Ako ransomware demands $3000. Operators hide behind tOr.

The SonicWall Capture Labs Threat Research Team have recently come across a new variant of Ako ransomware. The malware spreads via spam email and shares similarities to MedusaLocker. This has lead many to believe that the malware is a variant of MedusaReborn. However, the operators have reportedly denied this claim and state that Ako is thier own creation. The malware demands $3000 USD in Bitcoin for file retrieval. The operators run a website hosted behind tOr to facilitate file decryption for its victims.
Infection Cycle:
Upon infection, the malware encrypts files and appends <.random{6}> to their filenames. eg. finance.docx.C564Ec
The following files are dropped into directories where files were encrypted:
- ako-readme.txt
- id.key
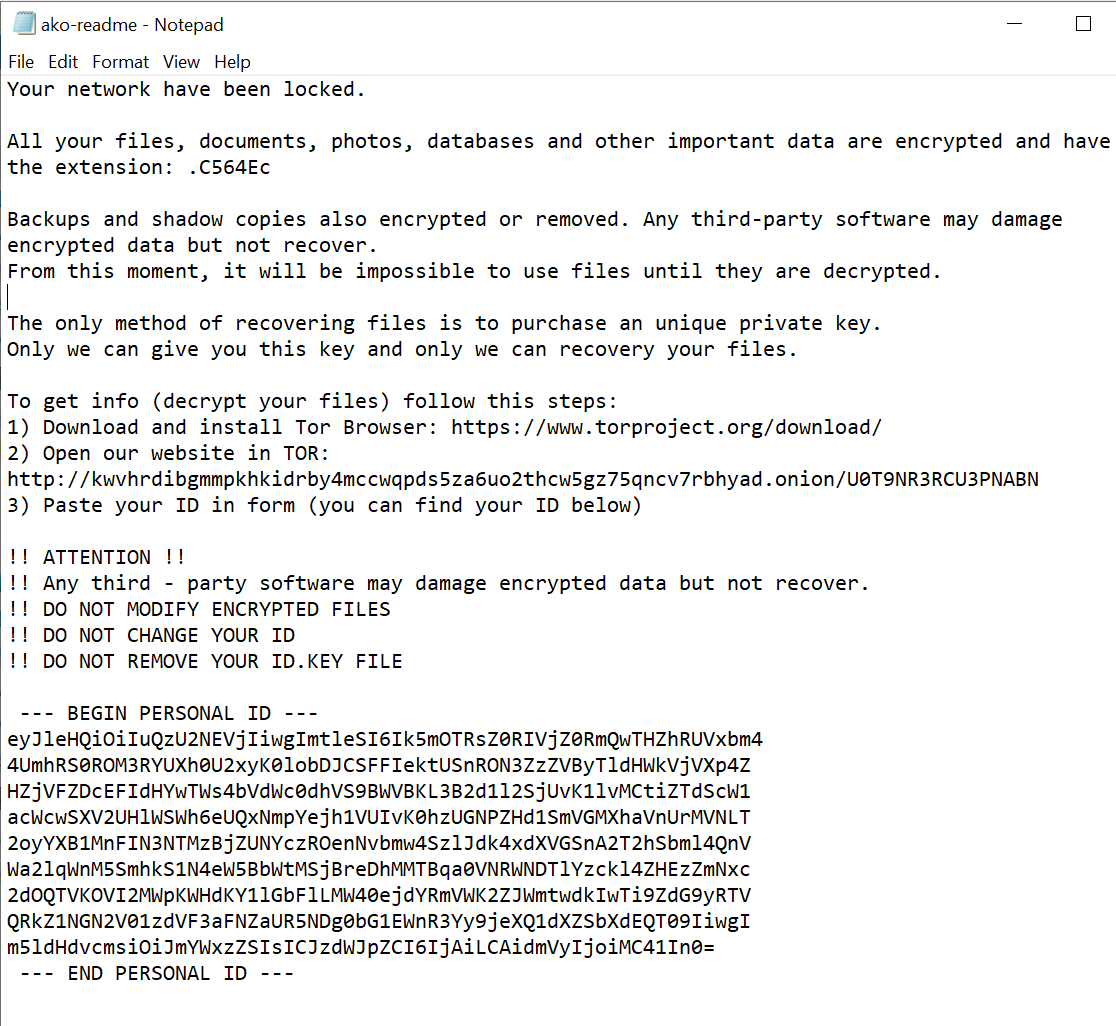
ako-readme.txt contains the following text:
:
id.key contains the public key used to encrypt files.
