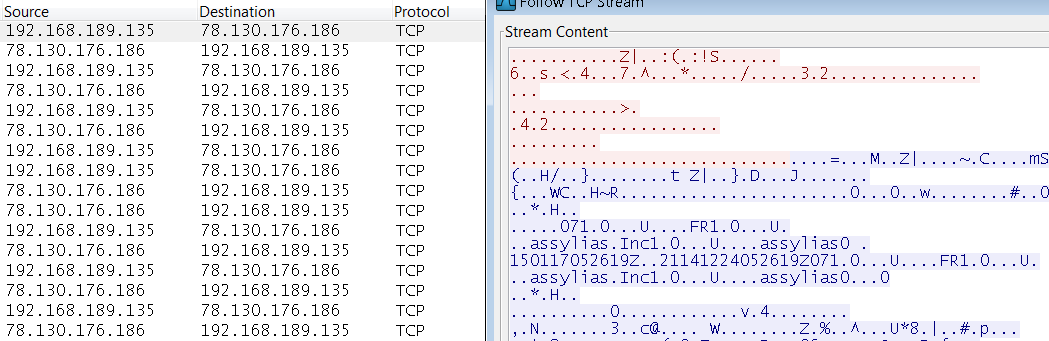
Because of the prevalance of these types of malware spam campaigns, we urge our users to always be vigilant and cautious with any unsolicited email with unsuspecting document attachments or website links, particularly if you are not certain of the source.
Sonicwall Capture Labs provides protection against this threat with the following signatures:
-
- GAV: Java.Fake.UPS (Trojan)
- GAV: Jrat.A (Trojan)





