Progress Kemp LoadMaster Unauthenticated Command Injection Vulnerability

Overview
The SonicWall Capture Labs threat research team became aware of a noteworthy vulnerability — an Unauthenticated Command Injection — in Progress Kemp Loadmaster, assessed its impact and developed mitigation measures for it. Kemp Technologies’ LoadMaster, an application delivery controller and load balancer, published an advisory on this vulnerability affecting all LoadMaster releases after 7.2.48.1 and the LoadMaster Multi-Tenant (MT) VFNs. LoadMaster can be deployed on various platforms such as hardware, cloud and virtual machines. This vulnerability is identified as CVE-2024-1212 and was assigned a critical CVSS score of 9.8. Considering the sizeable user base, low attack complexity and publicly available exploit code including a Metasploit module, LoadMaster users are strongly encouraged to upgrade their instances to the latest versions with utmost priority.
Technical Overview
This vulnerability allows threat actors to circumvent the authentication mechanism by sending a crafted request to the web server.
The conditions that led to the exploitation of the vulnerability in the Progress Kemp LoadMaster load balancer were:
- Bypassing Disabled API Restrictions: It was possible to access the REST API, even when disabled, by crafting a specific request path and parameters. This bypass allowed researchers to reach critical functions that were supposed to be inaccessible with the API disabled.
- Unauthenticated User Input Handling: The system did not properly validate or sanitize the "REMOTE_USER" and "REMOTE_PASS" environment variables, which were set based on user-provided basic authentication headers. This flaw allowed for the injection of arbitrary commands.
- Command Injection via System Call: The lack of validation and sanitization led to constructing a command with user-controllable input that was then passed to a system() call. This behavior facilitated the execution of arbitrary commands on the system.
- Exploiting Basic Authentication for Command Execution: By manipulating the base64-encoded authorization string sent in the HTTP headers, attackers could inject commands that the server would execute, enabling a direct path to command injection and system compromise.
Triggering the Vulnerability
The flaw is in the processing of the "/access/" RESTful API Interface to the LoadMaster.
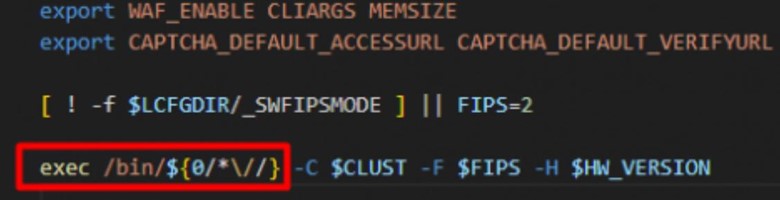 Figure 1: LoadMaster CGI Bash Script
Figure 1: LoadMaster CGI Bash Script
As seen in the code shared by RhinoSecurity Labs in Figure 1, user input to the “/access/" API is directly put into a bash script leading to a critical vulnerability tracked as CVE-2024-1212. Before being passed to any function(s), the user input should be mandatorily parameterized and sanitized.
Leveraging this unauthenticated command injection vulnerability requires access to the vulnerable LoadMaster administrator web user interface. The publicly available also shows the possibility of privilege escalation once the shell is obtained.
An example request to trigger the vulnerability would look like this http[:]//target-ip:port/access/set?param=enableapi&value=1 with the Authorization parameter containing the command injection, as shown in Figure 2.
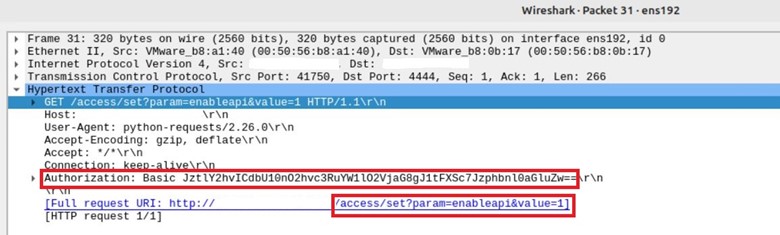
Figure 2: Triggering CVE-2024-1212 PoC packet capture
Notice the command injection is base64 encoded. When decoded, the attacker is sending the ‘;echo ‘’hostname;echo’’;’:anything as shown in Figure 3.
