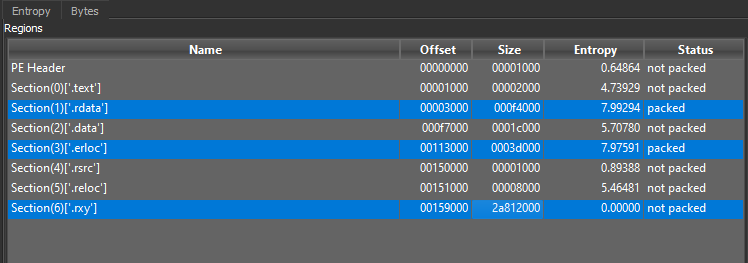
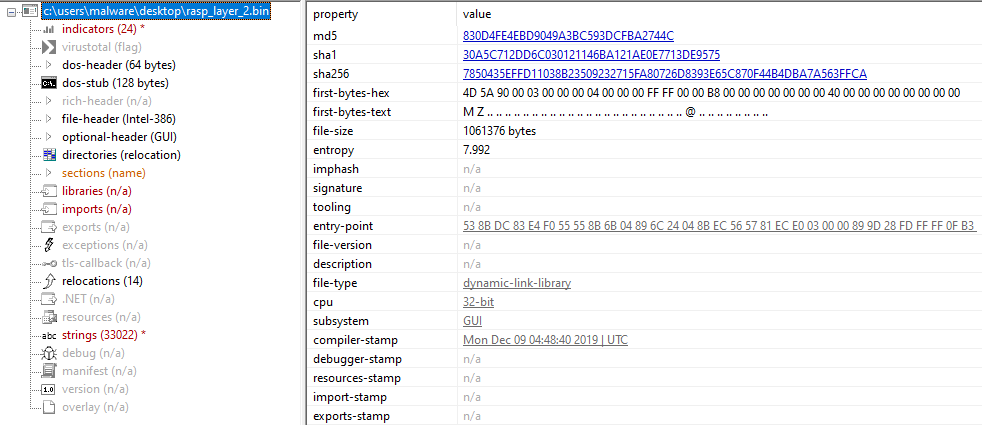
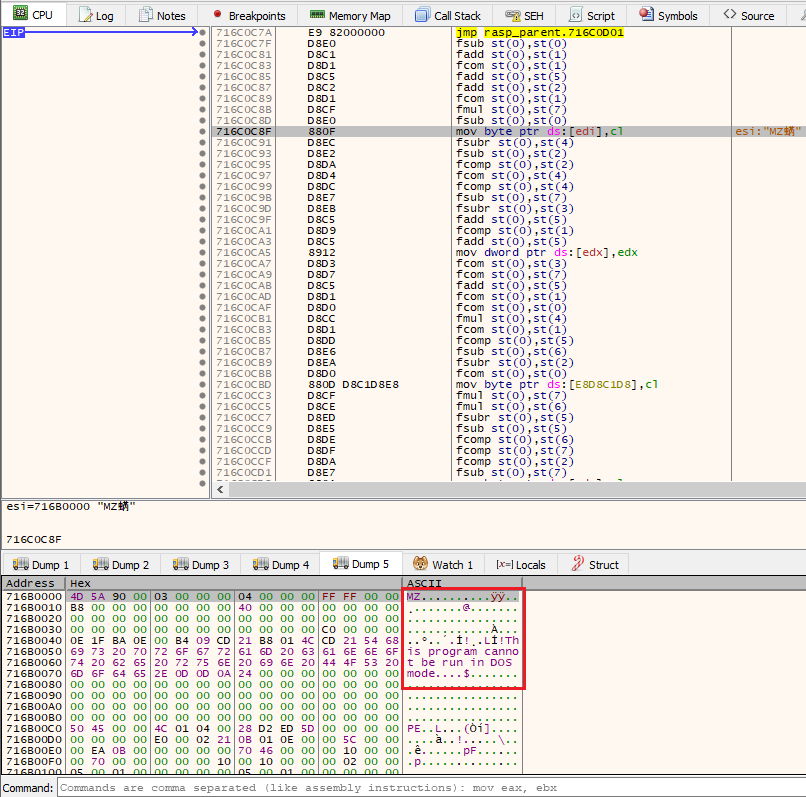
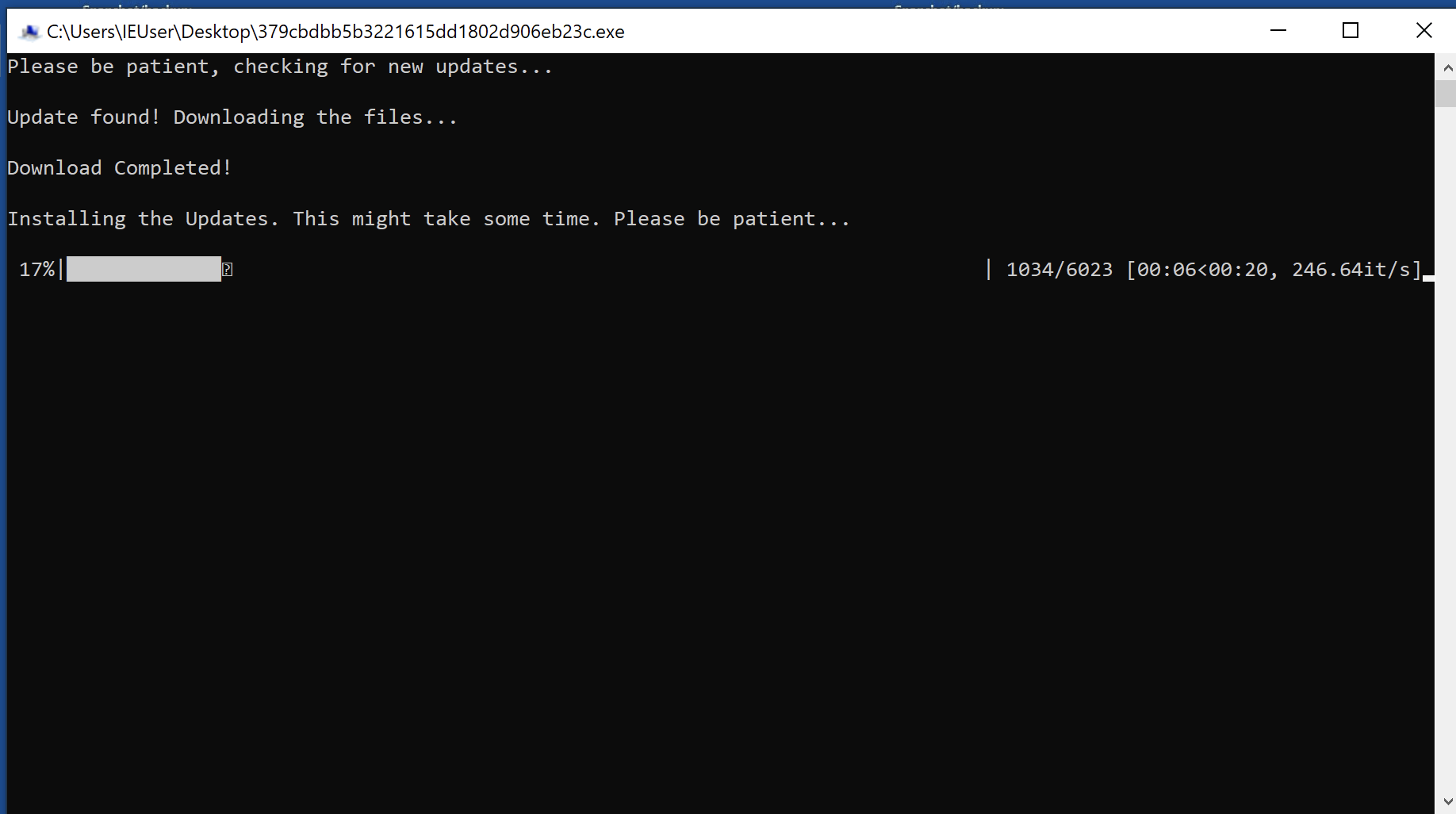
SonicWall curates important news stories and trends from all over the world to help you understand the state of cybersecurity.
