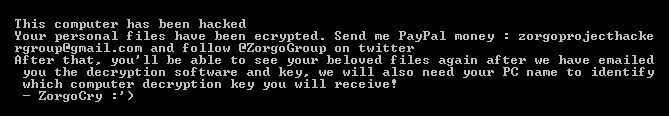
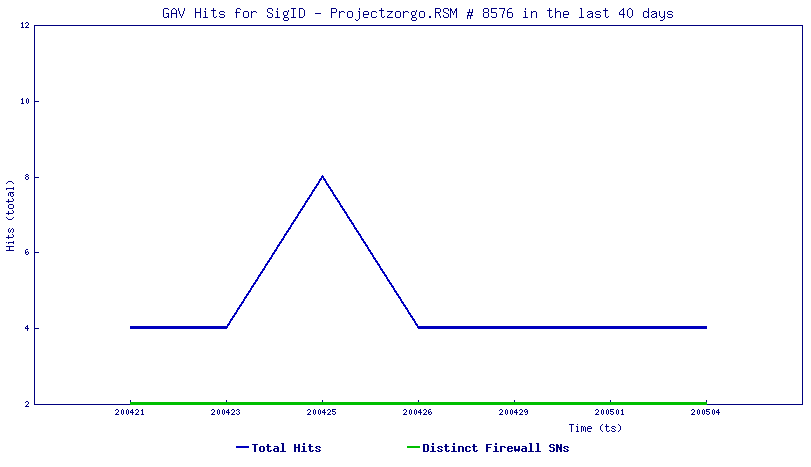
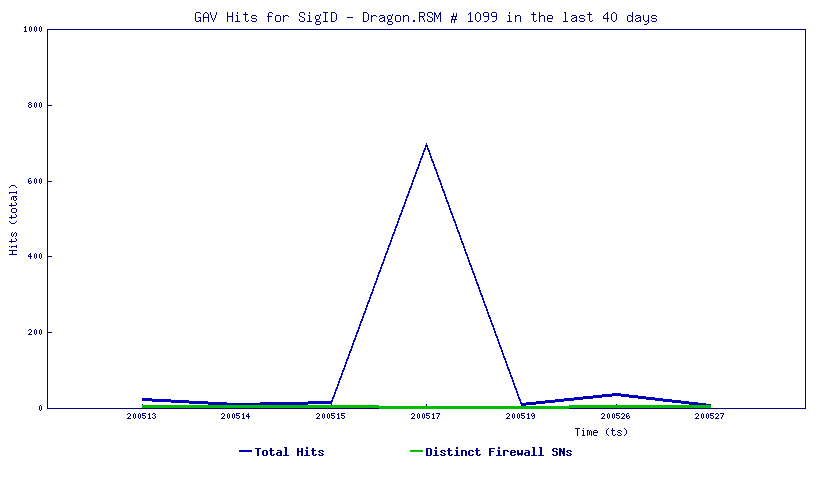
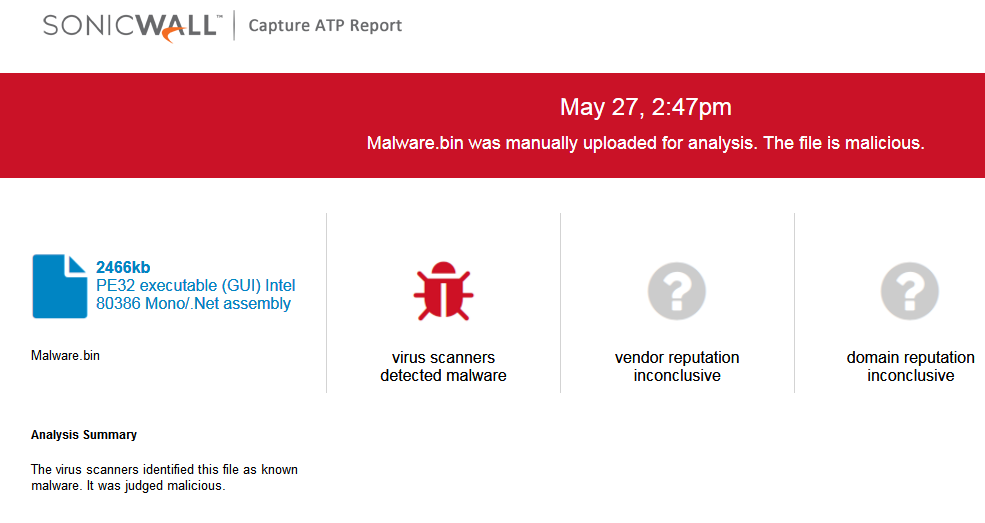
“One size fits all.” It’s a nice idea, isn’t it?
