Microsoft Security Bulletin Coverage For August 2024

Overview
Microsoft’s 2024 Patch Tuesday has 87 vulnerabilities, 36 of which are Elevation of Privilege vulnerabilities. The SonicWall Capture Labs threat research team has analyzed and addressed Microsoft’s security advisories for the month of 2024 and has produced coverage for ten of the reported vulnerabilities
Vulnerabilities with Detections
| CVE | CVE Title | Signature |
| CVE-2024-38106 | Windows Kernel Elevation of Privilege Vulnerability | ASPY 6995 Exploit-exe exe.MP_399 |
| CVE-2024-38125 | Kernel Streaming WOW Thunk Service Driver Elevation of Privilege Vulnerability | ASPY 6996 Exploit-exe exe.MP_400 |
| CVE-2024-38141 | Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability | ASPY 6997 Exploit-exe exe.MP_401 |
| CVE-2024-38144 | Kernel Streaming WOW Thunk Service Driver Elevation of Privilege Vulnerability | ASPY 6998 Exploit-exe exe.MP_402 |
| CVE-2024-38147 | Microsoft DWM Core Library Elevation of Privilege Vulnerability | ASPY 6999 Exploit-exe exe.MP_403 |
| CVE-2024-38148 | Windows Secure Channel Denial of Service Vulnerability | ASPY 593 Exploit-exe exe.MP_404 |
| CVE-2024-38150 | Windows DWM Core Library Elevation of Privilege Vulnerability | ASPY 594 Exploit-exe exe.MP_405 |
| CVE-2024-38178 | Scripting Engine Memory Corruption Vulnerability | IPS 4483 Scripting Engine Memory Corruption (CVE-2024-38178) |
| CVE-2024-38193 | Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability | ASPY 595 Exploit-exe exe.MP_406 |
| CVE-2024-38196 | Windows Common Log File System Driver Elevation of Privilege Vulnerability | ASPY 596 Exploit-exe exe.MP_407 |
