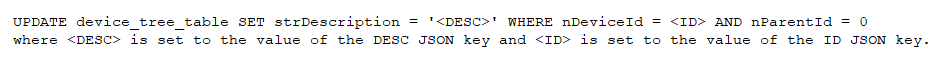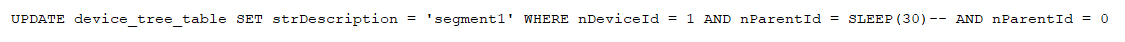Advantech iView SQL Injection Vulnerability

Overview:
SonicWall Capture Labs Threat Research Team has observed the following threat:
Advantech iView is a Simple Network Management Protocol-based element management software provided free-of-charge with intelligent FTTx, Optical Access, Media Conversion and eWorx Smart Industrial Ethernet Switch solutions. iView features an intuitive Graphical User Interface that provides a real-life representation of all installed B+B SmartWorx equipment, enables network managers to control and monitor device functions, port settings, receive device status information and traffic statistics via SNMP. iView supports multiple platforms; iView is a Web-based application that runs on 32-bit/64-bit Windows using Microsoft Edge/IE, Google Chrome or Mozilla Firefox browsers.
A SQL injection vulnerability has been reported for Advantech iView. This vulnerability is due to improper input validation for the ID parameter in the updateSegmentInfo process.
A remote, unauthenticated attacker could exploit this vulnerability by sending a crafted request to the target server. Successfully exploiting this vulnerability could result in SQL injection.
CVE Reference:
This vulnerability has been assigned the Common Vulnerabilities and Exposures (CVE) identifier CVE-2022-2135.
Common Vulnerability Scoring System (CVSS):
The overall CVSS score is 6.4 (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:L/A:L/E:U/RL:O/RC:C).
Base score is 7.3 (AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:L/A:L), based on the following metrics:
• Attack vector is network.
• Attack complexity is low.
• Privileges required is none.
• User interaction is none.
• Scope is unchanged.
• Impact of this vulnerability on data confidentiality is low.
• Impact of this vulnerability on data integrity is low.
• Impact of this vulnerability on data availability is low.
Temporal score is 6.4 (E:U/RL:O/RC:C), based on the following metrics:
• The exploit code maturity level of this vulnerability is unproven.
• The remediation level of this vulnerability is official fix.
• The report confidence level of this vulnerability is confirmed.
Technical Overview:
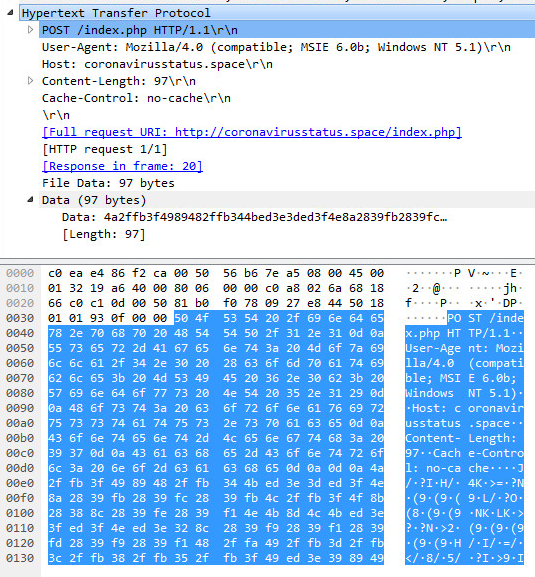
When a user sends a HTTP GET/POST request to the Request-URI "/iView3/NetworkServlet", the function NetworkServlet.doPost() is called. The function NetworkServlet.doPost() first checks the value of the parameter page_action_type and compares it to multiple values. Each value corresponds to a different action to be performed by the server. The value of importance in this vulnerability is "updateSegmentInfo". If the value of the parameter page_action_type is equal to "updateSegmentInfo", the function NetworkServlet.updateSegmentInfo() is called.
The function NetworkServlet.updateSegmentInfo() is used to update the name of created network segments. The value of the parameter data is stored in the variable strJSONObj and is passed to the function DeviceTreeTable.saveSegmentInfo().
The function DeviceTreeTable.saveSegmentInfo() is used to prepare the UPDATE SQL query. The string strJSONObj is then converted into a JSON array and stored into the variable arrayJSON. The value of the JSON key DESC is then checked for SQL injection characters. If no such characters exist, the following SQL query is prepared then run on the database:
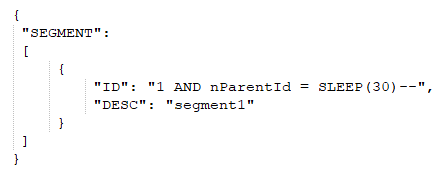
The vulnerability exists as the value of the JSON key ID is never checked for SQL injection characters. If an attacker sends a request similar to the following:
which the data parameter decodes to:
which would cause the following SQL query to be executed:
This query would cause the MySQL server to sleep for 30 seconds.
*Note, that this same action is performed when a user accesses the Request-URI "/iView3/CommandServle
Triggering the Problem:
• The target must be running a vulnerable version of the software.
• The attacker must have network access to the target server.
Triggering Conditions:
The vulnerability is triggered when the HTTP request is processed and the SQL query is executed.
Attack Delivery:
The following application protocols can be used to deliver an attack that exploits this vulnerability:
• HTTP
• HTTPS
SonicWall's, (IPS) Intrusion Prevention System, provides protection against this threat:
• IPS: 2982 Advantech iView SQL Injection 2
Remediation Details:
The risks posed by this vulnerability can be mitigated or eliminated by:
• Applying the vendor-supplied patch to eliminate this vulnerability.
• Filtering traffic based on the signature above.
The vendor has released the following patch to address this vulnerability:
Vendor Advisory
Share This Article

An Article By
An Article By
Security News
Security News