AndroidBot malware with obfuscation and multiple capabilities spreading in the wild

SonicWall Threats Research team observed an AndroidBot malware that contains multiple obfuscation layers that hides the hardcoded URLs and malicious code. Similar to a number of Android malware, this malware drops the dex file during execution that contains malicious code.
Sample details
- MD5: 04533b259e5623638184a37ce8a16ffb
- Package Name: com.qkjwie45.ngirwii
- Application Name: application
At the time of writing this blog, this sample is hosted on the following link:
Infection Cycle
The app requests for a number of permissions, below are a few risky ones:
- android.permission.CALL_PHONE
- android.permission.CAPTURE_VIDEO_OUTPUT
- android.permission.DISABLE_KEYGUARD
- android.permission.READ_CONTACTS
- android.permission.READ_SMS
- android.permission.RECEIVE_BOOT_COMPLETED
- android.permission.RECEIVE_SMS
- android.permission.REORDER_TASKS
- android.permission.REQUEST_DELETE_PACKAGES
- android.permission.REQUEST_INSTALL_PACKAGES
- android.permission.SEND_SMS
- android.permission.SYSTEM_ALERT_WINDOW
- android.permission.WRITE_EXTERNAL_STORAGE
- android.permission.WRITE_SMS
Upon installation and execution the application requests for accessibility permissions, once granted the application gains the ability to execute its malicious components:
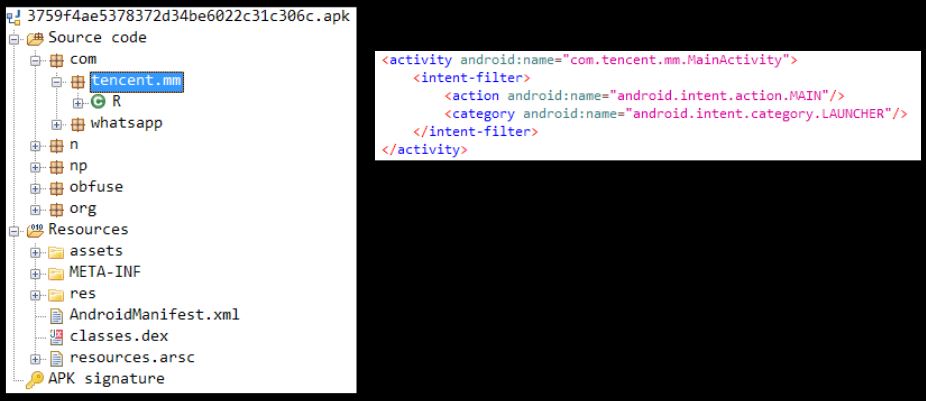
The main class listed in the Manifest.xml file is not present in the decompiled codebase:
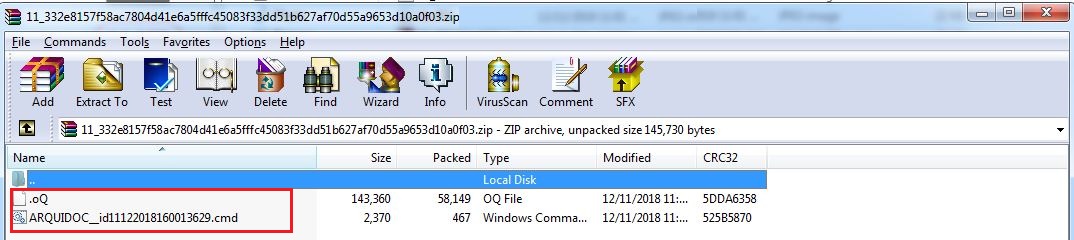
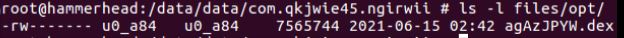
The malware drops a file - agAzJPYW.dex - during execution which is actually the dex file that contains malicious code.:
This dex file contains the main activity which is listed in the original manifest.xml file:
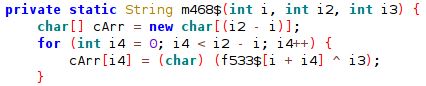
