Why SDP Matters in Zero Trust

Today’s networks have never been more diverse and distributed. While the network and security used to operate within a physical perimeter, digital transformation has made the old castle-and-moat model of security largely insufficient to protect modern networks. Organizations have hardened their network perimeters with firewalls, VPNs and NACs, but as the network perimeter continues to change, these tools need to evolve as well.
Traditionally, users were allowed to “connect first, authenticate later.” Network security relied on application-level permissions for authorization, giving users a pass into the network perimeter. But in today’s era of rising cybercrime, this implicit trust model puts organization at risk and has enabled far too many successful breaches.
Modern networks need flexible and adaptive security in which the perimeter begins with the users. The SDP (software-defined perimeter) model is built around the idea of “authenticate first, connect later,” giving administrators finely grained access control that is defined by policies and network parameters for each individual user.
SDP architectures include a minimum of five layers of security:
- Authentication and validation of devices
- Authentication and authorization of users
- Two-way encrypted connections
- Dynamic provisioning of connections
- Mapping and control of connections to services, while keeping these connections hidden
SDP uses single-packet authorization (SPA) protocol, which validates user or device identity to ensure that network resources are only accessible by authorized users, on a need-to-know basis.
The SDP architecture is made up of three key components:
- SDP Client: runs on the user’s device
- SDP Controller: authentication gate keeper
- SDP Gateway: trust broker to provide secure access to resources
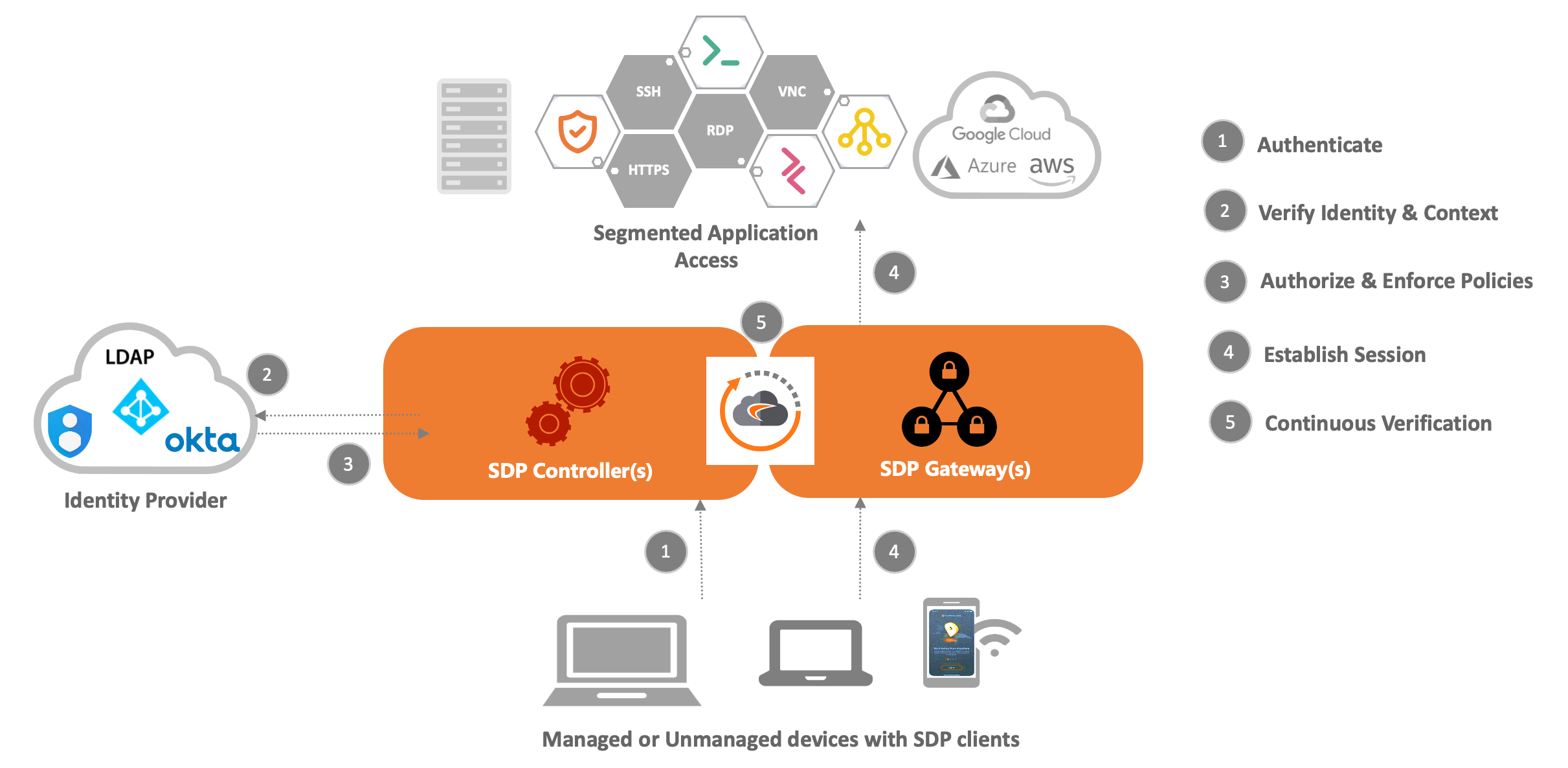
- The SDP client makes an access request to the SDP controller. The controller evaluates credentials and authenticates the client as per the access policies.
- The SDP controller checks the context and passes the individual network entitlement to the SDP client, along with the signed token to access the authorized network resources.
- The SDP client provides network entitlement to the SDP gateway, and the gateway uses it to match applications with the user’s context.
- A dynamic network segment is created to the resource or service from the SDP client to the SDP gateway via encrypted tunnels.
- The end-to-end network segment is continuously monitored for any context changes.
In contrast with the traditional model, Zero Trust is a network security concept built around the idea that networks should trust nothing and verify everything. Implementing Zero Trust requires verification of anything that attempts to connect to your network, even before granting access, and continuous access validation for the duration of connection.
SDP is one of the best and most advanced ways to implement Zero Trust, as SDP is agnostic to underlying IP infrastructure while securing all network connections and the infrastructure itself. SDP architecture separates the control plane, where trust is established, from the data plane — thus providing least-privilege access to tightly defined micro-segments of the network and resources.
SDP is applied at the network layer before the transport layer and prior to the application of the session layer. A Zero Trust implementation using SDP enables organizations to defend new variations of attack vectors that are constantly surfacing in perimeter-centric networking models.
SonicWall Cloud Edge Secure Access enables a simple Network-as-a-Service (NaaS) for site-to-site and hybrid cloud connectivity to AWS, Azure, Google Cloud and more. By combining Zero-Trust, SDP and least-privilege security, the solution enables organizations to offer remote-work flexibility while still protecting high-value assets from costly security breaches.
Share This Article

An Article By
An Article By
Rishabh Parmar
Rishabh Parmar