SonicWall is on a roll with news from partners in Latin America and the big news that its next-generation firewalls won CRN’s prestigious 2022 Products of the Year Awards.
Industry news reveals that law enforcement from the US, Netherlands and the UK have ‘powered down’ a major DDoS service provider. This report has contributions from the US Department of Justice, the UK National Crime Agency, Tech Crunch, Hacker News, and Krebs on Security.
Reuters reported that a former Twitter employee earned 3-1/2 years of prison for spying for Saudi Arabia.
According to Bleeping Computer, Social Blade, a data analytics provider, was breached, and hackers are selling the data on a hacking forum.
Then from Hacker News, another large Australian company was hacked. This time, it’s TPG Telecom’s turn.
According to Dark Reading, the Iranian state-sponsored cyber-attack APT group known as ‘Charming Kitten’ is including murder for hire and kidnapping as part of its operations.
And finally, SCMagazine reports that Microsoft is blocking threat actors that obtained signed drivers to deploy ransomware. The story also advises that all Windows administrators and even home users install critical security updates as soon as possible.
Remember that cybersecurity is everyone’s business. Be safe out there!
SonicWall News
BizCommunity, SonicWall News: Figures from SonicWall’s Biannual Report revealed that e-commerce and online retail businesses saw a 264% surge in the past 12 months in ransomware attacks alone. These statistics are extremely worrying for retail companies, so unsurprisingly, websites and digital security are at the forefront of retailers’ minds.
InfoChannel (Mexico), SonicWall News: 2022 has been a year of growth for SonicWall, especially for business partners, as announced by Eustolio Villalobos, general manager for Mexico, Central America and the Caribbean. Villalobos said that the company reached a record of internal sales in generation 7, SD-WAN and Wi-Fi 6 firewall solutions.
eSemenal (Mexico), SonicWall News: Today we have seen how companies are more aware of the cybersecurity challenges they face and have understood that it is not a separate issue. Expanding issues such as hybrid work and 5G will be some of the main challenges next year, and companies regardless of their size will have to be prepared,” said Arley Brogiato, Sales Leader for SonicWall in Latin America.
According to the executive, sales of security solutions this year exceeded the company’s expectations globally, achieving higher growth than the prospect and a double-digit increase in its market shares.
PR Newswire, SonicWall News: SonicWall today announced that its next generation firewalls were a winner in CRN’s prestigious 2022 Products of the Year Awards, notching yet another award in an impressive run for the company that is diligently driving new and innovative strategies to its partners offset rising costs industry-wide.
Total Security Advisor, SonicWall News: Ransomware will continue to be a leading way for bad actors to leverage control and data to monetize hacking organizations. According to the SonicWall Cyber Threat Report, the global volume of ransomware is increasing by 98%. Although this number is down from a 105% increase in 2021, the frequency and dollars spent continue to grow. Globally, healthcare, financial services, manufacturing, and state and local governments continue to see a rise in the frequency of attacks. Interestingly, a growing trend in this game of cat and mouse is that you may pay the ransom and still not be set free from the hacker’s control.
Solutions Numeriques (FR), Reprint from SonicWall Blog: SonicWall is organizing an event on this theme of the Art of War: December 15, presented by Guillaume Sevrin, SonicWall EMEA pre-sales manager.
Cyber Security Intelligence, SonicWall News: The retail sector is a specific target for Hive ransom attacks and this confirmed by an authoritative threat report by SonicWall, which found that retailers saw a 90% increase in ransomware attacks in 2022, whereby hackers attempt to cripple their day-to-day infrastructure.