The malware obfuscates the strings present in the code to deter security researchers from analyzing the malware and automated tools from identifying suspicious strings in the code:
However, the decryption routine is also present in the code which can be used to decode the strings:
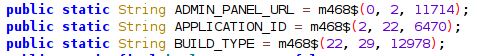
Decoded string:
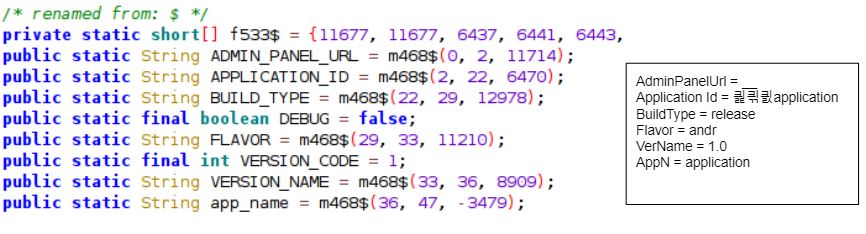
We identified several interesting bits when the strings were decoded:
Capabilities
This bot is capable of performing a series of malicious/dangerous actions on an infected device, some of them include:
- Show custom notifications
- Screencast/screencapture
- TeamViewer execution
- Read, write and send messages
- Extract information about running processes
- Extract information about the device
- Load URLs
- Receive messages via Fire Cloud Messaging (FCM)
- Install and remove applications
- Subscribe to premium messaging services
- Check if emulator is present
Hardcoded URLs
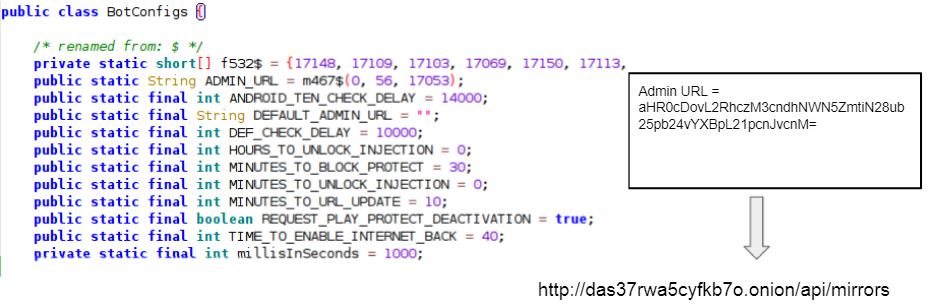
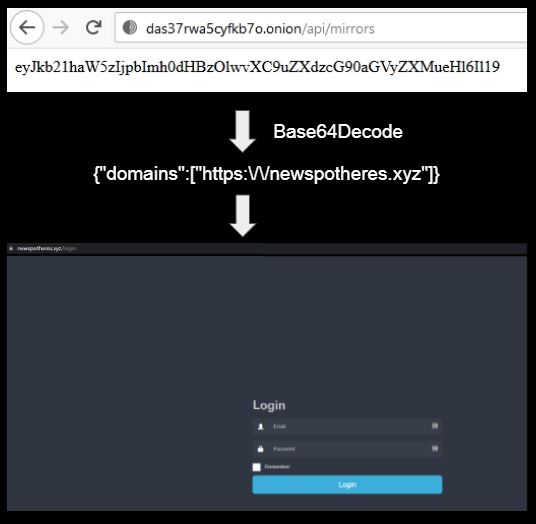
The class BotConfigs contained an interesting string titled Admin URL. Upon deobfuscation we got the string - http://das37rwa5cyfkb7o.onion/api/mirrors. After a series of layers we ultimately obtained a login page on the link newspotheres.xyz:
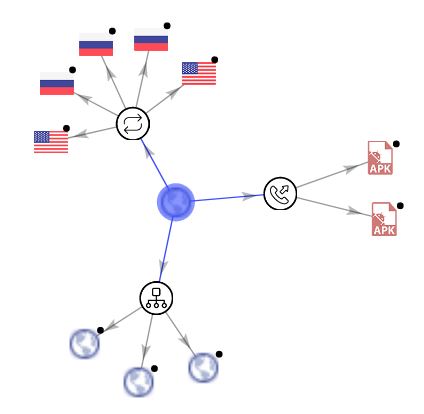
Based on the hardcoded url's obtained in the code we created a VirusTotal Graph as shown below:
SonicWall Capture Labs provides protection against this threat via the following signature:
- AndroidOS.AndroidBot.DX
Indicators of Compromise (IOC):
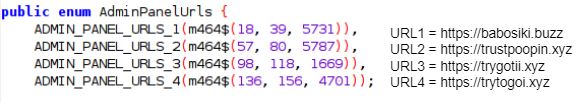
We have blacklisted the following URLs:
- https://newspotheres.xyz
- https://babosiki.buzz
- https://trustpoopin.xyz
- https://trygotii.xyz
- https://trytogoi.xyz
Share This Article

An Article By
An Article By
Security News
Security News