During the encryption process, the following file types are ignored:
.exe ,. dll, .sys, .ini, .lnk, .key, .rdp
Folders containing the following strings are also skipped:
Appdata
Program files
Program Files (x86)
Appdata
boot
Perflogs
Programdata
Google
Intel
Microsoft
Application data
Tor browser
Windows
Each encrypted file is given the following infection marker (CECAEFBE):
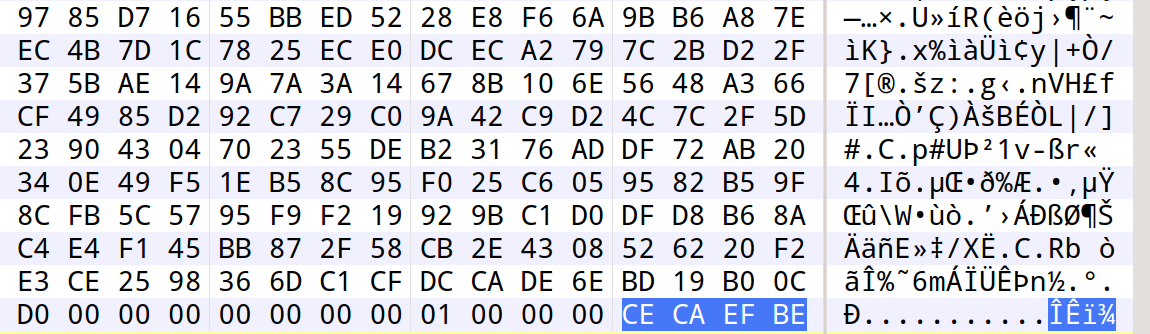
The following keys are added to the registry:
- HKEY_CURRENT_USER\Software\akocfg aid ".<random{6}>"
- HKEY_USERS\S-1-5-21-3032013890-123666948-3153623785-1001\Software\akocfg aid ".<random{6}>"
