A group of 10 threat researchers have disclosed a trio of new Spectre-based vulnerabilities that affect Intel chipsets. Named Foreshadow, the threats leverage a CPU design feature called speculative execution to defeat security controls used by Intel SGX (Software Guard eXtensions) processors.
“At its core, Foreshadow abuses a speculative execution bug in modern Intel processors, on top of which we develop a novel exploitation methodology to reliably leak plaintext enclave secrets from the CPU cache,” the research team published in its 18-page report Aug. 14.
The vulnerabilities are categorized as L1 Terminal Faults (L1TF). Intel published an overview, impact and mitigation guidance, and issued CVEs for each attack:
The research team found that Foreshadow abuses the same processor vulnerability as the Meltdown exploit, in which an attacker can leverage results of unauthorized memory accesses in transient out-of-order instructions before they are rolled back.
Conversely, Foreshadow uses a different attack model. Its goal is to “compromise state-of-the-art intra-address space enclave protection domains that are not covered by recently deployed kernel page table isolation defenses.”
“Once again, relentless researchers are demonstrating that cybercriminals can use the very architecture of processor chips to gain access to sensitive and often highly valued information,” said SonicWall President and CEO Bill Conner. “Like its predecessors Meltdown and Spectre, Foreshadow is attacking processor, memory and cache functions to extract sought after information. Once gained, side-channels can then be used to ‘pick locks’ within highly secured personal computers or even third-party clouds undetected.”
Does SonicWall protect customers from Foreshadow?
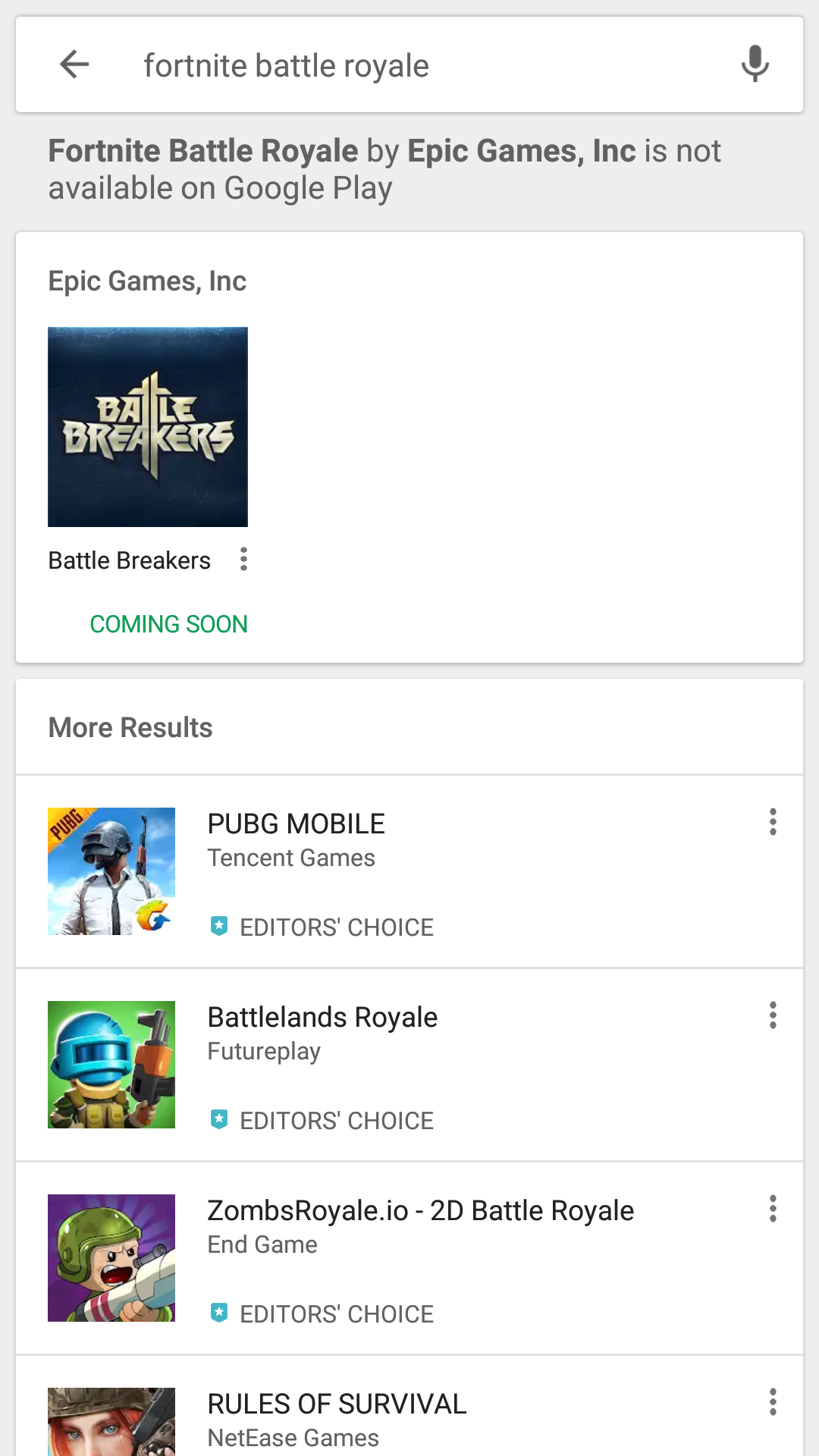
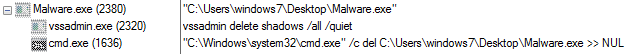
Yes. If a customer has the Capture Advanced Threat Protection (ATP) sandbox service activated, they are protected from current and future file-based Foreshadow exploits, as well as other chip-based exploits, via SonicWall’s patent-pended Real-Time Deep Memory Inspection (RTDMITM) technology.
