Capture Client: Purpose-Built for the Distributed Workforce

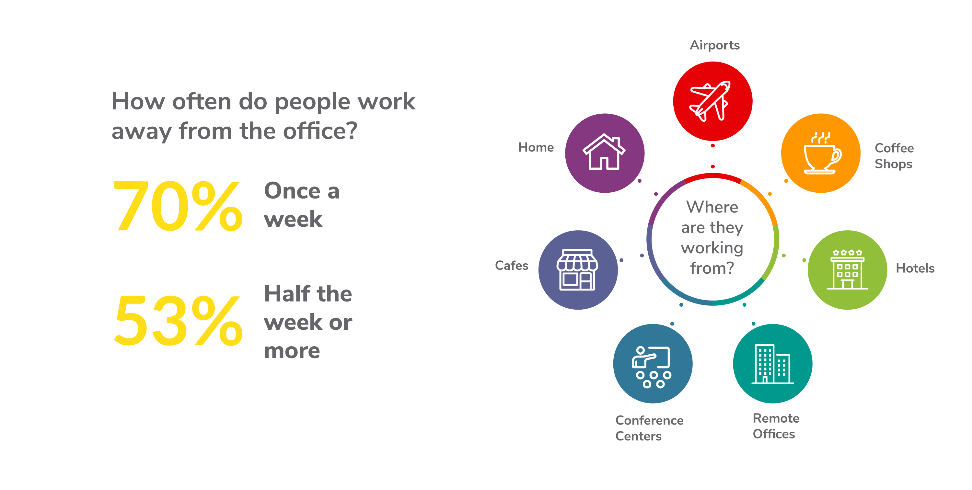
Before COVID-19 shelter-in-place orders were enacted across North America, I created several educational pieces on the subject of the distributed workforce. At that time, 70% of endpoints in the average company could be found outside the walls of the office at least once a week, and 53% of them could be away from perimeter defenses and physical accountability half of the week or more.
Now that this percentage has risen to nearly 100%, the focus at SonicWall is to give companies more visibility into what endpoints are doing, as well as more tools to keep people accountable, productive and safe online, whether or not they are coming in through VPN.
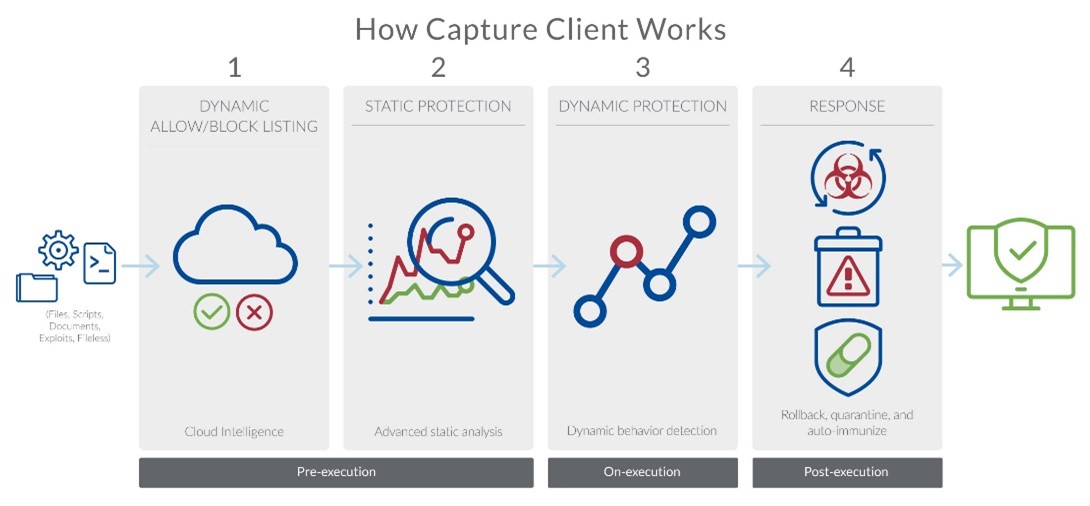
SonicWall Capture Client was designed to be a standalone security offering with optional built-in synergies with the SonicWall ecosystem. It was intended for the distributed workforce from Day One, and since then we’ve added more tools to stop attacks before they can damage systems, more freedom to add granular controls to web content, and soon, more tools for those who manage tenants.
