MSN Messenger Trojan (May 01, 2009)
SonicWALL UTM Research team discovered a new MSN Messenger based threat starting April 29, 2009. There are 2 types of IM threats: those that arrive through “send a file” functionality of the instant messaging client, and those that arrive through link-spamming. This attack is of the latter type, as it arrives in form of links via MSN messenger messages pretending to be pointing to image files.
Sample MSN instant message looks like:
- Your foto on facebook?? http://facebook-images(removed)/view.php?=(your msn account address)
- You saw this pic?? http://64.32.16.99/images.php?id=(your msn account address)
It performs the following activity on the victim machine:
- Drops two files (Temporary Folder)IXP000.TMPmsns.exe and (Windows Directory)msnmsgrs.exe [detected as GAV: IRCBot.IUN (Trojan)]
- It adds the following Registry key to ensure that msnmsgrs.exe file starts every time on system reboot:
- HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionRunWindows UDP Control Center = “msnmsgrs.exe”
- It creates a mutex object – hidpower, to mark its presence on the system
- It tries to connect to the next.hi5photos.mobi domain on TCP port 8080
The screenshots of the sample messages are shown below:
SAMPLE MESSAGE #1

SAMPLE MESSAGE #2

If the user clicks on the link, it downloads the malware executable file that has an icon disguised as a JPEG image file and it looks like this:
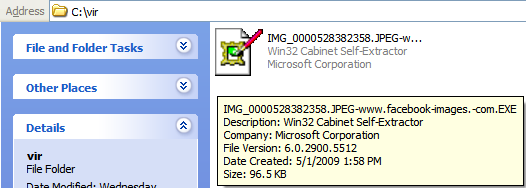
When the user tries to open the file, it opens up the following windows dialog box saying Picture can not be displayed:

The Trojan is also known as Virus.Win32.Trojan [Ikarus], BackDoor.IRC.Wisdom [DrWeb], and Win32:Trojan-gen [Avast]
SonicWALL Gateway AntiVirus provides protection against this malware via GAV: IRCBot.EMSN (Trojan) signature.