The following commands are executed to delete shadow copies of files and to disable any possibility of system recovery and repair:
vssadmin.exe Delete Shadows / All / Quiet
bcdedit.exe / set {default} recoveryenabled No
bcdedit.exe / set {default} bootstatuspolicy ignoreallfailures
wbadmin DELETE SYSTEMSTATEBACKUP
wbadmin DELETE SYSTEMSTATEBACKUP -deleteOldest
wmic.exe SHADOWCOPY / nointeractive
The ransom note contains the following tOr address:
http://kwvhrdibgmmpkhkidrby4mccwqpds5za6uo2thcw5gz75qncv7rbhyad.onion/U0T9NR3RCU3PNABN
The address leads to the following site hosted on the tOr network:
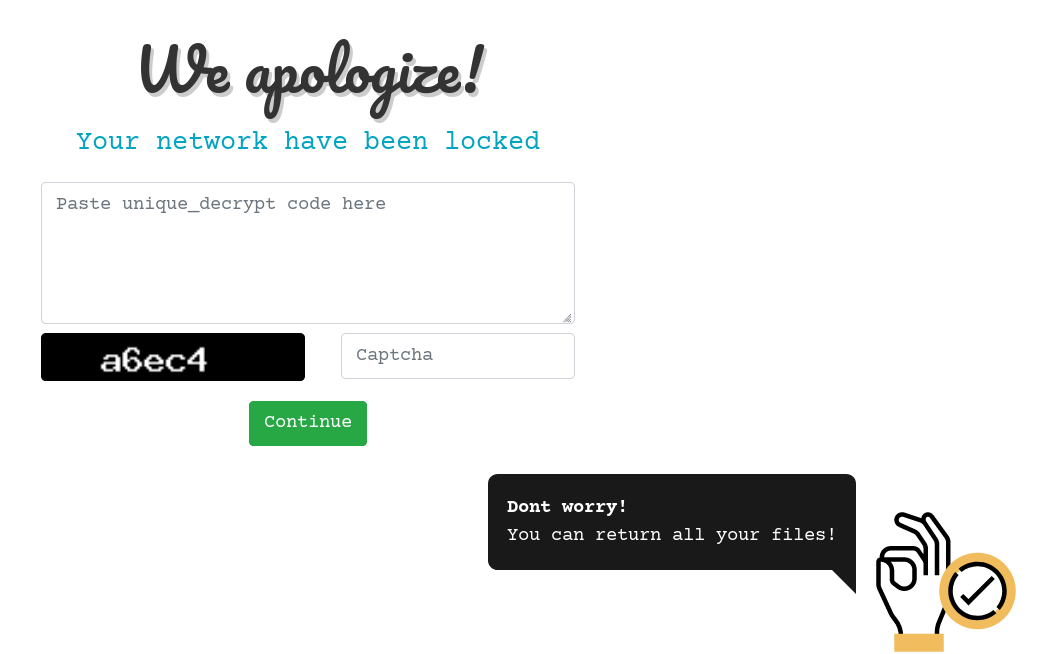
