Patch Tuesday: Which Vulnerabilities Really Need Prioritizing?
What 900+ vulnerabilities say about Microsoft, patching and today's threat environment.

By the end of 2023, Microsoft’s cybersecurity team had addressed a formidable 911 vulnerabilities, including 21 zero days. Propelled by sheer will and endless coffee, the team resolved 131 vulnerabilities in July alone—an average of more than four per day. Amid this frenetic pace, questions arise: Did every one of these issues demand an urgent fix? Does the sheer number suggest Microsoft’s products carry too much risk for organizational use? And how can we sift through the details to identify the truly critical vulnerabilities?
To demystify these concerns, SonicWall Capture Labs has meticulously analyzed each 'Patch Tuesday' release throughout the year. This research doesn't just recount vulnerabilities; it delves into their practical impact, offering insights beyond traditional categories and CVSS scores. By examining how attackers exploit these weaknesses, the work of our Capture Labs threat research team provides invaluable guidance, helping partners and customers prioritize their cybersecurity strategies effectively.
One Company, Millions of Attacks
In 2023, SonicWall firewalls prevented over 3.28 million attacks related to Microsoft vulnerabilities, emphasizing the importance of taking Patch Tuesday seriously. The insights from analyzing Patch Tuesday releases underscore the necessity of an informed approach to vulnerability management — and illuminates the need for organizations to ensure that decisions are strategically aligned with realistic cyber threats.
To begin our analysis of the data, we started by looking at the number of vulnerabilities released each month, as shown in Figure 1. July emerged as the standout month with 131 vulnerabilities, closely trailed by October, which recorded a substantial 104 CVEs. In contrast, December marked the lowest count at 33, accompanied by May and November with 38 and 57, respectively.
