PayDay – Negotiating ransom with a ransomware operator

The SonicWall Capture Labs Threat Research Team has conducted an experimental dialog with a ransomware operator using the PayDay ransomware trojan. PayDay, is a recent variant of the BTCWare ransomware trojan and has been in the wild for a few weeks. PayDay follows the current ransomware operator trend of using email to communicate with their victims in order to demand payment for file decryption. Payment has increased to an astronomical 0.5 Bitcoins (roughly $8000 USD at today's prices). In this case however, the price could be negotiated lower.
Infection cycle:
Upon infection the following page is displayed on the screen:
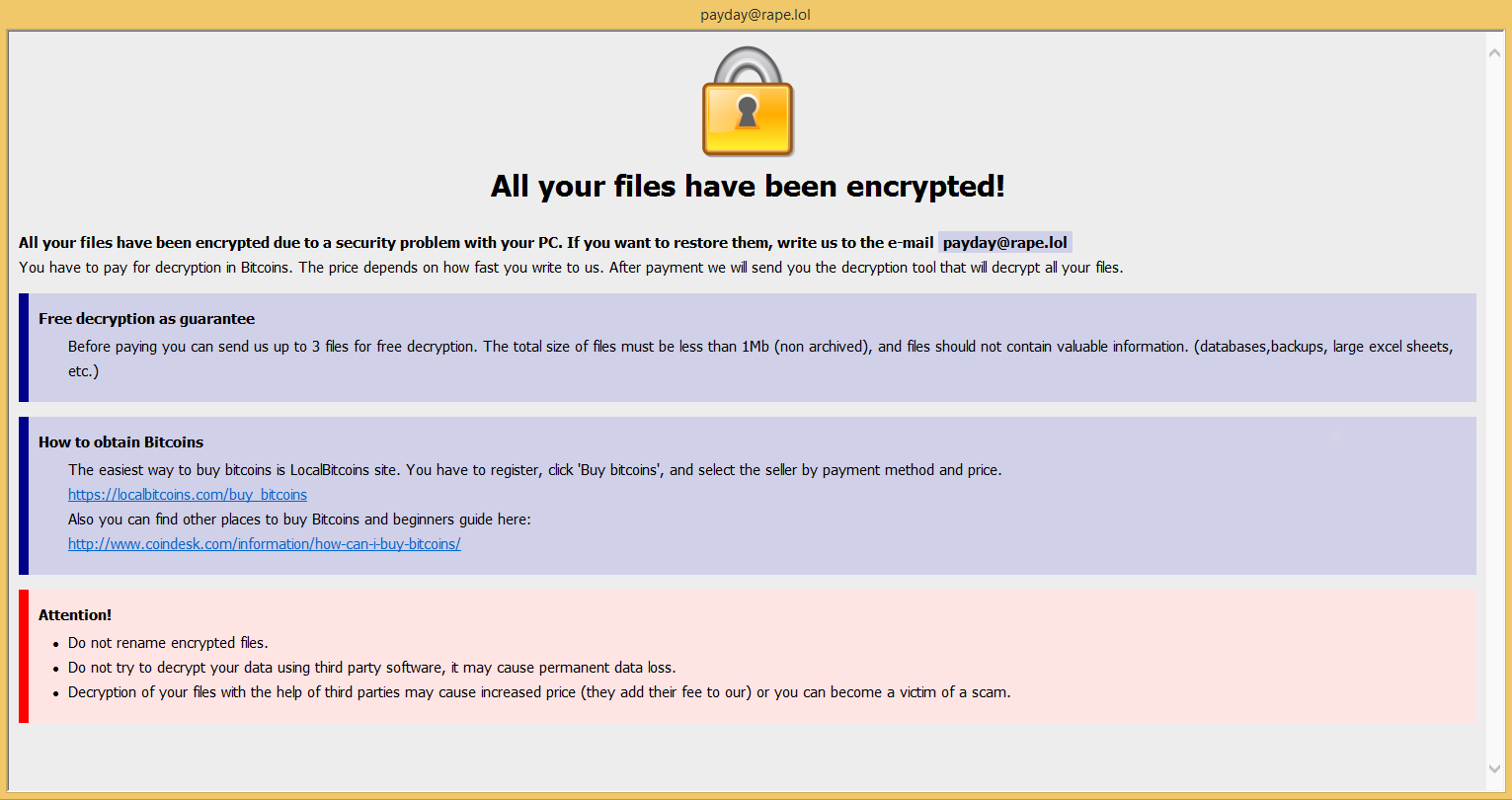
The Trojan makes the following changes to the filesystem:
- encrypts files and adds the following extension to the filename: .-id-1274.wallet
- adds %APPDATA%Roamingpayday.hta (as seen above)
