Yet another attack targeting Java vulnerability CVE-2013-2465 (Feb 5, 2014)
Dell SonicWALL threat research team has observed another live malware exploiting CVE-2013-2465 in the wild. The vulnerability allows remote attackers to bypass the Java sandbox via vectors related to “Incorrect image channel verification” in 2D.
When a victim is lured to visit malicious website http://sxxxxxxxxxxxxxxxx.br, the browser will download obfuscated javascripts, for example:

De-obfuscated javascript looks like:

, which determines JRE version. Other javascripts utilize different functions and eventually different malicious files got downloaded according to configuration of the victim’s machine.
We’ve analyzed the downloaded jnlp file and Java applet. The jnlp file itself is leveraging another exploit, Unsigned Applet Restriction Bypass Weakness, which bypass Java security warning. This flaw is fixed with Java 1.7.21 update.
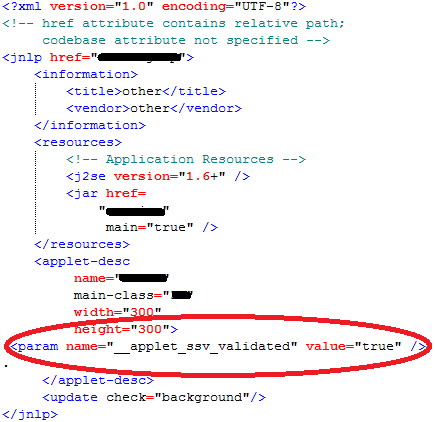
The Java applet is highly obfuscated too:

It first tries to exploit the vulnerability in SinglePixelPackedSampleModel. The decompiled code looks like:
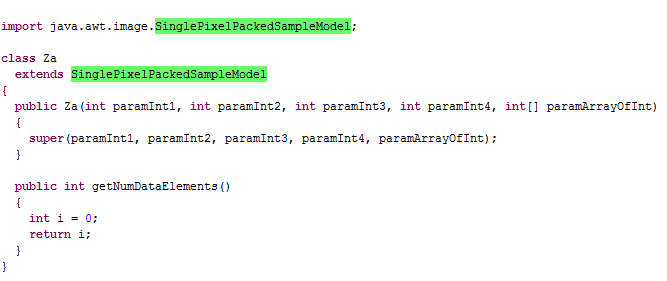
Successful exploit will set SetSecurityManager null.

Then it tries to download copy.exe.

In the end, copy.exe got executed by calling:
rundll32 url.dll,FileProtocolHandler “C:\DOCUME~1\USERNAME\LOCALS~1\Temp\Copy.exe”
Dell SonicWALL has released several signatures to detect and block specific exploitation attempts targeting this vulnerability. The signatures are listed below:
- Anti-SPY: Malformed-File class.TL.39
- GAV: Malformed.class.MT.3
- GAV: Malformed.jar.TL.4
- GAV: Malformed.jar.TL.5
- GAV: Pakes.ADDS




