Critical CyberPanel Vulnerability (CVE-2024-51378): How to Stay Protected

Overview
The SonicWall Capture Labs threat research team became aware of CVE-2024-51378, assessed its impact and developed mitigation measures for the vulnerability. CVE-2024-51378 is a critical vulnerability with a CVSS score of 9.8 in CyberPanel versions 2.3.6 and 2.3.7 that allows unauthenticated remote code execution (RCE). Threat actors, including the PSAUX ransomware group, have been reported exploiting this vulnerability to encrypt server files and deploy ransomware payloads. A public proof of concept is available. The exploitation of CVE-2024-51378 has led to the compromise of numerous CyberPanel instances worldwide with a significant concentration in the United States. Successful attacks result in full server control, unauthorized access to sensitive domains and potential data breaches. Users of affected CyberPanel versions are strongly advised to update to the latest version to mitigate these risks.
Technical Overview
Attackers can exploit this flaw to gain root-level access by sending crafted OPTIONS HTTP requests to /dns/getresetstatus and /ftp/getresetstatus endpoints located in dns/views.py and ftp/views.py. This is possible due to a lack of proper input validation. As a result, an attacker can break out of the intended code path by using a “;” and execute a command of their choosing without authenticating to the server.
Triggering the Vulnerability
- Make an initial GET request to the root (/) endpoint.
- Retrieve the CSRF token from the response of the get request.
- Construct an HTTP OPTIONS request with the headers X-CSRFToken, Content-Type, and Referer fields.
- Create a malicious payload that injects a command into the “status file” parameter using a semicolon within the parameter's value followed by a Linux command. The semicolon allows arbitrary shell commands to be executed on the server.
- Send the payload via an OPTIONS request to either “/dns/getresetstatus” or “/ftp/getresetstatus” endpoint. The result of the command may be returned in the “requestStatus” field of the JSON response
Exploitation
Using the publicly available PoC, it is possible to see an example of the malicious request (Figure 1).
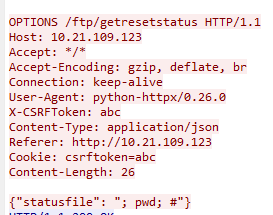
Figure 1: Malicious request
Exploitation occurs in the “status file” parameter sent within the JSON section of the request. In this instance, the “pwd” command will be executed, and the result will be returned to the attacker. A more likely attack would be a command to allow the attacker to download malware such as the use of a “wget” command, followed by a second request to execute the downloaded malware.
SonicWall Protections
To ensure SonicWall customers are prepared for any exploitation that may occur due to this vulnerability, the following signatures have been released:
- IPS:18890 CyberPanel getresetstatus Remote Command Execution
Remediation Recommendations
It is highly recommended to update to a patched version of CyberPanel where input validation and endpoint authentication have been increased. If unable to update immediately, it is suggested to monitor for unusual commands in the system logs for HTTP requests to /api/getresetstatus/ or/dns/getresetstatus.
Relevant Links
- https://github.com/refr4g/CVE-2024-51378/tree/main
- https://thecyberthrone.in/2024/10/30/psaux-ransomware-exploits-cyberpanel-vulnerabilities/
- https://dreyand.rs/code/review/2024/10/27/what-are-my-options-cyberpanel-v236-pre-auth-rce
- https://nvd.nist.gov/vuln/detail/CVE-2024-51378
Share This Article

An Article By
An Article By
Security News
Security News