CVE-2024-7928: FastAdmin Unauthenticated Path Traversal Vulnerability

Overview
The SonicWall Capture Labs threat research team became aware of an unauthenticated directory traversal vulnerability affecting FastAdmin installations. Identified as CVE-2024-7928 and with a moderate score of 5.3 CVSSv3, the vulnerability is more severe than it initially appears. Labeled as a path traversal vulnerability and categorized as CWE-22 – this vulnerability allows unauthenticated attackers to traverse the file system.
A proof of concept is publicly available on GitHub, affecting FastAdmin versions up to 1.3.3.20220121. An attacker could perform a path traversal on FastAdmin instances, retrieving database details and exposing sensitive information. Users are strongly encouraged to update to version 1.3.4.20220530.
Technical Overview
FastAdmin is an open-source backend framework based on two mainstream technologies: ThinkPHP and Bootstrap. It has powerful functions such as a complete permission management system and one-click CRUD generation. The CVE-2024–7928 PoC attempts to retrieve DB credentials for FastAdmin instances. This issue can be exploited remotely and could lead to unauthorized access to sensitive data, posing a risk to organizational security due to its low complexity and minimal privileges required for exploitation.
Figure 1 shows utilizing of the path traversal vulnerability by crafting a GET request to the /index/ajax/lang URI and manipulating the “lang” argument.
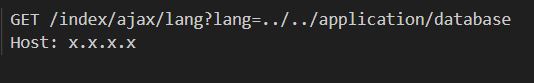
Figure 1: CVE-2024-7928 attack request
Exploiting the vulnerability
A crafted GET request to a vulnerable FastAdmin instance is necessary and sufficient to exploit the issue. An attacker only needs to be able to access the instance remotely, which could be over the Internet or a local network. A working PoC with a crafted GET request aids in exploiting this vulnerability. Figure 2 is a demonstration of exploitation leveraging the publicly available PoC.
Figure 2: CVE-2024-7928 Exploitation
Once the exploit is successful, an attacker can use stolen credentials with a MySQL utility tool to access, manipulate, and expose sensitive information, as shown in Figure 3.
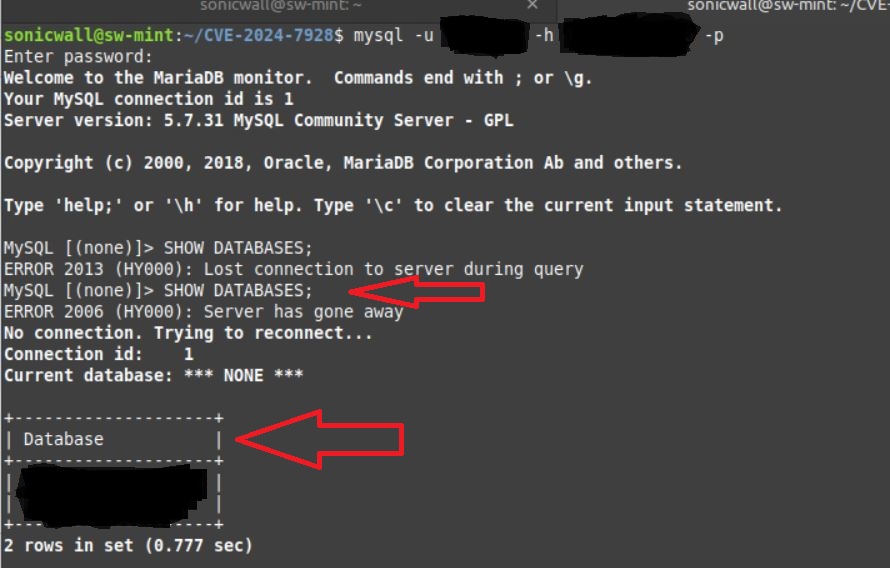
Figure 3: CVE-2024-7928 post exploitation
SonicWall Protections
To ensure SonicWall customers are prepared for any exploitation that may occur due to this vulnerability, the following signatures have been released:
- IPS:20259 – FastAdmin Path Traversal
Remediation Recommendations
According to the advisory, considering the severe consequences of this vulnerability and the trend of nefarious activists trying to leverage the exploit in the wild, users are strongly encouraged to upgrade their FastAdmin instances to version 1.3.4.20220530 to address the vulnerability.
Relevant Links
Share This Article

An Article By
An Article By
Security News
Security News