First TOR-based file encrypting Android Ransomware (June 10, 2014)
Dell SonicWALL Threats Research team reported last month about a new Android malware that locks up mobile devices until the victims pay a ransom to unlock the phone, called AndroidLocker. Recently, we came across a newer variant of the Android Ransomware called SimpleLocker that uses the same scareware tactics of pornography distribution but also adds two new features: A) It encrypts all the user files including documents, images, and videos stored on the mobile’s SD card. B) It uses TOR network for its Command and Control communication. This is the first ever Android malware family that performs file encryption as well as uses TOR for its communication.
We have already shared our analysis on the AndroidLocker ransomware which just locks the screen without encrypting the files.
Infection Cycle
Before installation the app requests for the following permissions:
- internet (full internet access)
- access_network_state (access information about networks)
- read_phone_state
- receive_boot_complete
- wake_lock
- write_external_storage [Used for file encryption]
- read_external_storage [Used for file encryption]
Upon installation the app appears in the app drawer as sex xonix

Once the user opens the app the following message covers the screen:

This ransom message is in Russian and can be roughly translated to:

Subsequently if the user goes to the home screen and opens any other app he is greeted with the same ransom message thereby crippling the normal phone usage.
The malware encrypts the user files such as images, videos, and documents stored on the SD card:
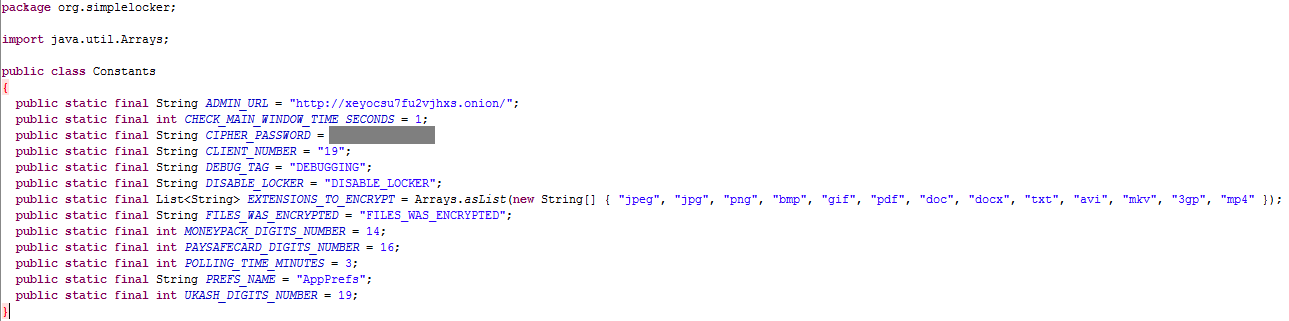
Files stored on the SD card before and after encryption:
The Command and Control server is hosted on a TOR .onion domain for the purpose of protection and anonymity.

It steals the device information and contacts its Command & Control server for further commands, possibly decrypting the files after ransom is paid.

It is possible to decrypt the files which are encrypted by the malware using the cipher key embedded in the malware code. We may see other Cryptolocker-like variants for Android which might be impossible to crack. Users should be extremely cautious while downloading apps from unfamiliar sites and only install apps from trusted sources.
Dell SonicWALL Gateway AntiVirus provides protection against this threat with the following signature:
- GAV: AndroidOS.Simplocker.A (Trojan)