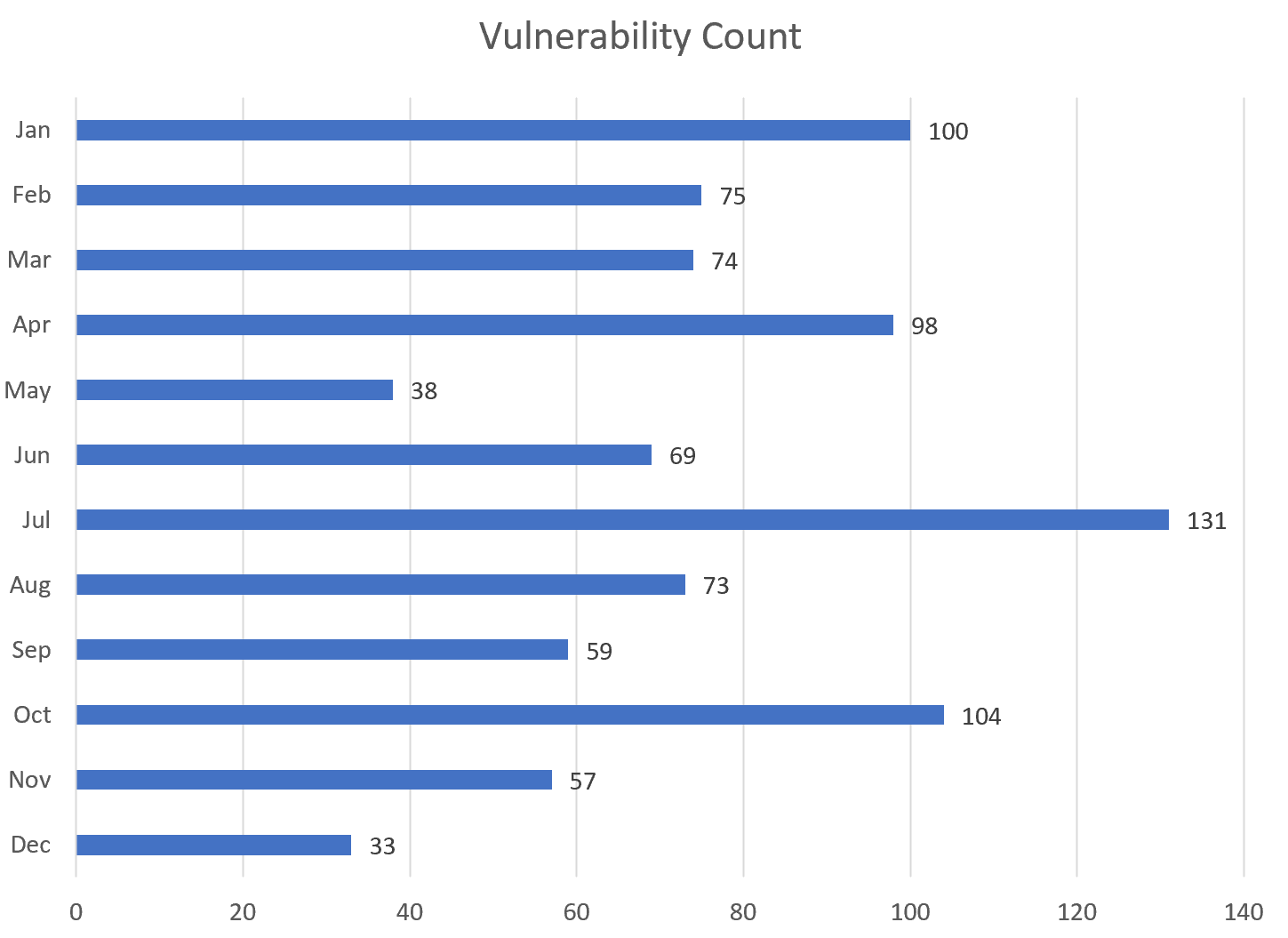
Figure 1
Microsoft also tracks vulnerabilities that are being actively exploited at the time of discovery, as well as those that have been disclosed publicly before the Patch Tuesday release for each month. Figure 2 displays these monthly metrics.
July and November emerge as key months, with five exploits and one disclosure in July and three of each in November.
In 2023, Microsoft addressed 21 zero-day exploits, alongside 11 vulnerabilities that were publicly disclosed before their scheduled patch updates. This evolving threat landscape accentuates the crucial role of MSPs in offering continuous monitoring and proactive defense strategies against emerging vulnerabilities far beyond the capabilities of occasional oversight by SOC analysts. MSPs are indispensable in navigating this dynamic environment to safeguard against potential cybersecurity breaches.
