Internet Explorer Vulnerability(MS12-043) Exploited in the Wild (August 30, 2013)
Dell Sonicwall Threats Research team has found multiple instances of malicious websites exploiting this old Internet Explorer Vulnerability. This vulnerability is already patched and has been assigned CVE-2012-1889. Metasploit also has a module msxml_get_definition_code_exec and we can see some similarities in the exploit code as outlined below.
There is obfuscation, heap allocation and shellcode setup. 


Vulnerable “MSXML3” control is included followed by its function call “definition” that triggers the condition.


Debugging shows heap spray and download of the url containing malicious executable.
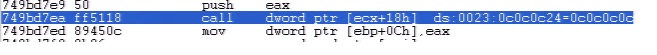


A separate variant uses IP address for executable download

We detect multiple variants of this attack by following IPS signatures
- 7967 Microsoft XML Core Services Uninitialized Object Access 1
- 8007 Microsoft XML Core Services Uninitialized Object Access 6
- 7610 HTTP Client Shellcode Exploit 68b
- 7370 HTTP Client Shellcode Exploit 68a
- 5416 HTTP Client Shellcode Exploit 15a
- 4604 HTTP Client Shellcode Exploit 1a
- 4605 HTTP Client Shellcode Exploit 2



