Critical Path Traversal Vulnerability in Check Point Security Gateways (CVE-2024-24919)

Overview
This week, the SonicWall Capture Labs Research team analyzed a sample of Linux ransomware. The group behind this ransomware, called INC Ransomware, has been active since it was first reported a year ago.
Infection Cycle
The malware is a Linux executable in ELF file format. A quick inspection of its strings revealed command-line arguments that can be passed to this ELF file.
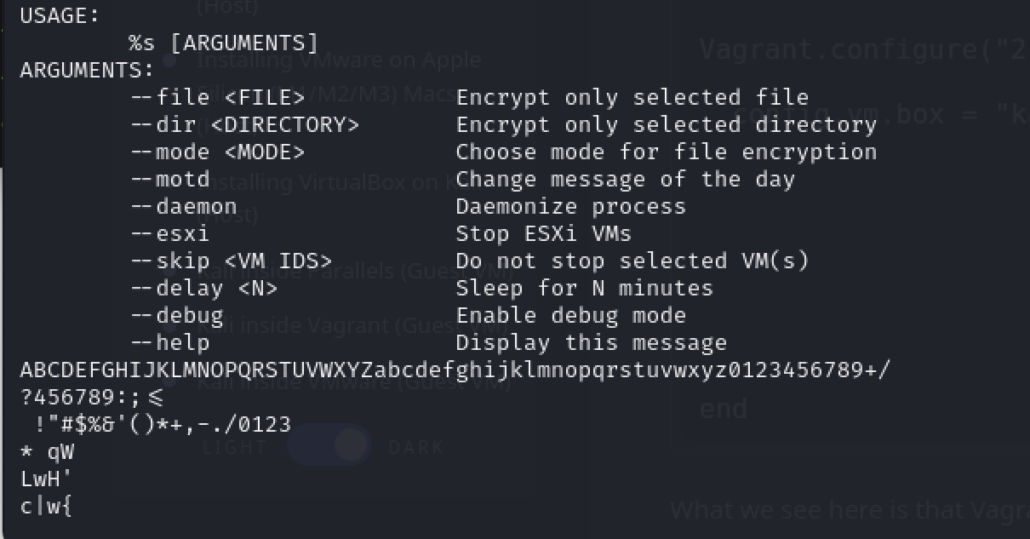
Figure 1: List of Command Line Arguments
Upon execution with the identified parameters, the malware appends “INC” to the names of encrypted files.

Figure 2: Debug Output Using the --debug Option
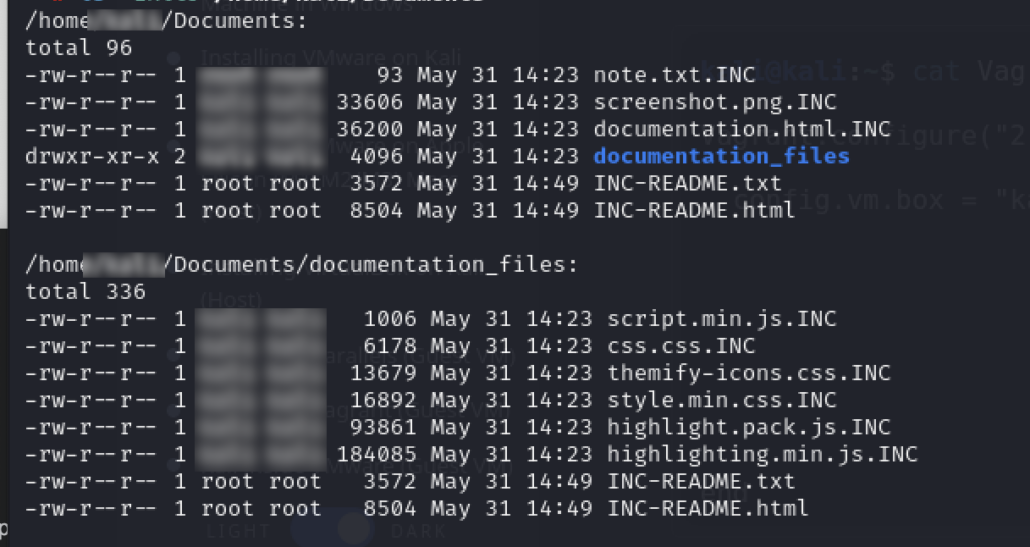
Figure 3: Encrypted files with “INC” appended file extension
The malware also creates a file named “kill,” a shell script using the esxcli utility available in VMWare ESXi to list and kill all virtual machine processes if running in an ESXi environment. Since our analysis was not conducted in such an environment, this command resulted in an error as the utility was not found.
