New Spambot Trojan with Backdoor functionality (July 12, 2013)
The Dell SonicWALL Threats Research team has come across a new family of spam bot Trojan with backdoor functionality. The spambot checks the reputation of the victim machine’s public IP address on various Real-time Blacklists (RBLs) before sending out the spam e-mails.
Infection Cycle:
Upon execution, the Trojan first attempts to start itself like a normal service executable. However, this fails for the first time as the service is not yet registered. It then proceeds to register itself as a service named as Sshdaemon. If the service installation fails then it will create a Registry run key with ValueName as falcon. If the service installation is successful it starts the service by executing the command cmd.exe /c net start Sshdaemon.
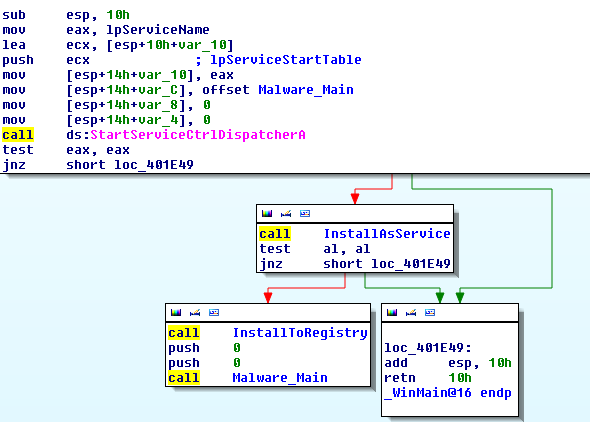
Once the Malware_Main is reached, it opens a backdoor on TCP port 1024 on the victim machine. It also uses the SSDP protocol to discover any available UPNP rootdevice. If a device of Internet Gateway Device UPNP profile is found it attempts to open the port through that device via WANIPConnection or WANPPPConnection subprofile whichever is supported.

It creates a registry entry to save a unique id hard coded within the malware code:

Below is the list of the C&C servers that the Trojan attempts to contact:
- 124.217.229.121
- despicableu.com
- basaltblock.com
- donfinale.com
- soulpick.org
- eldivision.net
The Trojan encrypts the following data and sends it to the servers listed above until one of them responds:

The C&C server responds back with the configuration for connecting to a spam server:

The Trojan checks the victim’s public IP address against popular Real-time Blacklists (RBLs) and if clean, it subsequently connects to the spam server to obtain a list of hosts and spam e-mail templates. It then proceeds to send out the spam e-mails.

Dell SonicWALL Gateway AntiVirus provides protection against this threat via the following signatures:
- GAV: Kryptik.BEWH (Trojan)