| CVE-2024-38063 | Windows TCP/IP Remote Code Execution Vulnerability | RTDMI |
Release Breakdown
The vulnerabilities can be classified into following categories:
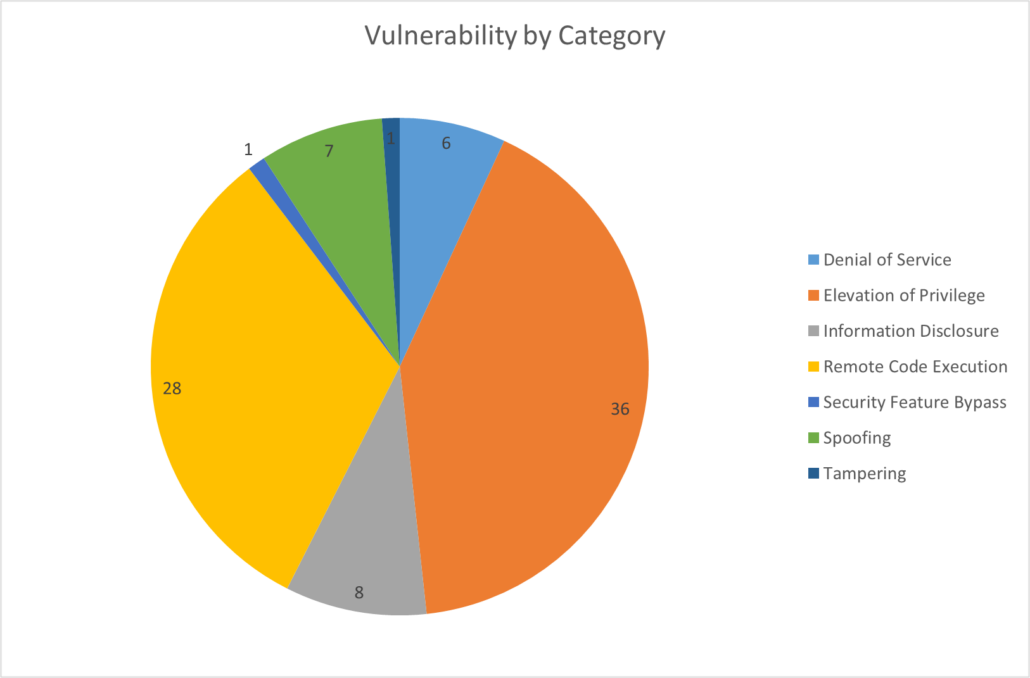
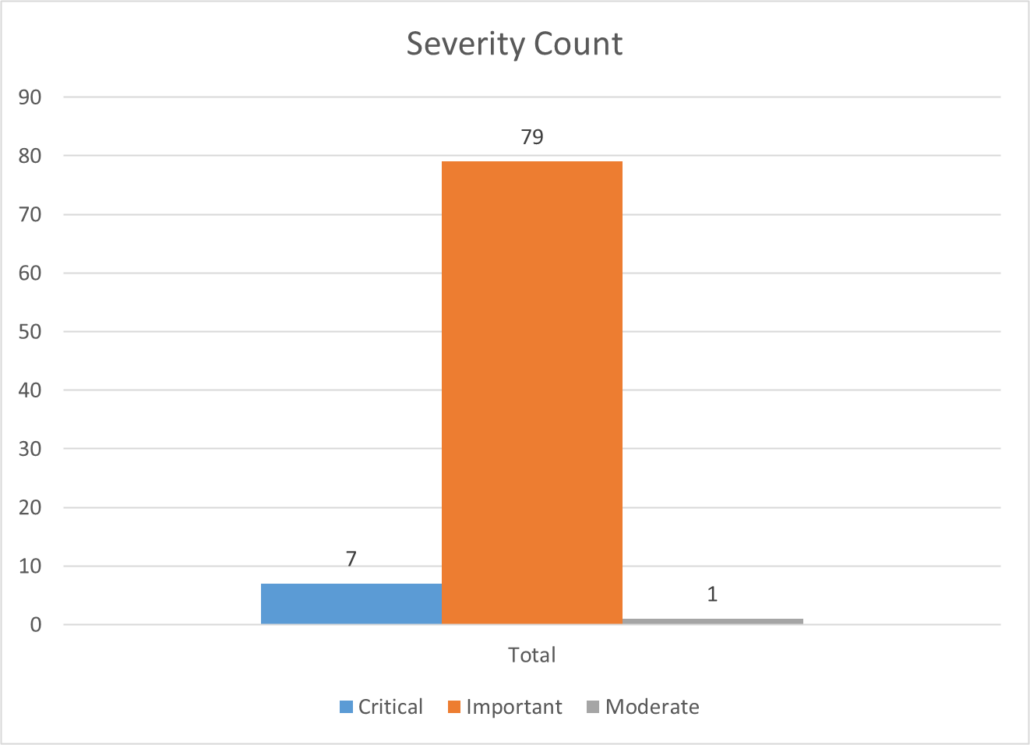
For August there are seven critical, 79 important and one moderate vulnerabilities.
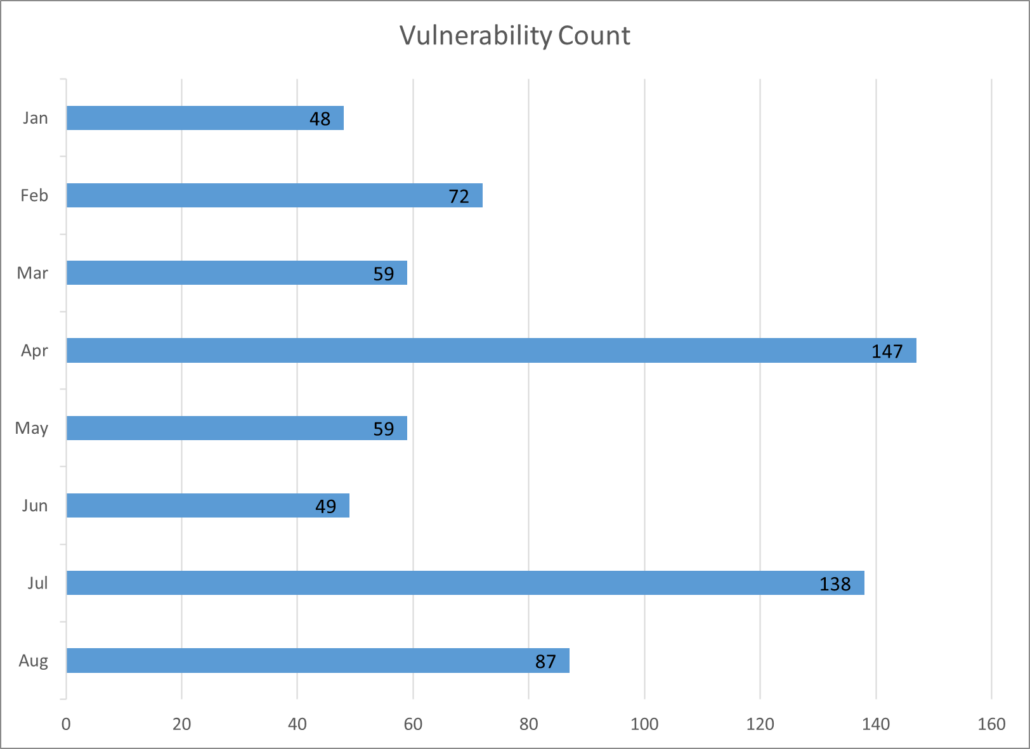
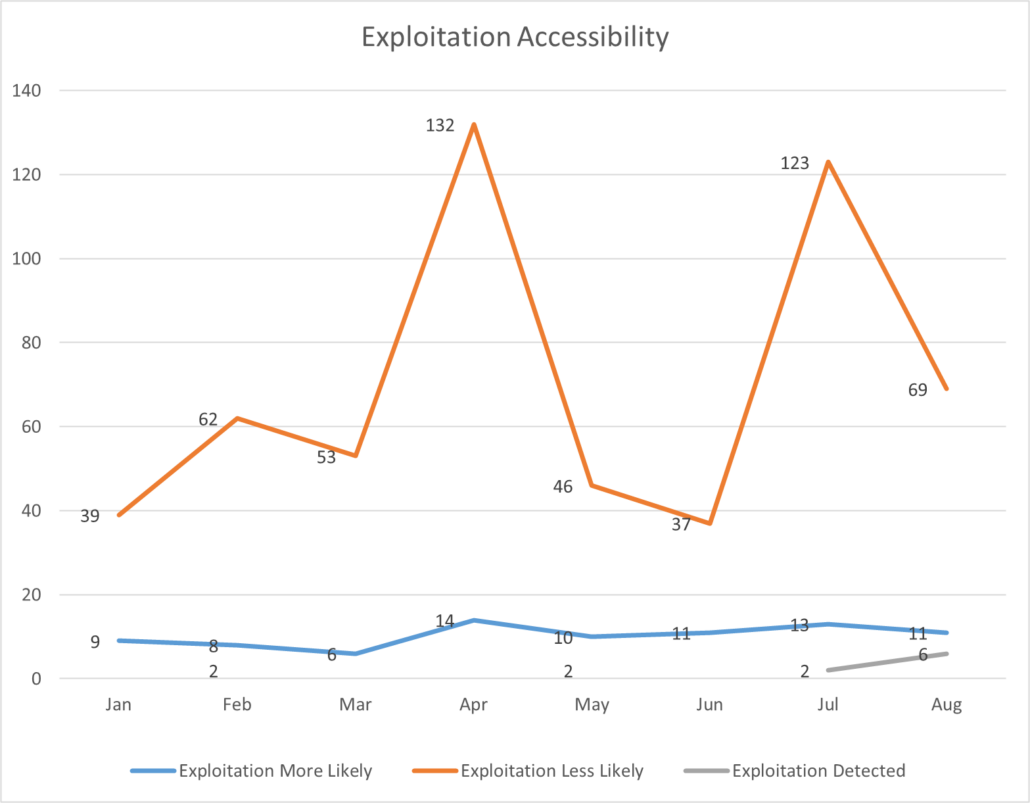
2024 Patch Tuesday Monthly Comparison
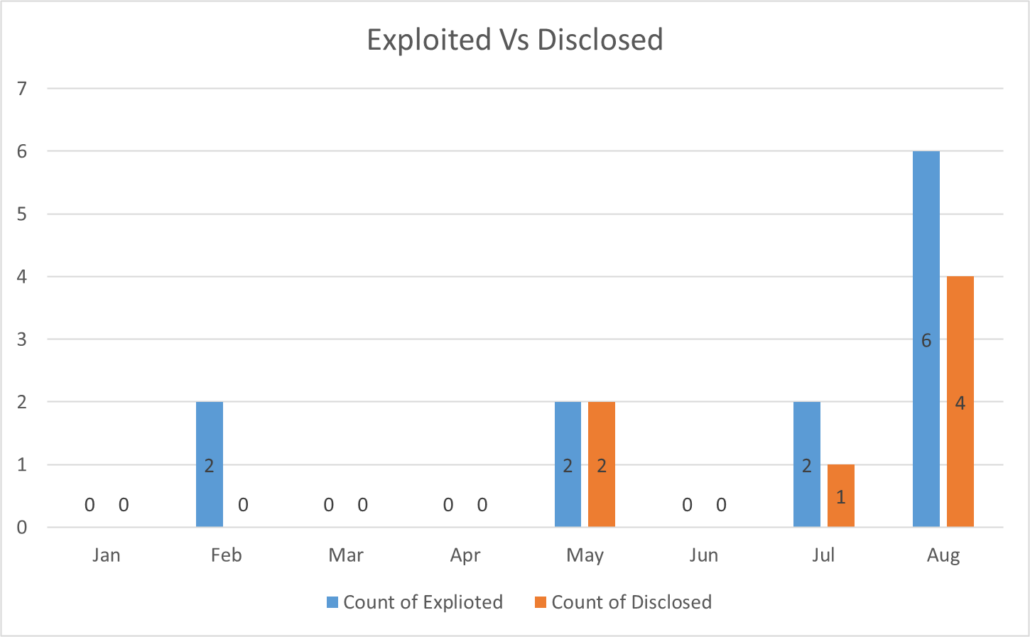
Microsoft tracks vulnerabilities that are being actively exploited at the time of discovery and those that have been disclosed publicly before the patch Tuesday release for each month. The above chart displays these metrics as seen each month.