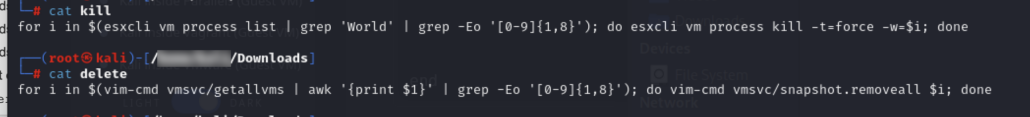
Figure 4: Content of the “kill” and delete scripts
Another file created is “delete,” which is a shell script using the ESXi command-line utility vim-cmd to delete all available virtual machines.
Copies of ransom notes were dropped in directories where files were encrypted, consistent with other ransomware behavior.
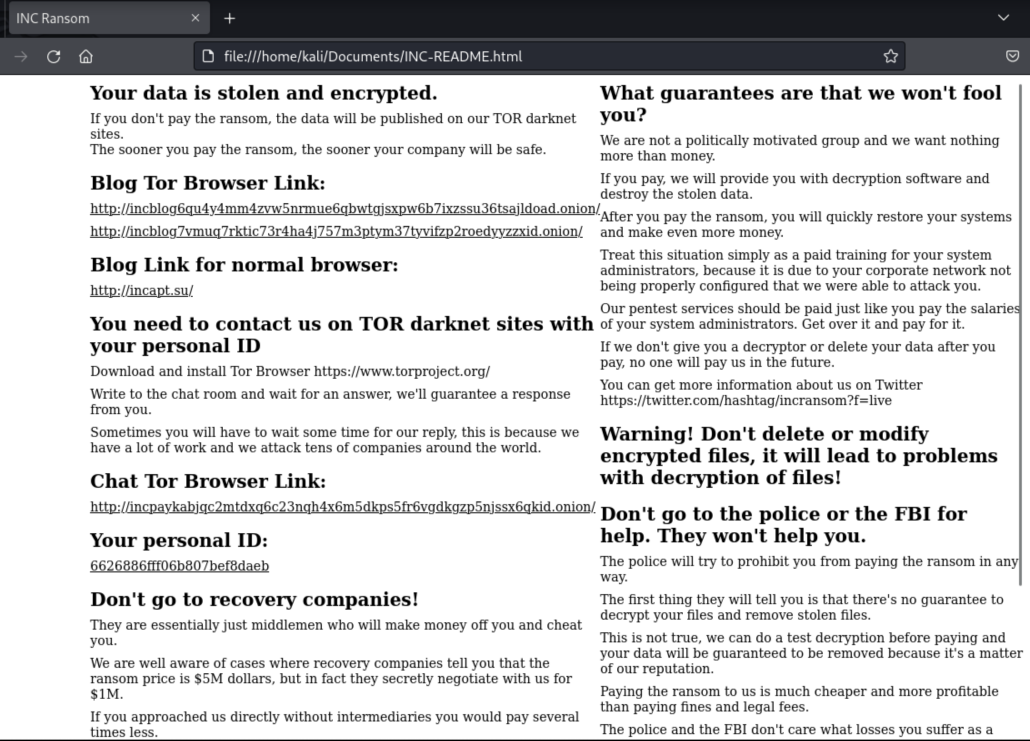
Figure 5: Contents of “Inc_readme.html” Ransom note
The parameter ‘–motd’ also changed the message of the day (MOTD) on the infected machine to display the ransom note message upon successful login.