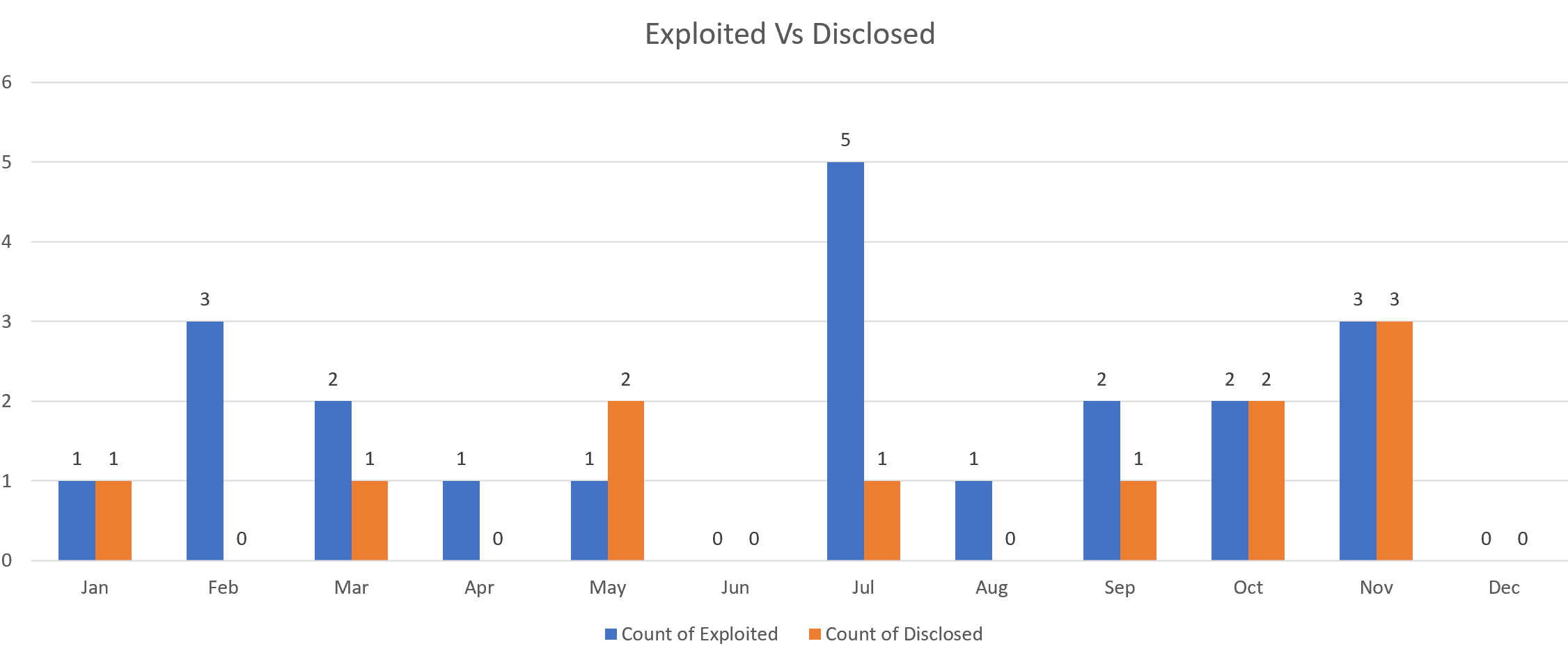
Figure 2
Throughout the entirety of 2023, the predominant focus in patching vulnerabilities for an organization each month often revolved around addressing issues related to Remote Code Execution and Elevation of Privilege. These two categories consistently emerge as the primary areas of concern. Figure 3 demonstrates that these categories account for on average more than half of the released patched vulnerabilities.
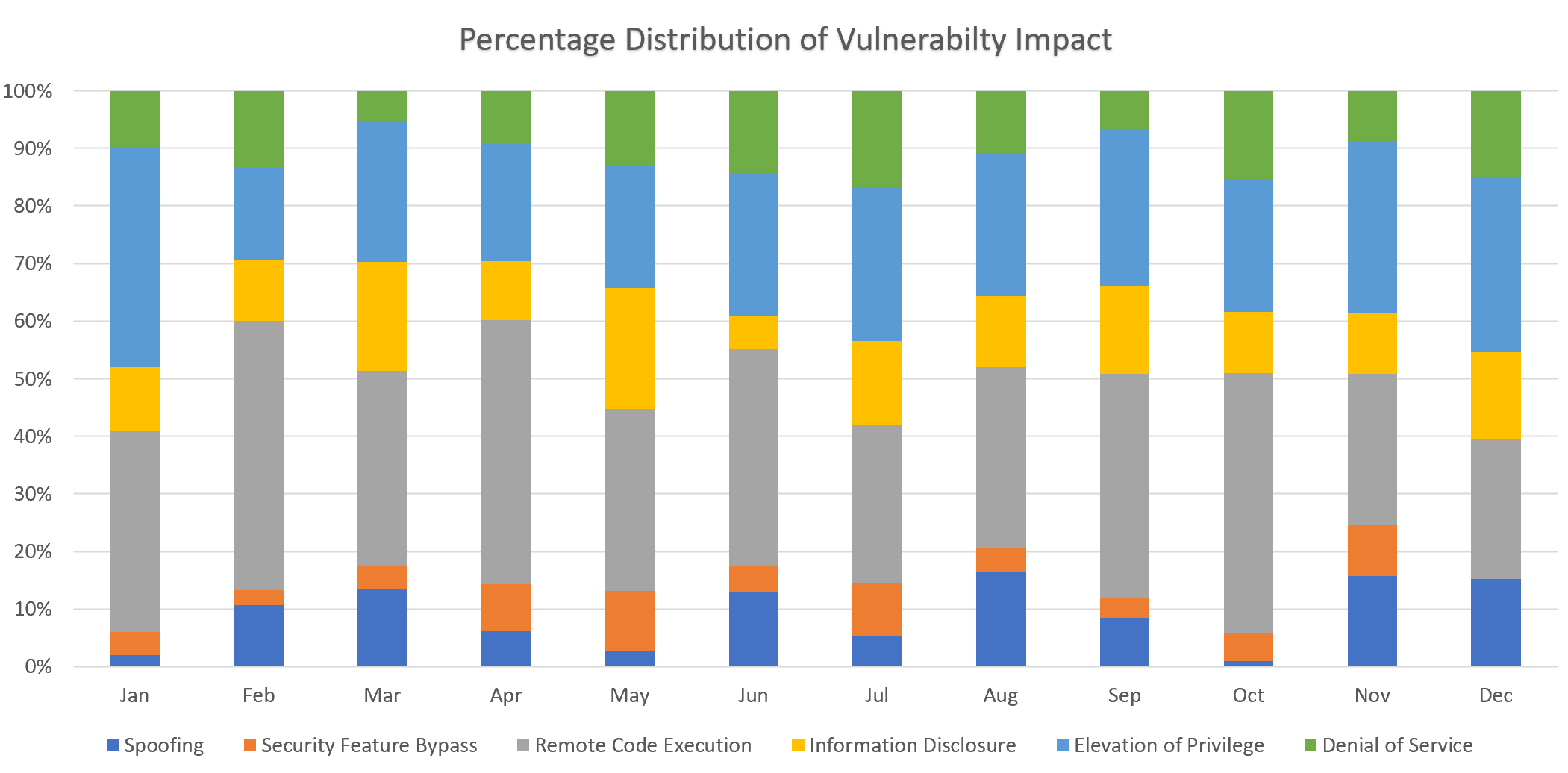
Figure 3
Does Most Common Mean Most Exploited?
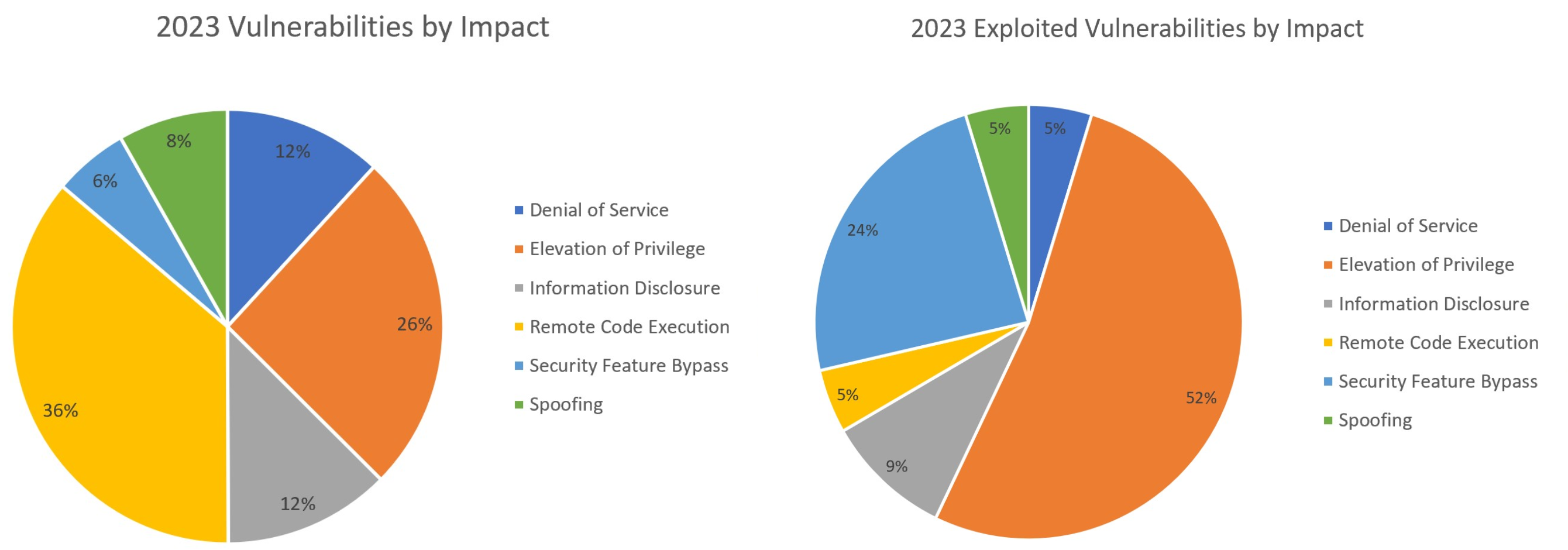
But are remote code execution and elevation of privilege the right areas for a business to focus on when it comes to Microsoft vulnerabilities? It's noteworthy that, among the 21 exploited vulnerabilities, over half are attributed to Elevation of Privilege and nearly one-fourth are related to Security Feature Bypass, as seen in Figure 5.