From the solution’s first build, the goal has been to stop attacks before and as they execute, with remediation steps to quickly resolve problems if an attack ever causes damage. Since those early days, we’ve added Capture ATP sandboxing integration, Device Control to stop infected USB devices, Attack Visualization and more.
Today, Capture Client is widely relied on to keep remote employees safe from outside threats as well as from harmful web properties. By combining Security, Web Filtering and Device Control, Capture Client offers an ideal work-from-home solution:
Security
SonicWall has always been a security-first company. From our beginnings in network security, protecting endpoints from outside threats is in our corporate DNA.
Since many endpoints may not be connecting with the company infrastructure via VPN, endpoint security is usually the first and last line of defense. By leveraging the SentinelOne anti-malware engine, which combines AI with Capture ATP sandboxing integration, we are stopping most (nearly all) attacks before and as the execute. First, the AI engine is constantly monitoring system changes for malicious intent. Secondly, if the engine can’t fully convict a suspicious file, it will be sent to a Capture ATP PoP (Point of Presence) for evaluation. Since Capture ATP can do more with a file than your endpoint is allowed to do by the OS, it can flush out sleeping or seemingly innocuous threats.
This means that, if an employee downloads a malicious attachment from their private email or lands on an infected phishing site, Capture Client’s continuous monitoring technology will stop the attack and inform the end user of the event. If an employee downloads a file designed to activate and connect with a C&C server at a designated time in the future, Capture ATP will identify the threat. If remediation is required, administrators can step in and quickly get any Windows machine back to its last known clean state, no matter where the endpoint sits.
Web Filtering
Years ago, SonicWall first developed Content Filtering Service (CFS) for firewalls — and Content Filtering Client (CFC) — based on our work with school districts, where the goal was to protect the most impressionable among us from abusive content and prevent sites like YouTube from taking too much of a school’s bandwidth. CFS and CFC (which is used to enforce the polices on devices away from firewalls) were built with a lot of tools for those that needed it most — but the business community was also able to benefit from its granular control of web content as needed. These tools have now been added to Capture Client for your use; here are some use cases listed in order of commonality for business users:
Blocking malicious content
The little-known secret that I am trying to reveal is that a lot of companies have access to Content Filtering in one shape or form, but don’t use it. You don’t have to get fancy with it; you can simply use it to block millions of known malicious phishing sites, hacking domains and other malicious IP addresses (think botnets or C&C servers).
Blocking inappropriate material
Every company has an Internet usage policy to help employees avoid certain categories of web content. There are over 50 categories such as Adult/Mature Content, Drugs/Illegal Drugs, Illegal Skills, or Nudism that can be blocked.
Blocking specific social media outlets
When shelter-in-place orders forced workers to stay in their homes, the first complaints from admins I heard (outside of VPN connectivity) were about trying to keep the network open for business traffic due to too many users watching TikTok videos. Some admins will create granular policies to block TikTok, yet keep YouTube open. Policies can also be created to give marketing departments access to Facebook and Twitter, but block their use by those in other departments.
Bandwidth management
If, for example, YouTube is taking up too much bandwidth as people are pulling it through your servers via VPN, one could limit the amount of bandwidth a specific web property can use.
Device Control
In 46% of American homes, both parents are working — which means endpoints from two different companies may sit side by side most of the day. How many of these couples use the same USB devices? Capture Client has the ability to block unknown devices from connecting to the employee endpoint to prevent infection by a compromised USB from another company’s endpoint. If malware was to jump between companies in 2020, this might be a top-three threat vector. But even if you don’t use the Device Control feature, the AI engine within Capture Client will still notice the malicious behavior and stop any malicious scripts from executing.
Conclusion
In short, Capture Client helps secure work-from-home by being a top-in-class, first and last line of defense against online attacks and infected devices, as well as enforcing your internet usage policies. If you’d like more information on how Capture Client keeps people working safely no matter where they are, you’re welcome to listen to one of my recent webcasts, “You Can’t Stop What You Can’t See.”
Share This Article

An Article By
An Article By
SonicWall Staff
SonicWall Staff