- adds ! FILES ENCRYPTED.txt to any attached drives/network shares after encrypting files
The Trojan adds the following keys to the registry:
- HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun 1payday "%APPDATA%Roamingpayday.hta"
- HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun 2baby "%APPDATA%Roamingpayday.hta"
! FILES ENCRYPTED.txt contains the following message:
Good afternoon. Your computer underwent PayDay infection. All data are ciphered by a unique key which is only at us. Without unique key - files cannot be recovered.Each 24 hours are removed 24 files. (we have their copies)If not to start the program the decoder within 72 hours, all files on the computer are removed completely, without a possibility of recovery.Read Attentively instructions how to recover all ciphered data.PayDay------------------------------------------------------You will be able to recover files so:1. to contact us by e-mail: payday@rape.lol- you send your ID identifier and 2 files, up to 1 MB in size everyone.We decipher them, as proof of a possibility of interpretation.also you receive the payment instruction. (payment will be in bitcoin)- report your ID and we will switch off any removal of files (if do not report your ID identifier, then each 24 hours will beto be removed on 24 files. If report to ID-we will switch off it)2. you pay and confirm payment.3. after payment you receive the program the decoder. Which will recover your data and will switch off function of removal of files.------------------------------------------------------You have 48 hours on payment.If you do not manage to pay in 48 hours, then the price of interpretation increases twice.To recover files, without loss, and on the minimum rate, you have to pay within 48 hours.Address for detailed instructions e-mail: payday@rape.lol