In contrast, when considering the 911 total vulnerabilities that Microsoft patched in 2023, Remote Code Execution accounts for 36%, as seen in Figure 4. This is intriguing because, despite Remote Code Execution vulnerabilities constituting a significant portion of the overall vulnerabilities, attackers appear to exploit Elevation of Privilege vulnerabilities more frequently.
This underscores the importance of focusing on addressing and mitigating Elevation of Privilege vulnerabilities in cybersecurity strategies, even though Remote Code Execution vulnerabilities are numerically more prevalent and often considered a higher criticallity.
The underuse of Microsoft remote code execution vulnerabilities points to a broader trend in cyberattack strategies. SonicWall's 2023 Cyber Threat Report highlights an expected persistently high level of phishing attacks, particularly through deceptive emails invoking urgency and pointing to legitimate-looking login pages. These phishing efforts and Microsoft privilege escalations address two key stages in the MITRE ATT&CK Matrix: gaining initial access and escalating privileges. We’re seeing that attackers favor phishing over Microsoft-specific exploits for initial entry, and subsequently favoring exploiting Microsoft's privilege vulnerabilities to enhance their access.
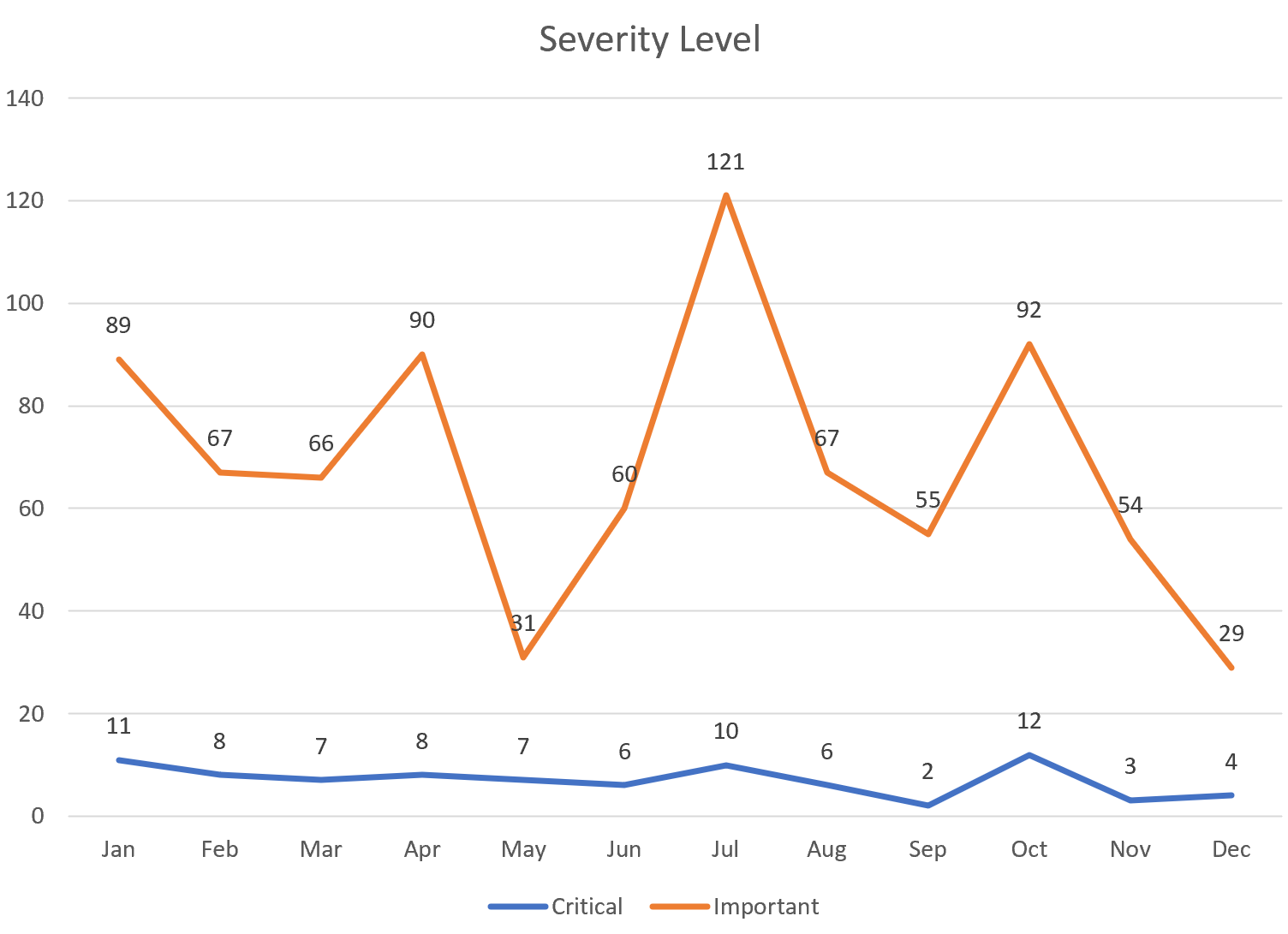
Figure 6