Release Detailed Breakdown
Denial of Service Vulnerabilities
| CVE | CVE Title |
| CVE-2024-38126 | Windows Network Address Translation (NAT) Denial of Service Vulnerability |
| CVE-2024-38132 | Windows Network Address Translation (NAT) Denial of Service Vulnerability |
| CVE-2024-38145 | Windows Layer-2 Bridge Network Driver Denial of Service Vulnerability |
| CVE-2024-38146 | Windows Layer-2 Bridge Network Driver Denial of Service Vulnerability |
| CVE-2024-38148 | Windows Secure Channel Denial of Service Vulnerability |
| CVE-2024-38168 | .NET and Visual Studio Denial of Service Vulnerability |
Elevation of Privilege Vulnerabilities
| CVE | CVE Title |
| CVE-2024-21302 | Windows Secure Kernel Mode Elevation of Privilege Vulnerability |
| CVE-2024-29995 | Windows Kerberos Elevation of Privilege Vulnerability |
| CVE-2024-38084 | Microsoft OfficePlus Elevation of Privilege Vulnerability |
| CVE-2024-38098 | Azure Connected Machine Agent Elevation of Privilege Vulnerability |
| CVE-2024-38106 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-38107 | Windows Power Dependency Coordinator Elevation of Privilege Vulnerability |
| CVE-2024-38109 | Azure Health Bot Elevation of Privilege Vulnerability |
| CVE-2024-38117 | NTFS Elevation of Privilege Vulnerability |
| CVE-2024-38125 | Kernel Streaming WOW Thunk Service Driver Elevation of Privilege Vulnerability |
| CVE-2024-38127 | Windows Hyper-V Elevation of Privilege Vulnerability |
| CVE-2024-38133 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-38134 | Kernel Streaming WOW Thunk Service Driver Elevation of Privilege Vulnerability |
| CVE-2024-38135 | Windows Resilient File System (ReFS) Elevation of Privilege Vulnerability |
| CVE-2024-38136 | Windows Resource Manager PSM Service Extension Elevation of Privilege Vulnerability |
| CVE-2024-38137 | Windows Resource Manager PSM Service Extension Elevation of Privilege Vulnerability |
| CVE-2024-38141 | Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability |
| CVE-2024-38142 | Windows Secure Kernel Mode Elevation of Privilege Vulnerability |
| CVE-2024-38143 | Windows WLAN AutoConfig Service Elevation of Privilege Vulnerability |
| CVE-2024-38144 | Kernel Streaming WOW Thunk Service Driver Elevation of Privilege Vulnerability |
| CVE-2024-38147 | Microsoft DWM Core Library Elevation of Privilege Vulnerability |
| CVE-2024-38150 | Windows DWM Core Library Elevation of Privilege Vulnerability |
| CVE-2024-38153 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-38162 | Azure Connected Machine Agent Elevation of Privilege Vulnerability |
| CVE-2024-38163 | Windows Update Stack Elevation of Privilege Vulnerability |
| CVE-2024-38184 | Windows Kernel-Mode Driver Elevation of Privilege Vulnerability |
| CVE-2024-38185 | Windows Kernel-Mode Driver Elevation of Privilege Vulnerability |
| CVE-2024-38186 | Windows Kernel-Mode Driver Elevation of Privilege Vulnerability |
| CVE-2024-38187 | Windows Kernel-Mode Driver Elevation of Privilege Vulnerability |
| CVE-2024-38191 | Kernel Streaming Service Driver Elevation of Privilege Vulnerability |
| CVE-2024-38193 | Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability |
| CVE-2024-38196 | Windows Common Log File System Driver Elevation of Privilege Vulnerability |
| CVE-2024-38198 | Windows Print Spooler Elevation of Privilege Vulnerability |
| CVE-2024-38201 | Azure Stack Hub Elevation of Privilege Vulnerability |
| CVE-2024-38202 | Windows Update Stack Elevation of Privilege Vulnerability |
| CVE-2024-38215 | Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability |
| CVE-2024-38223 | Windows Initial Machine Configuration Elevation of Privilege Vulnerability |
Information Disclosure Vulnerabilities
| CVE | CVE Title |