We followed the instructions and sent an email attached with 2 encrypted files to payday@rape.lol. In under 10 minutes we received the following response:
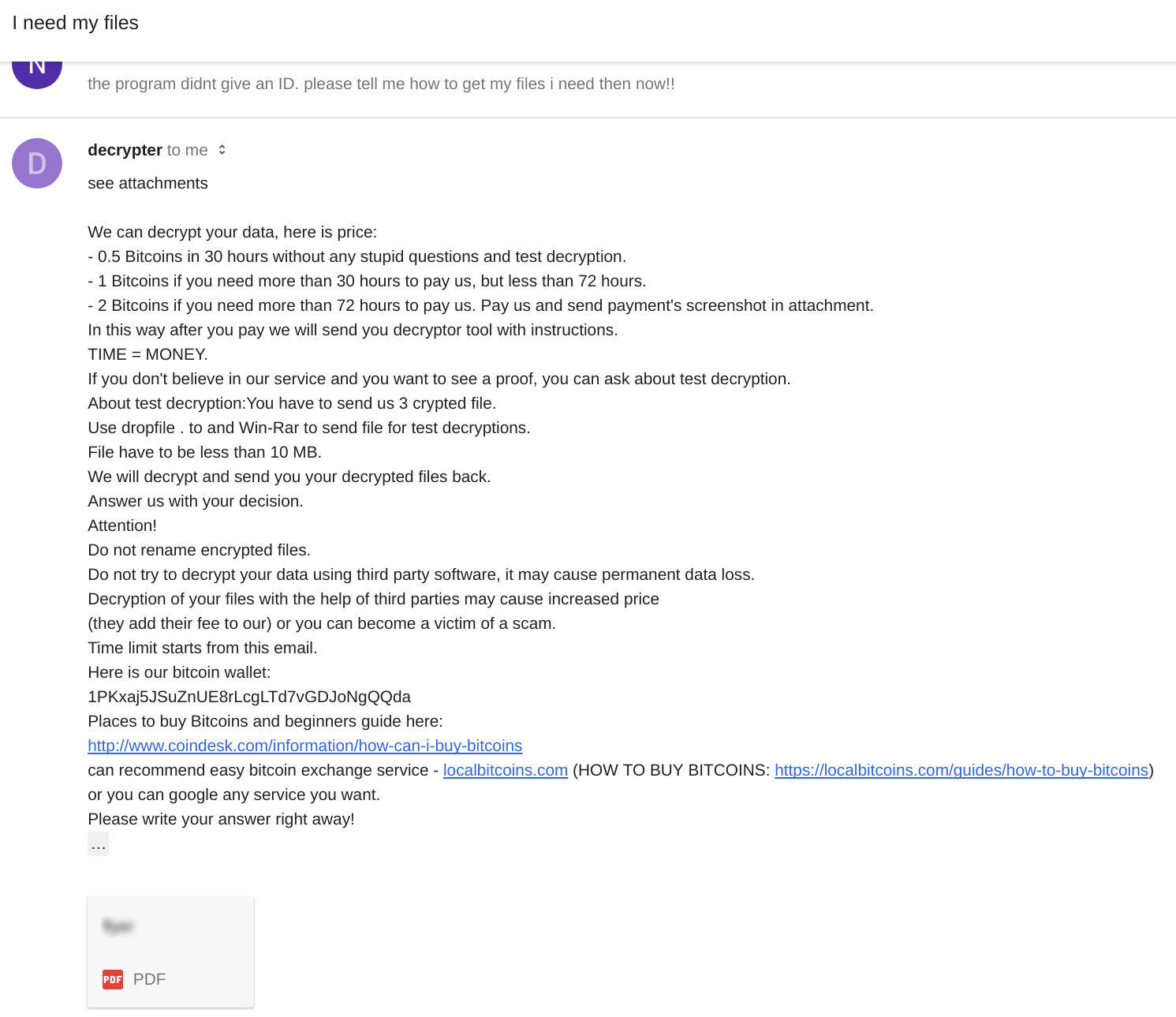
The response included an attachment to one of the encrypted files that we sent for decryption. Although the file content had changed, it remained encrypted. Perhaps the operator had used the wrong key. The response also contained an unused (probably freshly generated) bitcoin address for receiving funds: 1PKxaj5JSuZnUE8rLcgLTd7vGDJoNgQQda.
The conversation continued:
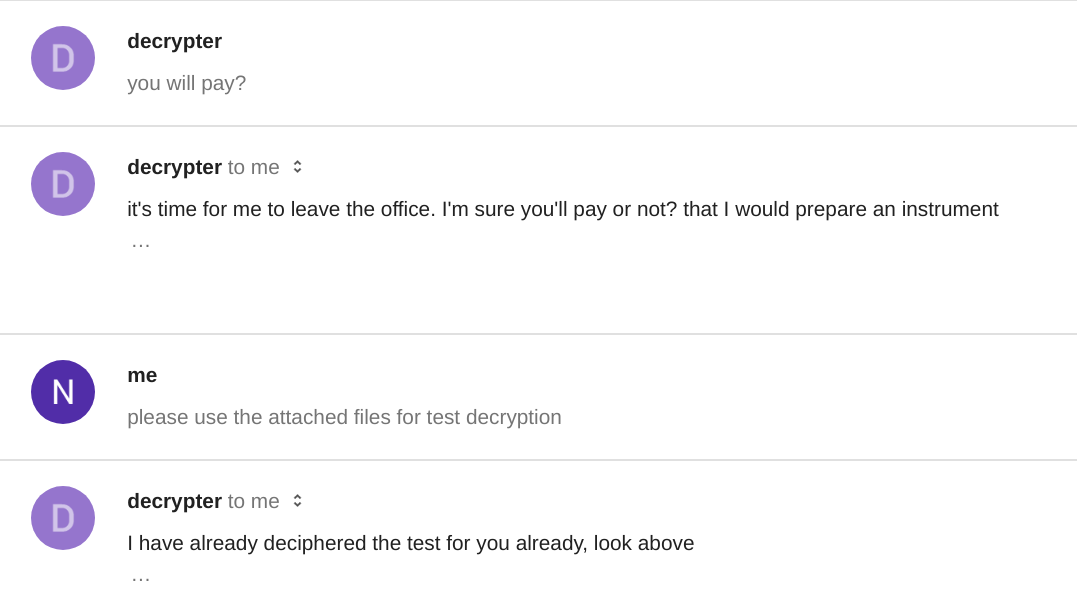
"that I would prepare an instrument" ?? Perhaps a job for a seasoned forensic linguistics team. However, what is more interesting is that the operator is prepared to negotiate the price for decryption and accept my 50% discount offer:
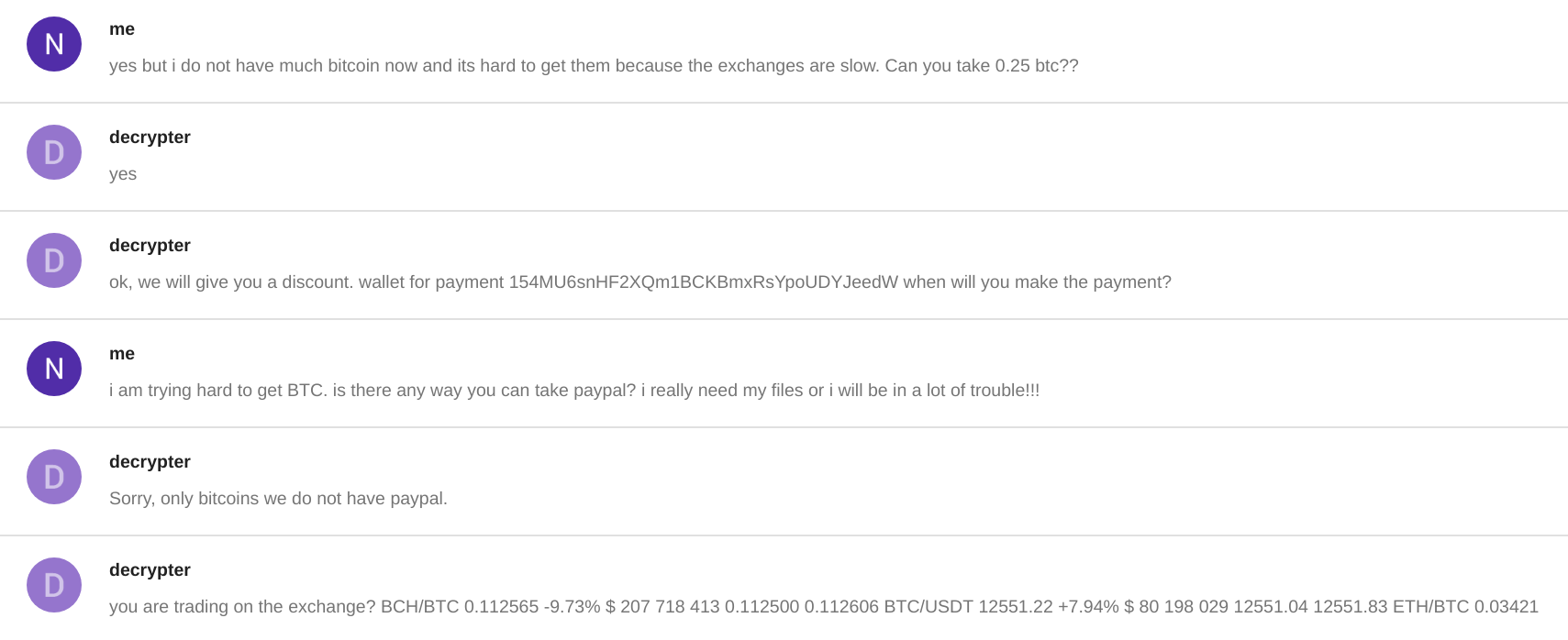