Business Reporter, SonicWall News: Combining these factors with the avalanche of cyber-attacks on connected devices makes the challenge even more insurmountable. According to SonicWall, the total number of malware attacks on IoT-enabled devices rose by 77 per cent in the first half of 2022 to an alarming 57 million. The number of “never-before-seen” malware variants, that are the hardest to defend against, also rose by 45 per cent in the period.
CRN UK, SonicWall News: “Looking at the enlarged UK business, Griffiths said that Nuvias hands it “scale and power”. While Infinigate’s largest vendors were Progress Software and SonicWall, Nuvias held bigger partnerships with the likes of Juniper Networks.”
Computer Weekly, SonicWall News: SonicWall’s 2022 Cyber threat report states that ransomware incidents on governments across the globe increased by 1,885% last year, with the healthcare industry alone suffering a 755% increase.
GIS User, SonicWall News: We recommend using a reliable VPN service that uses military-grade encryption, such as SonicWall VPN. It has a wide range of features and is very affordable. It is important to note that not all VPN services are created equal, so it is essential to do your research before choosing one.
Cyber Magazine, SonicWall News: We can expect smaller scale attacks, for lower amounts of money, but which target a much broader base. The trend will probably hit education providers hard: education is already the sector most likely to be targeted by a malware, cryptojacking or encrypted attack, according to SonicWall’s 2022 Cyber Threat Report.
Industry News
Operation PowerOFF: Major DDoS Service Providers Hit Hard
The FBI working with law enforcement in California, Alaska, the Netherlands and the UK National Crime Agency, has shut down 50 domains involved in selling denial-of-service-for-hire tools to the public. In addition, six people in California and Alaska were charged with directing what are known as “booter” and “stressor” services. They are joined by one other individual from the UK whom authorities identified as a site administrator.
A booter service allows anyone to order DDoS attacks for a minimal monthly fee. They may have a simple front end and Web interface, email support, and detailed tutorials. The services often provide the user with a set of attack vectors and the ability to select a target and its IP address. The attacker can then use the service’s attack infrastructure to launch a DDoS attack. The service operators often prefer to use bitcoins as a payment method. Most of the booter services are run by teenagers or young adults. The service typically offers a variety of membership options and may include email support, detailed tutorials, and YouTube instructional exercises.
The sites seized were among the most extensive DDoS-for-hire services in the market. They had a six-month lifecycle and were typically located in North America, Israel, or Europe.
This summary is a compilation of contributions from the US Department of Justice, the UK National Crime Agency, Tech Crunch, Hacker News, and Krebs on Security.
Ex-Twitter worker gets 3-1/2-year US prison term for spying for Saudi Arabia
From Reuters, a California judge sentenced an ex-Twitter employee to three and a half years in prison for spying for Saudi Arabia and sharing user data several years ago and potentially exposing users to persecution. According to a US Dept of Justice press release, Ahmad Abouammo was accused of being paid to obtain information about Twitter users who were critics and dissidents of the kingdom. One of the bribes was a Hublot watch that the man offered for sale on Craigslist for $42,000. Prosecutors also said that he received another $200,000.
Social Blade confirms breach after hacker posts stole user data
According to a report from Bleeping Computer, a data analytics tool known as Social Blade suffered a data breach after its database was stolen and up for sale on a hacking forum. Social Blade provides statistical graphs for YouTube, Twitter, Twitch, Daily Motion, Mixer, and Instagram, allowing customers to see estimated earnings and projects. According to Bleeping Computer, the attacker found a security gap to gain access. The data stolen includes usernames, email addresses, and password hashes. The company clarified that the security incident did not expose any credit card information.
Hackers Breach TPG Telecom Email Host
From HackRead, another large Australian company was hacked. This time, it’s TPG Telecom’s turn. According to a TPG Telecom letter, hackers breached their Microsoft Exchange server. Around 15,000 email accounts were affected, and these seemed to be owned by business users. The company also reported that hackers appeared to be searching for customers’ cryptocurrency and financial information. Neither the company nor other reports offered further details, but an investigation into the attack continues. Recent targets were also Optus telecom and Medibank private health services.
