A Look Into Embargo Ransomware, Another Rust-based Ransomware

Embargo is a relatively new ransomware group that emerged in 2024. This group is known for using Rust-based malware and operating under a ransomware-as-a-service (Raas) model. Like many modern ransomware groups, Embargo employs double extortion tactics where they first exfiltrate sensitive data from their victims before encrypting their files. They then threaten to release the stolen data unless a ransom Is paid.
Infection Cycle
This ransomware uses an executable written in Rust. Examining its strings will show references to multitude of Rust libraries and crates used.
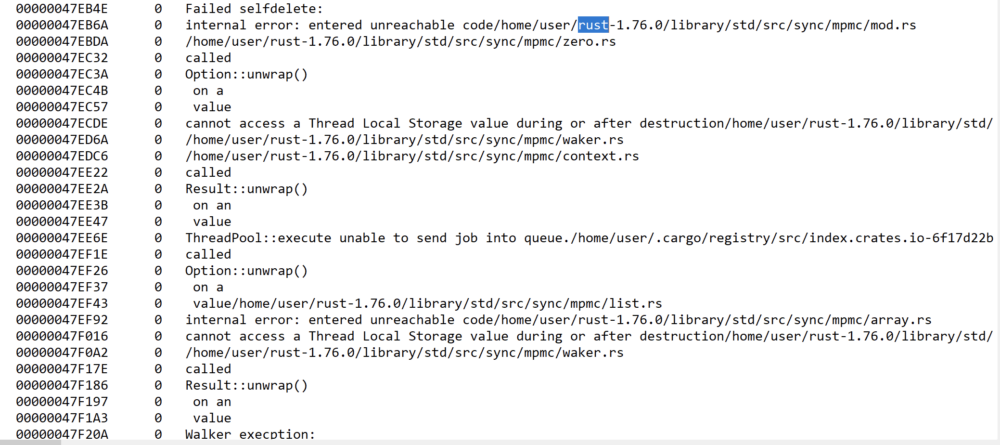
Figure 1: Rust libraries and crates referenced in its strings
Here are some of the notable Rust crates used by this ransomware that will help understand its functionality:
- Clap_builder – command line argument parser
- Humantime – parser and formatter for durations and timestamps
- Log4rs – crate used for output logging