After entering the unique key from the ransom note, the following page is presented which states that 0.2932 BTC (approx $3000 USD at this time) is required to restore files:
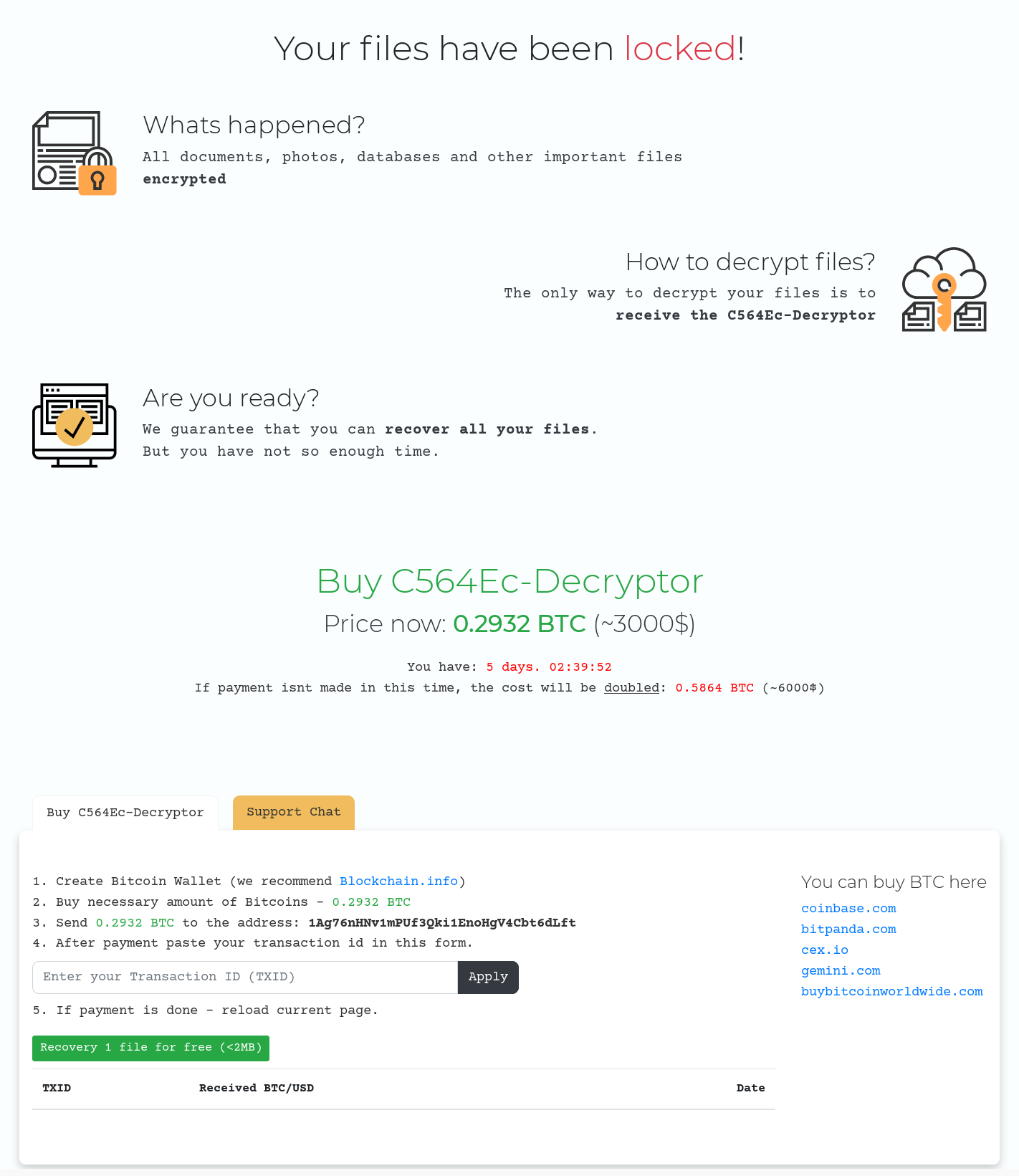
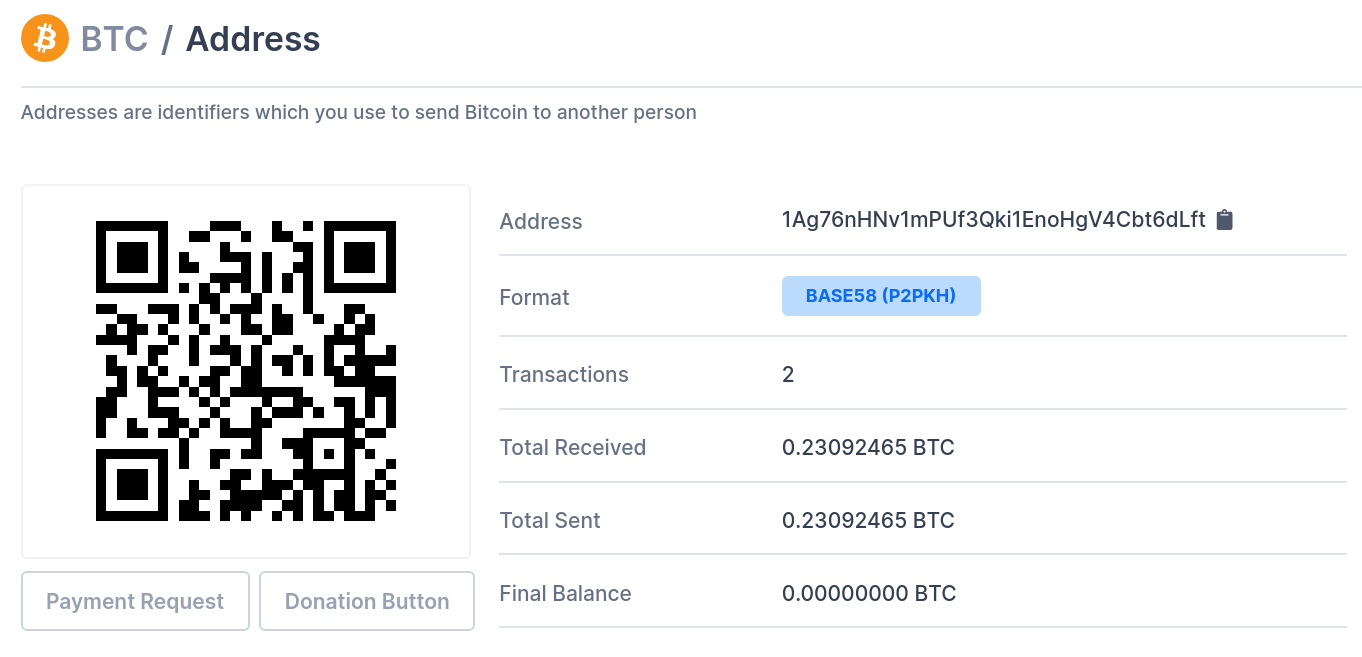
Activity recorded for the supplied BTC address (1Ag76nHNv1mPUf3Qki1EnoHgV4Cbt6dLft) suggests that the operators may have been successful in their endeavours:
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: Ako.RSM (Trojan)
This threat is also detected by SonicWALL Capture ATP w/RTDMI and the Capture Client endpoint solutions.
Share This Article

An Article By
An Article By
Security News
Security News