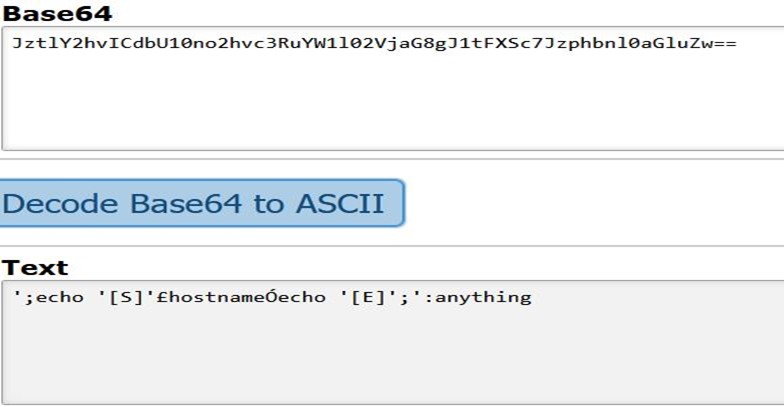
Figure 3: Decoded-authorization-header
The default admin configuration of a LoadMaster instance is a user named “bal”, as shown in Figure 4. One can fully control the system by manipulating sudo user entries via the management interface.
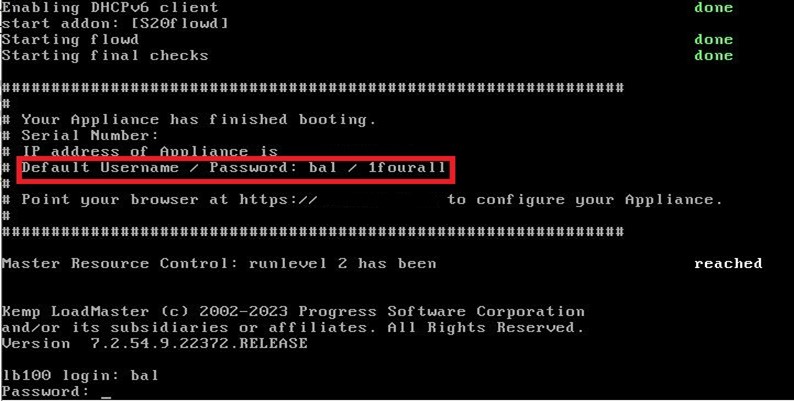 Figure 4: Default LoadMaster interface
Figure 4: Default LoadMaster interface
SonicWall Protections
To ensure SonicWall customers are prepared for any exploitation that may occur due to this vulnerability, the following signatures have been released:
- IPS 4362 - Progress Kemp LoadMaster Command Injection
Threat Graphs
SonicWall sensors have confirmed exploitation attempts of this vulnerability. The graph below indicates increased exploitation attempts over the last 6 days.
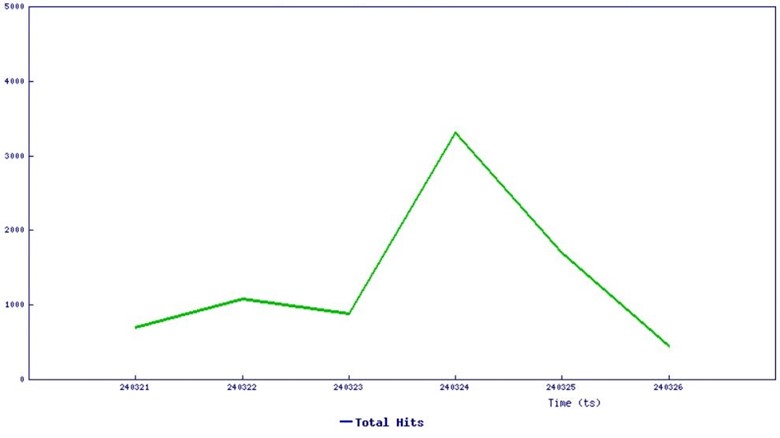
Figure 5: Threat graph
Remediation Recommendations
Considering the severe consequences of this vulnerability and the trending of unauthenticated nefarious activists trying to get Loadmaster management interface access using the exploit in the wild, users are strongly encouraged to upgrade their instances as published in the vendor advisory.
Relevant Links
- NVD
- GitHub PoC
- Latest LoadMaster-Firmware
- GitHub Advisory Database
- RhinoSecurity Labs blog
- LoadMaster Advisory
- LoadMaster Release Notice
- LoadMaster ECS Connection Manager Advisory
*Originally this article claimed we had confirmed active exploitation of this vulnerability. This was a mistake. We have confirmed exploitation attempts, and the article now reflects that.
Share This Article

An Article By
An Article By
Security News
Security News