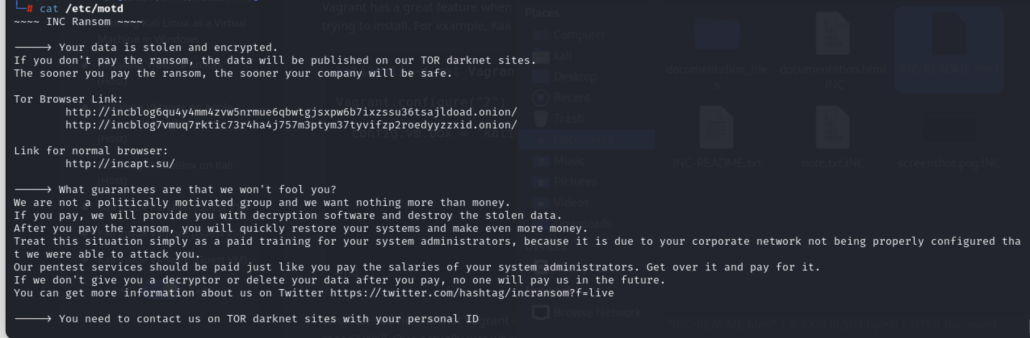
Figure 6: Message of the Day shows ransom note message
Visiting the URL in the ransom note led to a blog site listing all supposed victims.
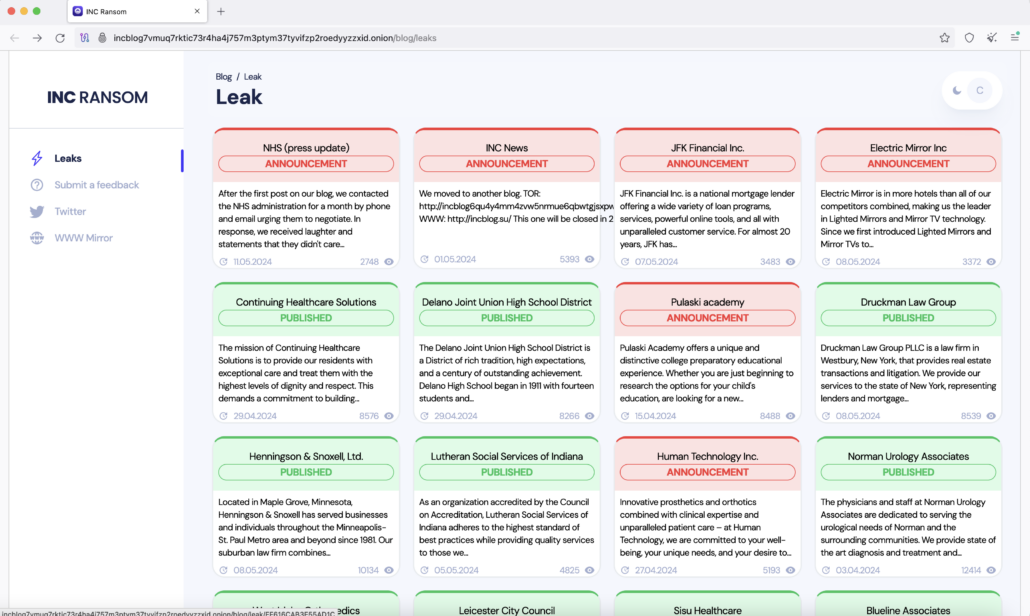
Figure 7: INC Ransom blog site
SonicWall Protections
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: LinuxINC.RSM(Trojan)
This threat is also detected by SonicWall Capture ATP w/RTDMI and the Capture Client endpoint solutions.
For further details, visit the official man page for MOTD.
Share This Article

An Article By
An Article By
Security News
Security News