Understanding CVE-2024-38063: How SonicWall Prevents Exploitation

Contributing Researchers: Soumy Das and Hasib Vhora
Overview
CVE-2024-38063 is a critical remote code execution vulnerability in Windows systems with the IPv6 stack, carrying a CVSS score of 9.8. This zero-click, wormable flaw allows attackers to execute arbitrary code remotely via specially crafted IPv6 packets, potentially leading to full system compromise. It affects Windows 10, Windows 11, and Windows Server systems. Microsoft has released patches to mitigate this vulnerability, and it is essential to apply these updates promptly to protect against exploitation. Given the critical nature of this vulnerability and its likely exploitation in the wild, SonicWall has proactively enhanced its firewall and RTDMI products with additional mitigations to protect systems, protecting cases where the patch has not yet been applied.
A Chinese researcher from Cyber KunLun discovered the vulnerability and publicly disclosed by Microsoft in its August 2024 Patch Tuesday release. Due to the simplicity with which an exploit could be crafted, Microsoft has urged users to apply the available patches immediately. Some security experts have incorrectly advised disabling IPv6. While Microsoft clarifies that disabling IPv6 can mitigate the vulnerability, it is not recommended due to potential issues with Windows functionality. Instead, Microsoft advises patching systems immediately.
SonicWall Protections
The SonicWall firewall protects against CVE-2024-38063 by blocking malicious IPv6 fragmented packets by default. This will still occur regardless of whether additional security services are configured, including if deep packet inspection (DPI) is enabled or disabled or if the firewall is configured to allow smaller IPv6 packets. The firewall drops the critical packet involved in the exploit due to its fragment reassembly logic, which ensures that the packet never reaches the victim machine. If an exploitation attempt is made, a log may be created depending on the firewall’s configuration showing “IPv6 fragment was dropped”.
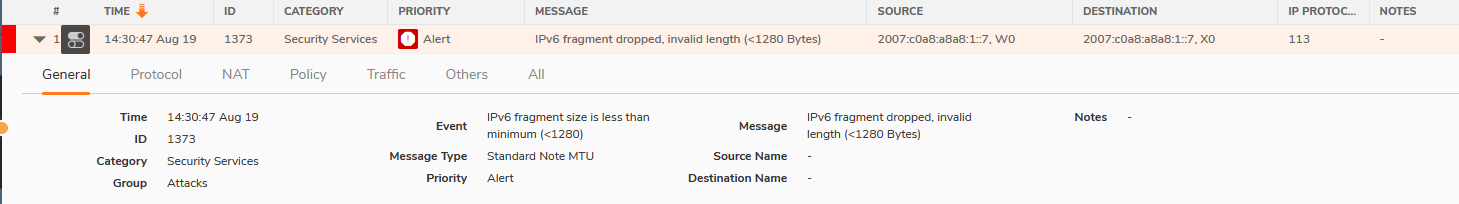
Given the wormable nature of this vulnerability, there is a risk that it could be embedded in binaries sent over the network for later exploitation. We've strengthened our RTDMI sandboxing solution to safeguard our customers to detect and block Windows or Linux binaries carrying this exploit. This added layer of protection is crucial for identifying and preventing lateral movement and post-exploitation activities by threat actors, ensuring robust security even if some systems remain unpatched.
The Patch
By doing basic patch diffing with the help of Diaphora on the old and new versions of the tcpip.sys driver within Microsoft Windows, it is possible to determine the patch was added to the Ipv6pProcessOptions function.
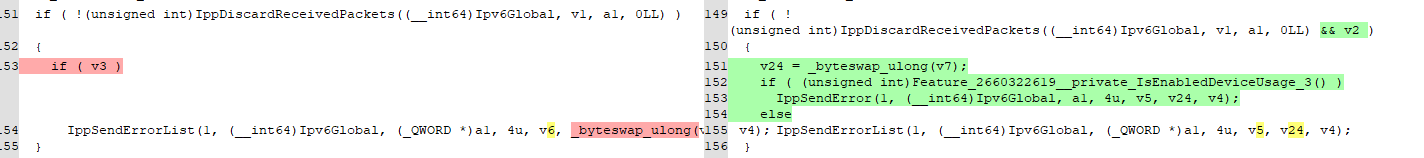
The additional, conditional logic in the updated version introduces checks before executing IppSendErrorList. The vulnerability takes advantage of an out-of-bound write (OOB) by sending malformed Ipv6 packets. It forces packets to be written to an error list called IppSendErrorList to obtain the correct conditions. The new checks only add packets to the list after the data is validated. Otherwise, it only sends an error without adding the packets to the list memory structure. The patch prevents unintended behavior or exploitation by ensuring that the functions `IppSendError` or `IppSendErrorList` are only called under appropriate conditions, reducing the risk of incorrect or malicious data being processed. This indicates that the vulnerable code likely still exists but is more complicated or potentially impossible to leverage.
Share This Article

An Article By
An Article By
Douglas McKee
Douglas McKee