Flash ads hijack cliboard (Aug 21, 2008)
August 21, 2008
In the Web attacks, which affect Mac, Windows, and Linux users running Firefox, IE, and Safari, bad guys are seizing control of the machine’s clipboard. This is a clever new way to spread malware. If someone replies to an e-mail, they may paste from the clipboard, and get the URL. Likewise with blog posts, social-networking sites, anywhere you paste.
Flash banner ads are using ActionScript code to load (persistently) a malicious URL into a target clipboard. They may be using the Flash command setClipboard. The Flash9b.ocx module is used to parse the file. A number of legitimate sites have been seen to host ads carrying the attack: including Newsweek, Digg, and MSNBC.com.
The URL points to a fake anti-virus program. So-called rogue security programs either make bogus claims that the user’s machine is infected with malware in an attempt to dupe people into buying the software, or in some cases, downloads malware rather than real antivirus software.
The particular variant used in this attack is FakeAlert.TY which we have alerted on July 18, 2008. SonicWALL blocks this attack proactively with GAV: Fakealert.TY (Trojan) signature.
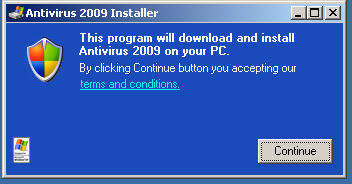
We have also released a signature for a variant of the Flash copy-paste exploit – GAV: SWF.CB (Exploit). SonicWALL UTM Research Team is still monitoring for new variants of these attacks and will research them as soon as they appear.