“Fortunately, prior to Meltdown and Spectre being made public in January 2018, the SonicWall team was already developing Real-Time Deep Memory Inspection (RTDMITM) technology, which proactively protects customers against these very types of processor-based exploits, as well as PDF and Office exploits never before seen,” said Conner.
RTDMI is capable of detecting Foreshadow because RTDMI detection operates at the CPU instruction level and has full visibility into the code as the attack is taking place. This allows RTDMI to detect specific instruction permutations that lead to an attack.
“The guessed-at branch can cause data to be loaded into the cache, for example (or, conversely, it can push other data out of the cache),” explained Ars Technica technology editor Peter Bright. “These microarchitectural disturbances can be detected and measured — loading data from memory is quicker if it’s already in the cache.”
To be successful, cache timing must be “measured” by the attack or it can’t know what is or is not cached. This required measurement is detected by RTDMI and the attack is mitigated.
In addition, RTDMI can also detect this attack via its “Meltdown-style” exploit detection logic since user-level process will try to access privileged address space during attack execution.
SonicWall customers with the Capture Advanced Threat Protection (ATP) sandbox service activated are NOT vulnerable to file-based Foreshadow processor exploits.
How does Foreshadow impact my business, data or applications?
According to Intel’s official L1TF guidance, each variety of L1TF could potentially allow unauthorized disclosure of information residing in the SGX enclaves, areas of memory protected by the processor.
While no current real-world exploits are known, it’s imperative that organizations running virtual or cloud infrastructure, as well as those with sensitive workloads, apply microcode updates released by Intel (linked below) immediately. Meanwhile, SonicWall Capture Labs will continue to monitor the malware landscape in case these proofs of concept are weaponized.
“This class of attack is something that will not dissipate,” said Conner. “Instead, attackers will only seek to benefit from the plethora of malware strains available to them that they can formulate like malware cocktails to divert outdated technologies, security standards and tactics. SonicWall will continue to innovate and develop our threat detection and prevention arsenal so our customers can mitigate even the most historical of threats.”
What is speculative execution?
Speculative execution takes place when processors execute specific instructions ahead of time (as an optimization technique) before it is known that these instructions actually need to be executed. In conjunction with various branch-prediction algorithms, speculative execution enables significant improvement in processor performance.
What is L1 Terminal Fault?
Intel refers to a specific flaw that enables this class of speculative execution side-channel vulnerabilities as “L1 Terminal Fault” (L1TF). The flaw lies in permissions checking code terminating too soon when certain parts of the memory are (maliciously) marked in a certain manner. For more information, please see Intel’s official definition and explanation of the L1TF vulnerability.
Are chips from other vendors at risk?
According to the research team, only Intel chips are affected by Foreshadow at this time.
What is Real-Time Deep Memory Inspection (RTDMI)?
RTDMI technology identifies and mitigates the most insidious cyber threats, including memory-based attacks. RTDMI proactively detects and blocks unknown mass-market malware — including malicious PDFs and attacks leveraging Microsoft Office documents — via deep memory inspection in real time.
“Our Capture Labs team has performed malware reverse-engineering and utilized machine learning for more than 20 years,” said Conner. “This research led to the development of RTDMI, which arms organizations to eliminate some of the biggest security challenges of all magnitudes, which now includes Foreshadow, as well as Meltdown and Spectre.”
RTDMI is a core multi-technology detection capability included in the SonicWall Capture ATP sandbox service. RTDMI identifies and blocks malware that may not exhibit any detectable malicious behavior or hides its weaponry via encryption.
To learn more, download the complimentary RTDMI solution brief.
How do I protect against Foreshadow vulnerability?
Please consult Intel’s official guidance and FAQ. To defend your organization against future processor-based attacks, including Foreshadow, Spectre and Meltdown, deploy a SonicWall next-generation firewall with an active Capture ATP sandbox license.
For small- and medium-sized businesses (SMB), also follow upcoming guidance provided via the new NIST Small Business Cybersecurity Act, which was signed into law on Aug. 14. The new policy “requires the Commerce Department’s National Institute of Standards and Technology to develop and disseminate resources for small businesses to help reduce their cybersecurity risks.”
NIST also offers a cybersecurity framework to help organizations of all sizes leverage best practices to better safeguard their networks, data and applications from cyberattacks.
To mitigate file-based processor vulnerabilities like Meltdown, Spectre and Foreshadow, activate the Capture Advanced Threat Protection service with RTDMI. The multi-engine cloud sandbox proactively detects and blocks unknown mass-market malware and memory-based exploits like Foreshadow.