Resist the Lure of Amazon Spear Phishing
Let’s be real: Approximately everyone and their grandma buy things on Amazon. Amazon became the world’s largest retailer in 2019, and its branding is recognized around the globe. But this widespread popularity can bring with it other, less desirable consequences.
Due to its ubiquity, Amazon is one of the most mimicked companies in email phishing. Because so many people use Amazon, the hackers can create a phishing template and use it many times, simply substituting pertinent personal information based on the target. And since most potential targets will at least have an Amazon account, if not be current users, the odds that the phish will prompt action are much greater.
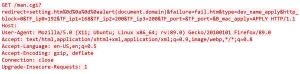
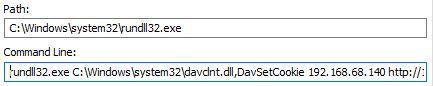
While these phishing attempts take many forms, in the example below, the attackers have spoofed an order confirmation from the Amazon website. The hope is that this confirmation will attract the target’s attention and raise alarm that someone has made an unauthorized purchase.
Despite being an imperfect attempt — the logo is wrong, plus there are grammatical errors — the hallmarks of spear phishing are still present. These attempts are more sophisticated (and thus more dangerous) than standard phishing attempts because the hackers have taken the time to learn about their target, and in turn use this information to craft more convincing lures. Here, the information being leveraged is a name and address, but in reality can be just about anything that could make the attempt seem more authentic.
In this case, the hackers have prompted the target to call a number and report unfamiliar transactions in multiple places on the email, even highlighting this call-to-action to make it pop. (Because this is only a portion of the full email, it is only visible once.)
Calling the number will connect the target with hackers, who will attempt to trick the caller into thinking they are from Amazon Support. If the ruse is successful, the hackers will try to get the victim to reveal personal credentials or other information that could be used to further exploit them.
As attacks like this continue to succeed, they will only get more plentiful. While it’s important that all employees know how to spot a phish, with these sorts of attacks becoming more sophisticated every day, this is no longer a reliable first line of defense.
By implementing solutions such as SonicWall Cloud App Security (CAS) or SonicWall Email Security, you can stop these sorts of attempts from reaching the inbox in the first place — and prevent the data theft, ransomware and more that can result from a successful spear phish. To learn more about how to harden your business against spear phishing attempts, contact us.