The operator begins to show signs of impatience and offers additional help in my request to (obviously not) pay him via PayPal:
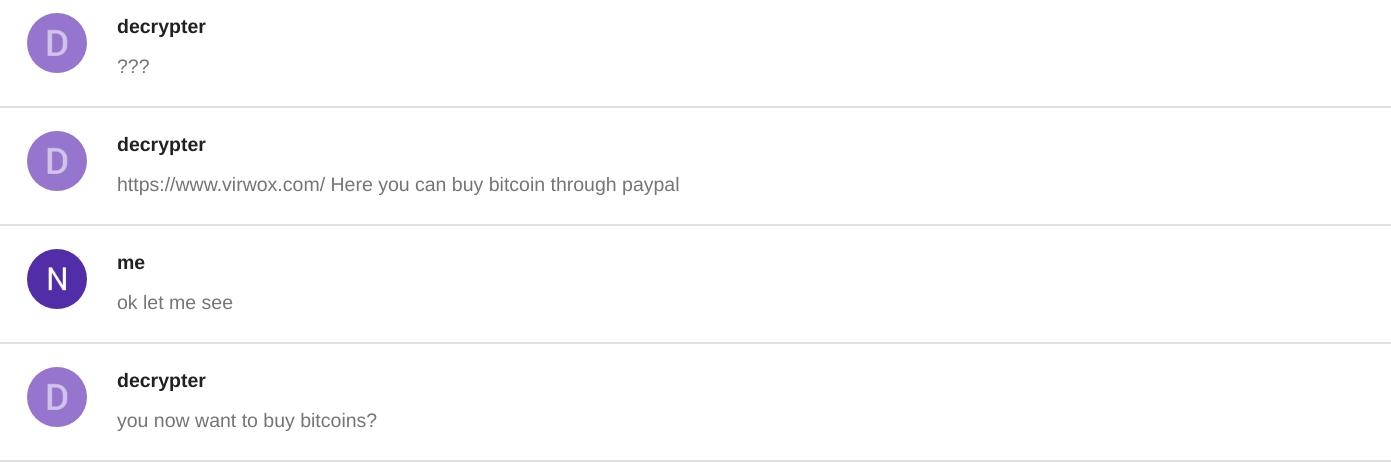
We make a brash attempt to obtain an IP address associated with the operator by causing him to visit a webserver under our control:
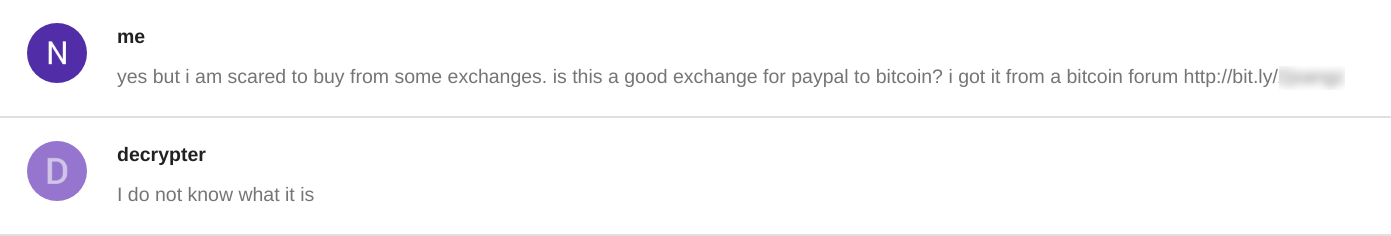
Moments later access logs reveal a visit from an IP address located in the Czech Republic. After perhaps realizing his mistake, there were subsequent visits from IP addresses located in multiple countries around the world.
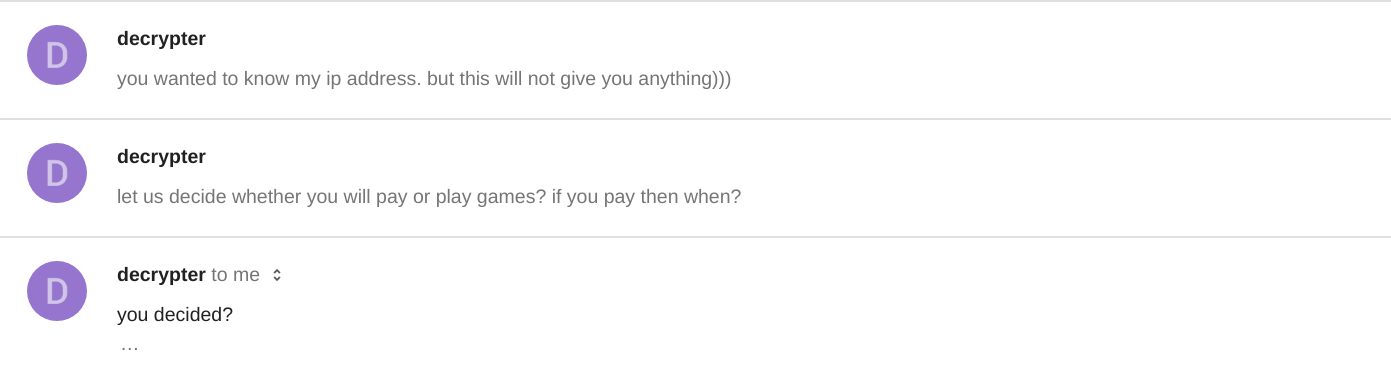
This however, may be the operators attempt to obfuscate his tracks after visiting the site directly the first time.
SonicWALL Gateway AntiVirus provides protection against this threat via the following signature:
- GAV: PayDay.RSM (Trojan)
Share This Article

An Article By
An Article By
Security News
Security News