- Ignore – file/directory iterator; can be used to automatically filter out files and directories according to ignore globs
- Zeroize- Securely clear secrets from memory
- Winapi-util-0.1.6/src/sysinfo.rs - routines for querying various Windows specific properties such as Computer Name
- Chacha20 – Rust implementation of the ChaCha20 Stream Cipher, 256-bit stream cipher used to encrypt and decrypt data
This ransomware uses command line options as shown in the figure below.
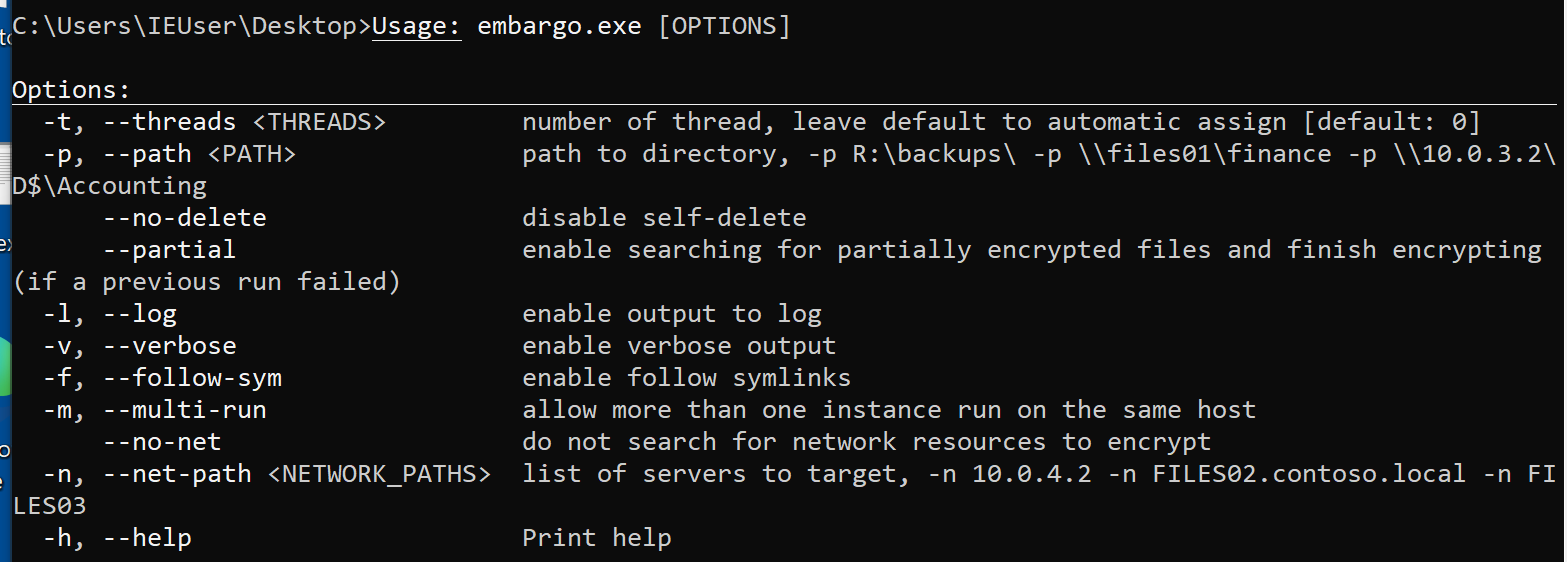
Figure 2: Embargo ransomware command line options
Executing this malware with the option for logging will create a log file showing every single file being successfully encrypted along with errors during runtime.
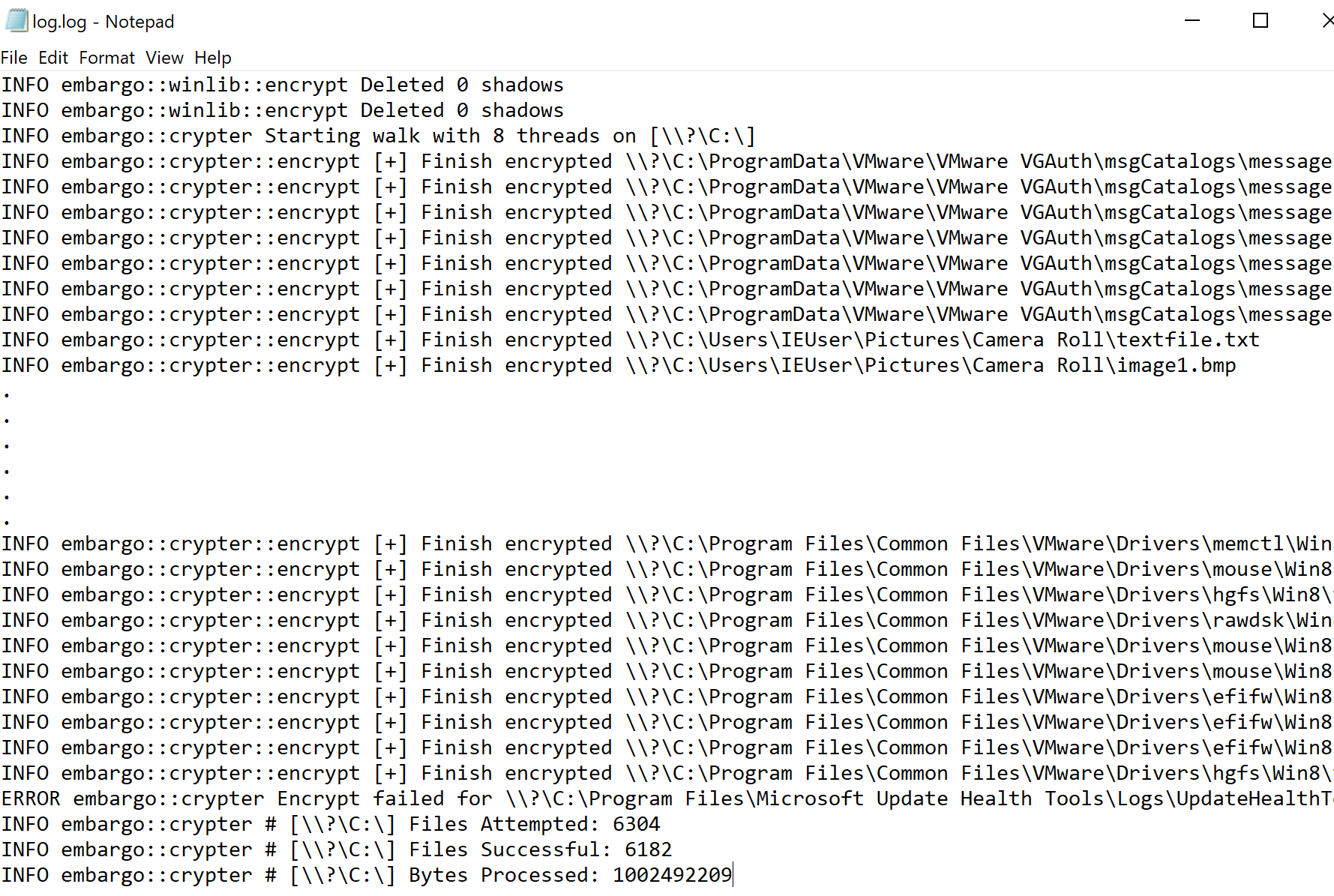
Figure 3: Runtime execution logging output to a file
Upon successful execution, encrypted files will be appended with random digits and a ransom note can be found in every directory where files have been encrypted.
