Inside Cybercriminal Inc.: SonicWall Exposes New Cyberattack Data, Threat Actor Behaviors in Latest Report

For cybercriminals and threat actors, the digital frontier is a lawless panorama of targets and opportunity. Despite the best intentions of government agencies, law enforcement and oversight groups, the modern cyber threat landscape is more agile and evasive than ever before.
For this reason, SonicWall Capture Labs threat researchers work tirelessly to arm organizations, enterprises, governments and businesses with actionable threat intelligence to stay ahead in the global cyber arms race.
And part of that dedication starts with the 2020 SonicWall Cyber Threat Report, which provides critical threat intelligence to help you better understand how cybercriminals think — and be fully prepared for what they’ll do next.
Global Malware Dips, But More Targeted
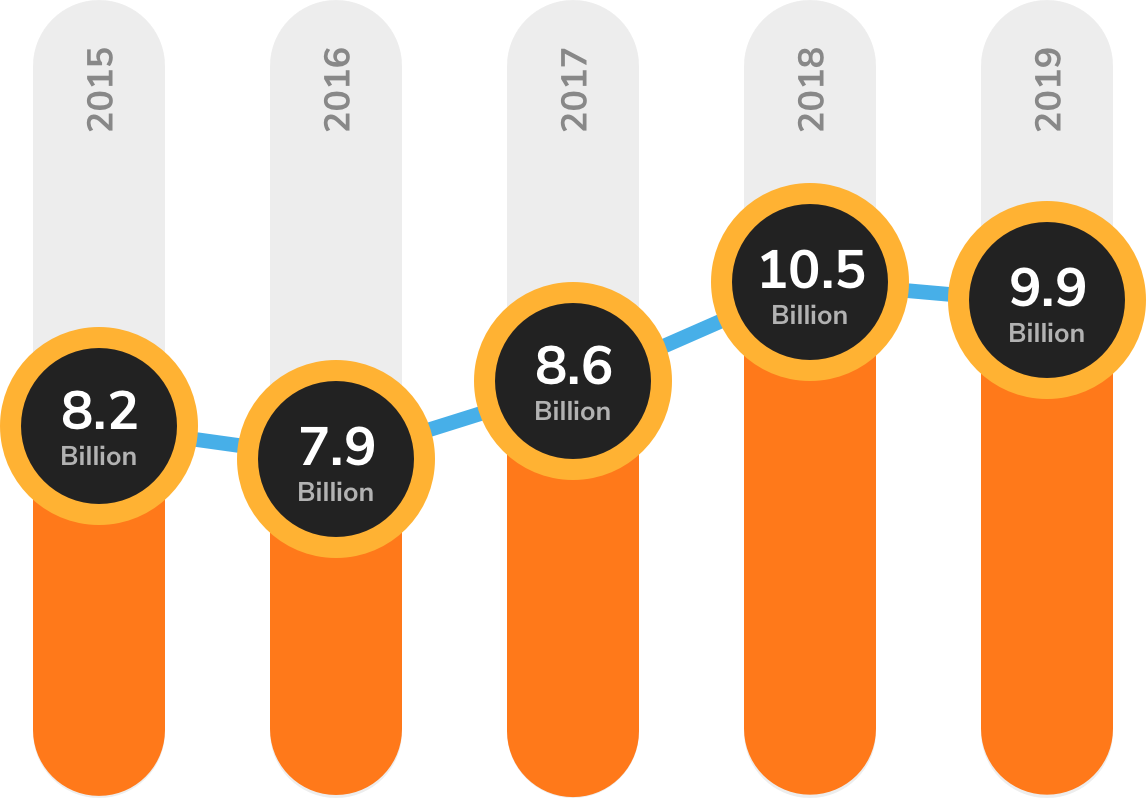
For the last five years, cybercriminals overwhelmed organizations with sheer volume. But as cyber defenses evolved, more volume was not resulting in higher paydays. A change was in order.
In 2018, cybercriminals began to leverage more evasive and pointed attacks against “softer” targets. In 2019, global malware volume dipped, but attacks were more targeted with higher degrees of success, particularly against the healthcare industry, and state, provincial and local governments.
All told, SonicWall Capture Labs threat researchers recorded 9.9 billion malware attacks* in 2019 — a slight 6% year-over-year decrease.
Ransomware targets state, provincial and local governments
‘Spray and pray’ is over. Cybercriminals are using ransomware to surgically target victims that are more likely to pay given the sensitive data they possess or funds at their disposal (or both). Now it’s all about ‘big-game hunting.’
The report outlines the most egregious ransomware attacks of 2019, while also painting a picture of the evolution of ransomware families and signatures, including Cerber, GandCrab, HiddenTear and more.
Fileless malware spikes in Q3
Fileless malware is a type of malicious software that exists exclusively as a memory-based artifact (i.e., RAM). It does not write any part of its activity to the computer's hard drive, making it very resistant to existing computer forensic strategies.
The use of fileless malware ebbed and flowed in 2019. But exclusive SonicWall data shows a massive mid-year spike for this savvy technique.
Encrypted threats growing consistently
Another year, another jump in the use of encrypted threats. Until more organizations proactively and responsibly inspect TLS/SSL traffic, this attack vector will only expand.
IoT malware volume rising
From hacked doorbell cameras to rogue nanny cams, 2019 was an alarming year for the security and privacy of IoT devices. Trending data suggests more IoT-based attacks are on the horizon.
Cryptojacking crumbles
In early 2019, the price of bitcoin and complementary cryptocurrencies created an untenable situation between Coinhive-based cryptojacking malware and the legitimate Coinhive mining service. The shuttering of the latter led to the virtual disappearance of one the year’s hottest malware.
Share This Article

An Article By
An Article By
SonicWall Staff
SonicWall Staff