| CVE-2024-38118 | Microsoft Local Security Authority (LSA) Server Information Disclosure Vulnerability |
| CVE-2024-38122 | Microsoft Local Security Authority (LSA) Server Information Disclosure Vulnerability |
| CVE-2024-38123 | Windows Bluetooth Driver Information Disclosure Vulnerability |
| CVE-2024-38151 | Windows Kernel Information Disclosure Vulnerability |
| CVE-2024-38155 | Security Center Broker Information Disclosure Vulnerability |
| CVE-2024-38167 | .NET and Visual Studio Information Disclosure Vulnerability |
| CVE-2024-38206 | Microsoft Copilot Studio Information Disclosure Vulnerability |
| CVE-2024-38214 | Windows Routing and Remote Access Service (RRAS) Information Disclosure Vulnerability |
Remote Code Execution Vulnerabilities
| CVE | CVE Title |
| CVE-2024-38063 | Windows TCP/IP Remote Code Execution Vulnerability |
| CVE-2024-38114 | Windows IP Routing Management Snapin Remote Code Execution Vulnerability |
| CVE-2024-38115 | Windows IP Routing Management Snapin Remote Code Execution Vulnerability |
| CVE-2024-38116 | Windows IP Routing Management Snapin Remote Code Execution Vulnerability |
| CVE-2024-38120 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-38121 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-38128 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-38130 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-38131 | Clipboard Virtual Channel Extension Remote Code Execution Vulnerability |
| CVE-2024-38138 | Windows Deployment Services Remote Code Execution Vulnerability |
| CVE-2024-38140 | Windows Reliable Multicast Transport Driver (RMCAST) Remote Code Execution Vulnerability |
| CVE-2024-38152 | Windows OLE Remote Code Execution Vulnerability |
| CVE-2024-38154 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-38157 | Azure IoT SDK Remote Code Execution Vulnerability |
| CVE-2024-38158 | Azure IoT SDK Remote Code Execution Vulnerability |
| CVE-2024-38159 | Windows Network Virtualization Remote Code Execution Vulnerability |
| CVE-2024-38160 | Windows Network Virtualization Remote Code Execution Vulnerability |
| CVE-2024-38161 | Windows Mobile Broadband Driver Remote Code Execution Vulnerability |
| CVE-2024-38169 | Microsoft Office Visio Remote Code Execution Vulnerability |
| CVE-2024-38170 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2024-38171 | Microsoft PowerPoint Remote Code Execution Vulnerability |
| CVE-2024-38172 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2024-38173 | Microsoft Outlook Remote Code Execution Vulnerability |
| CVE-2024-38178 | Scripting Engine Memory Corruption Vulnerability |
| CVE-2024-38180 | SmartScreen Prompt Remote Code Execution Vulnerability |
| CVE-2024-38189 | Microsoft Project Remote Code Execution Vulnerability |
| CVE-2024-38195 | Azure CycleCloud Remote Code Execution Vulnerability |
| CVE-2024-38199 | Windows Line Printer Daemon (LPD) Service Remote Code Execution Vulnerability |
Security Feature Bypass Vulnerability
| CVE | CVE Title |
| CVE-2024-38213 | Windows Mark of the Web Security Feature Bypass Vulnerability |
Spoofing Vulnerabilities
| CVE | CVE Title |
| CVE-2024-37968 | Windows DNS Spoofing Vulnerability |
| CVE-2024-38108 | Azure Stack Hub Spoofing Vulnerability |
| CVE-2024-38166 | Microsoft Dynamics 365 Cross-site Scripting Vulnerability |
| CVE-2024-38177 | Windows App Installer Spoofing Vulnerability |
| CVE-2024-38197 | Microsoft Teams for iOS Spoofing Vulnerability |
| CVE-2024-38200 | Microsoft Office Spoofing Vulnerability |
| CVE-2024-38211 | Microsoft Dynamics 365 (on-premises) Cross-site Scripting Vulnerability |
Tampering Vulnerability
| CVE | CVE Title |
| CVE-2024-38165 | Windows Compressed Folder Tampering Vulnerability |
Share This Article

An Article By
An Article By
Security News
Security News