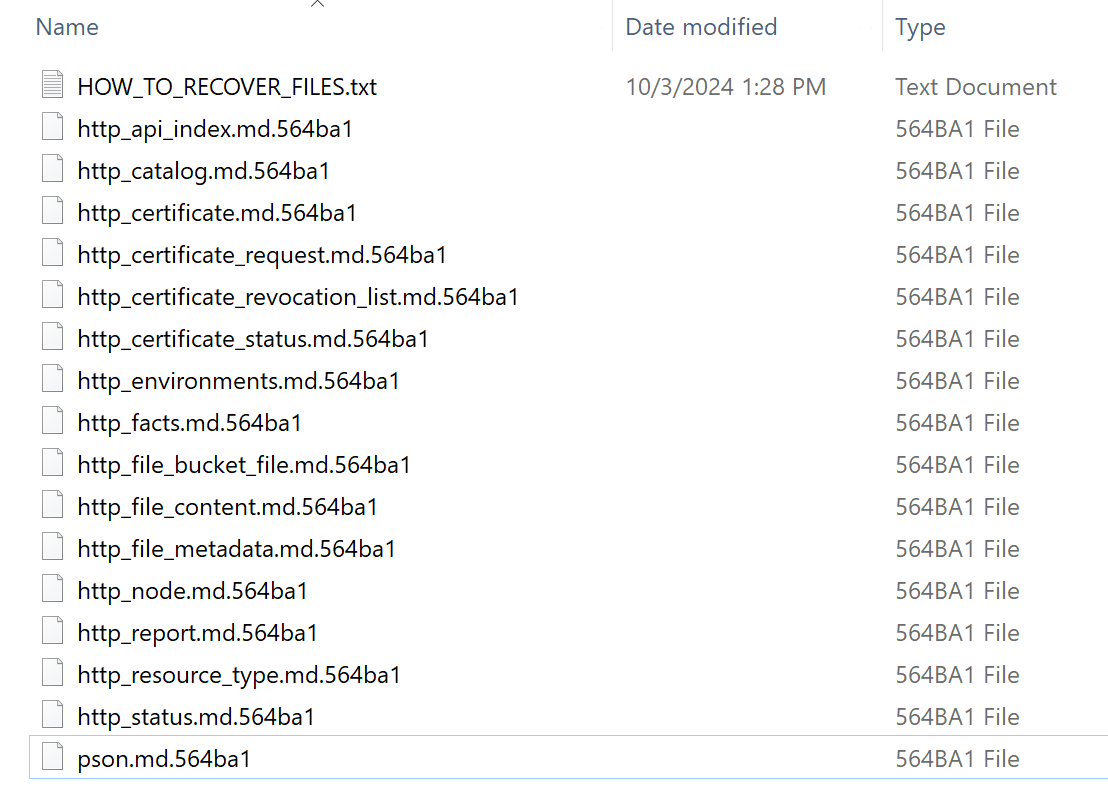
Figure 4: Example of encrypted files within a directory
The ransom note will show instructions on how to recover files along with a threat that all sensitive data will be posted on their blog site.