For ties and wristwatches, maybe.
For just about everything else, “one size fits all” is simply a nice way of saying “tailored for no one” — especially when it comes to cybersecurity bundles. With all the different tools, services, options and solutions that can go into a bundle, what are the odds that the bundles being offered will fit your particular business needs?
In the end, you often wind up with something you hadn’t planned to buy, or maybe didn’t even need, just to get a good deal. But if you’re forced to buy something you can’t use, are you actually saving money?
Imagine if you had the option to specify what you’d like to bundle together. How often would you opt for the pre-packaged bundle, if you had the option not to?
Traditional bundles offer two options: Take it, or leave it. But business needs — and use cases — are more complex than ever before. Organizations are now protecting a boundless workforce, with boundless exposure points. So why should your cybersecurity packages box you in?
That’s why SonicWall is introducing the limited-time Boundless Cybersecurity Bundle promotion. What’s in it? Whatever you’d like, with just a couple of conditions. Regardless of your use case, you can take only what you need, and none of what you don’t.
Best of all, the more you buy, the more you save. Purchase a qualifying product, including any firewall (or virtual firewall) with Advanced Gateway Security Services (AGSS), any Secure Mobile Access (SMA/SMAv), or a four- or eight-pack of wireless access points, and receive incremental discounts on each different solution added to that transaction, up to five total.
By leveraging SonicWall’s disruptive economics, you’ll get security tailored to your needs, all at a lower price than if you’d purchased each solution separately.
Whether you’re trying to comply with HIPAA, PCI-DSS, FIPS or other regulations; extend wireless across a construction site; protect a utility from ransomware; give remote employees access to key business data; or implement web filtering (CIPA) for elementary students, there’s a set of SonicWall products, services and solutions to fit your needs.
Your Boundless Cybersecurity Bundle is specific to you, and specific to your business use cases, because you built it from the ground up. And each is backed by SonicWall’s nearly three decades of experience securing businesses of all sizes against the most advanced and sophisticated cyberattacks.
So you get a customized solution and lower total cost of ownership, all from a company that nearly 500,000 organizations already trust with their cybersecurity needs.
To start building your Boundless Bundle, contact SonicWall or your partner.
Promotion begins June 3, 2020, and ends July 31, 2020, and is only available for purchases in NOAM and EMEA. In EMEA, only registered deals qualify for this promotion. This promotional offering may not be combined with any other sale, promotion, discount, rebate, coupon, or offering nor may it be used in conjunction with stock rotations. Discounts may vary depending on participation in programs offered by SonicWall and will be applied to only one solution per purchase transaction per end user customer during the promotion period. SonicWall’s MSRP will be used to calculate the final purchase price. A qualifying product must be purchased with one of the additional products listed. The qualifying product chosen must be different from the additional products chosen. The solution must be created to meet an end user customer’s request and must be reasonable for the end users intended use (e.g. meet the end customer’s intended licensed seat usage). Incremental discounts increase only as qualifying products that are different from each other are added to the solution. Proposed solutions and discounts granted are at SonicWall’s sole discretion. Only purchases of products that the end customer has not previously purchased qualify for the promotion. The purchase of qualifying physical or virtual firewalls must include one (1) year of the SonicWall Advanced Gateway Security Suite (AGSS). Additional terms and conditions may apply. All end user customer purchases are subject to the term and condition located at: www.sonicwall.com/legal. SonicWall is not responsible errors or omissions nor for the acts or omissions of any third party. This offer may be modified, discontinued or terminated by SonicWall at any time without notice.