Figure 6 showcases the monthly distribution of critical and important issues. These peaked in July, with 10 critical and 121 important vulnerabilities, and dipped in September, with just 2 critical and 55 important issues. By the end of 2023, a total of 84 critical and 821 important vulnerabilities had been patched.
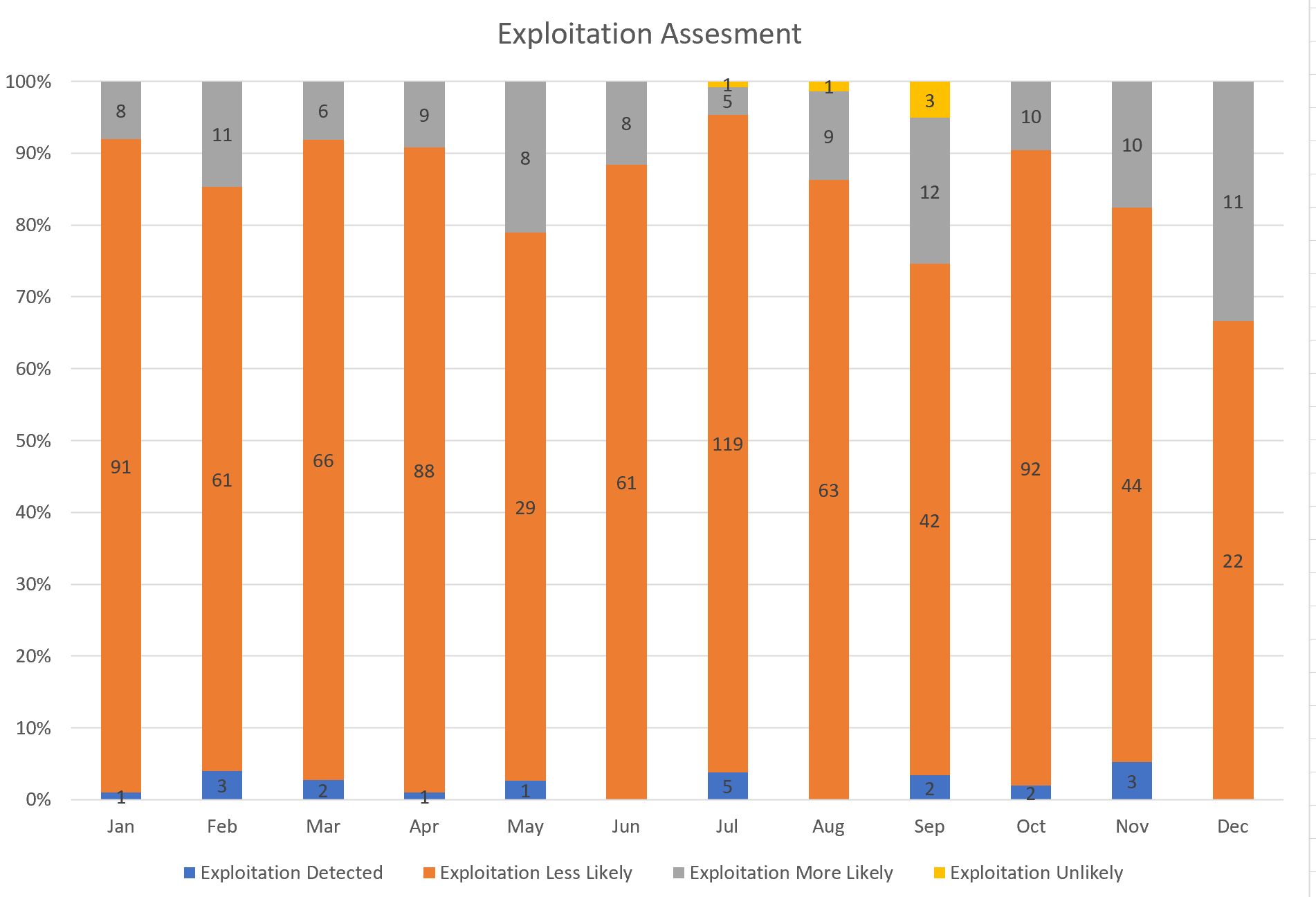
Figure 7
Figure 7 provides a snapshot of Microsoft vulnerabilities in 2023 based on the Microsoft Exploitability Index at the time of Patch Tuesday each month. July is notable in both "Exploitation Detected" and "Exploitation Less Likely" categories. Overall, the year sees 20 vulnerabilities with detected exploitation, 778 with a lesser likelihood, 107 more likely to be exploited, and 5 deemed unlikely to be exploited.
These 107 "Exploitation More Likely" vulnerabilities are particularly noteworthy. On Patch Tuesday, these vulnerabilities are not currently being exploited, but Microsoft indicates they “would make it an attractive target for attackers, and therefore more likely that exploits could be created.” It recommends that organizations ”should treat this with a higher priority.”
But does this hold true? After Patch Tuesday, CISA only added four more vulnerabilities to the known exploited category. Two out of the four added were previously labeled “Exploitation Less Likely.” The category of these vulnerabilities is also intriguing, as three are Elevation of Privilege and one is Security Feature Bypass. This again underscores the prevalence of attackers targeting Elevation of Privilege vulnerabilities. Weak authentication, misconfigured access controls and social engineering are common initial access methods that allow these Elevation of Privilege attacks to be successful.
When considering these two data points, it's reasonable to conclude that, for organizations looking at a large list of Microsoft vulnerabilities, the category of elevation of privileges should carry more weight in prioritization than the exploitable index or other types of vulnerabilities.
Throughout 2023 and into 2024, Microsoft's operating system remains the leader, commanding a robust 72% share of the desktop market. This dominance attracts cyber attackers, targeting the broadest array of organizations. SonicWall's findings, revealing over 3.28 million thwarted Microsoft-targeted attacks in 2023, underscore the high stakes.
Microsoft tirelessly works to secure its extensive product range, as demonstrated by the 911 vulnerabilities addressed in 2023's Patch Tuesdays — yet only about 3% were exploited. This low exploitation rate affirms Microsoft's dedication to enhancing security and the increasing challenge of exploiting vulnerabilities in their environment.
The prevalence of vulnerabilities, contrasted with their selective exploitation, underscores the critical need for businesses to prioritize and monitor threats efficiently. While elevation of privilege vulnerabilities can receive a lower CVSS and exploitability probability score, they are often the most attractive to threat actors because they fill a critical gap in their playbook.
Share This Article

An Article By
An Article By
Ashwini Bhagwat
Ashwini Bhagwat