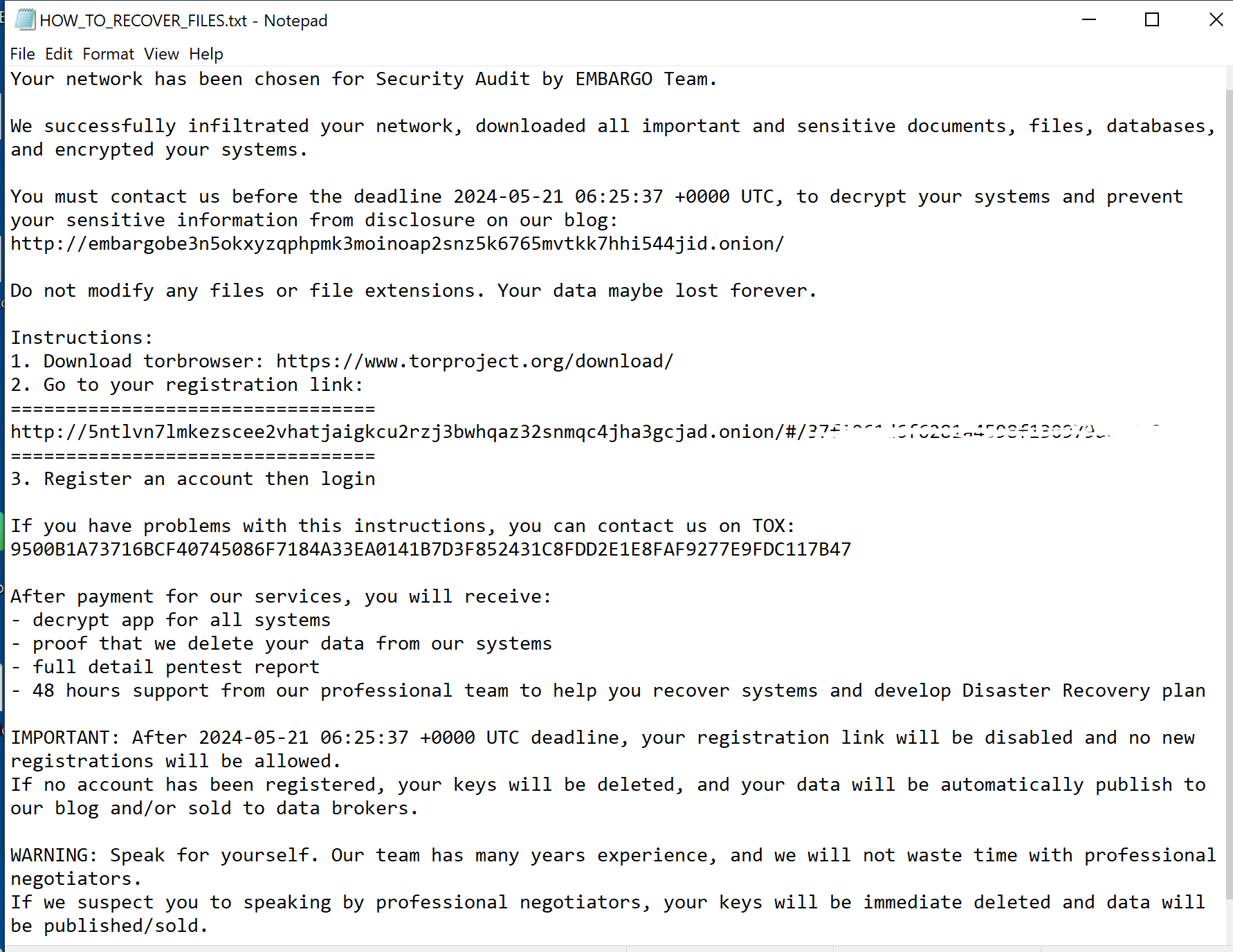
Figure 5: Embargo ransom note
Embargo have targeted various organizations. Their blog on the onion network lists some of the victims that have allegedly not paid the ransom for which their data are now available to the public.
 Figure 6: Embargo website on the Onion network accessible using a Tor browser
Figure 6: Embargo website on the Onion network accessible using a Tor browser
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: Embargo.RSM(Trojan)
This threat is also detected by SonicWall Capture ATP w/RTDMI and the Capture Client endpoint solutions.
Share This Article

An Article By
An Article By
Security News
Security News