Iran-Backed Charming Kitten APT Eyes Kinetic Ops, Kidnapping
More information is trickling in about an Iranian-based cyber-attack group called TA453, but other researchers refer to it as Charming Kitten or Phosphorous. According to Dark Reading, this group is classified as a state-sponsored advanced persistent threat (APT). The group usually targets academics, researchers and journalists with sometimes deadly expertise. Attacks can begin with benign email conversations that last for weeks before the victim receives a message with malicious links or documents. For example, one victim was the press secretary for an American government official. A second target, an American academic, was sent a suspicious message by a hacked email account of a reporter. But the truly chilling thing about this group is that in the latest campaigns, researchers have observed more aggressive activity, which agents could use to support attempted “kinetic operations,” including murder for hire and kidnapping.
Microsoft blocks threat actors that obtained signed drivers to deploy ransomware
From SCMagazine’s threat intelligence reporters, Microsoft disclosed Tuesday that it suspended several developer program accounts that obtained drivers certified by its Windows Hardware Developer Program. The accounts, the report claims, likely deployed ransomware on telecommunications, outsourcing companies, MSSPs and financial services.
Certificates for the impacted files were revoked in Microsoft’s latest patch Tuesday on Dec. 13, and the seller accounts were suspended. In addition, Microsoft said it also implemented blocking detections against legitimately signed drivers being used maliciously for post-exploit activity. The Dec. 13’s Patch also includes fixes for 48 vulnerabilities found in its products, six of which were listed as critical.
This leads us to a general advisory for Windows administrators and users at home: install the Windows security updates released in September and now December as soon as possible.
SonicWall Blog
‘3 & Free’ Promotion: How to Upgrade to a New SonicWall TZ Series NGFW for Free – Matt Brennan
The Art of Cyber War: Sun Tzu and Cybersecurity – Ray Wyman
Talking Boundless Cybersecurity at the Schoolscape IT 2022 Conference – Mohamed Abdallah
3 & Free: 1 Amazing Deal, 2 Exceptional Firewalls, 3 Years of Superior Threat Protection – Matt Brennan
SonicWall Wins CRN’s 2022 Tech Innovator Award in Enterprise Network Security – Bret Fitzgerald
SonicWall Included on the Acclaimed CRN Edge Computing 100 List for 2022 – Bret Fitzgerald
A New Era of Partnering to Win – Robert (Bob) VanKirk
Multiply Your Security with Multifactor Authentication – Amber Wolff
10 Reasons to Upgrade to the Latest SonicWall Gen 7 TZ Firewall – Sarah Choi
SonicWall Third-Party Threat Performance: Seven Times Superior – Amber Wolff
Q3 2022 Threat Intelligence Highlights Changing Threat Environment in 2022 – Amber Wolff
Securing Your Credentials: Does Your Password Pass the Test? – Amber Wolff
The Power of Patching: Why Updating Your Software Should Be a Top Priority
Think Before You Click: Spotting and Stopping a Phish – Amber Wolff
National Cybersecurity Awareness Month Spotlights the Role of Individuals in Stopping Attacks – Amber Wolff
Seamless Security: How SonicWall Solutions Work Together to Safeguard Your Organization – Sarah Choi
SonicWall’s Nicola Scheibe Recognized by CRN as One of 2022’s 100 People You Don’t Know But Should – Bret Fitzgerald
SonicWall NSM 2.3.4 Uplevels Central Management Capabilities – Amber Wolff
Why 5G Needs to Start with Secure Network Access – Rishabh Parmar
Security Platform Vendors vs. Best-of-Breed Approach to Security Architecture – Rajesh Agnihotri
Why Organizations Should Adopt Wi-Fi 6 Now – David Stansfield