Ransomware extending to Linux

SonicWall Capture Labs Threat Research Team recently discovered a new update to the Erebus ransomware family capable of infecting Linux servers. Erebus ransomware family, discovered a year ago, initially spread through malvertisements by redirecting the user to Rig Exploit kit, which in turn installed the ransomware on victim's machine. Later Erebus evolved and started using UAC bypassing technique (UAC- A windows feature to prevent unauthorized changes on computer). In its latest form this ransomware is now capable of infecting the Linux servers as well. Erebus infects the data on the Linux server and thus makes the service unavailable for the users.
Initialization
Before going for encrypting the files on the server, the ransomware first make certain initializations to make a log file. The procedure to make log file and the information stored in them are as below: First, the ransomware calls log_init function to create a log file at the following location:
- ./{5f58d6f0-bb9c-46e2-a4da-8ebc746f24a5}//log.log
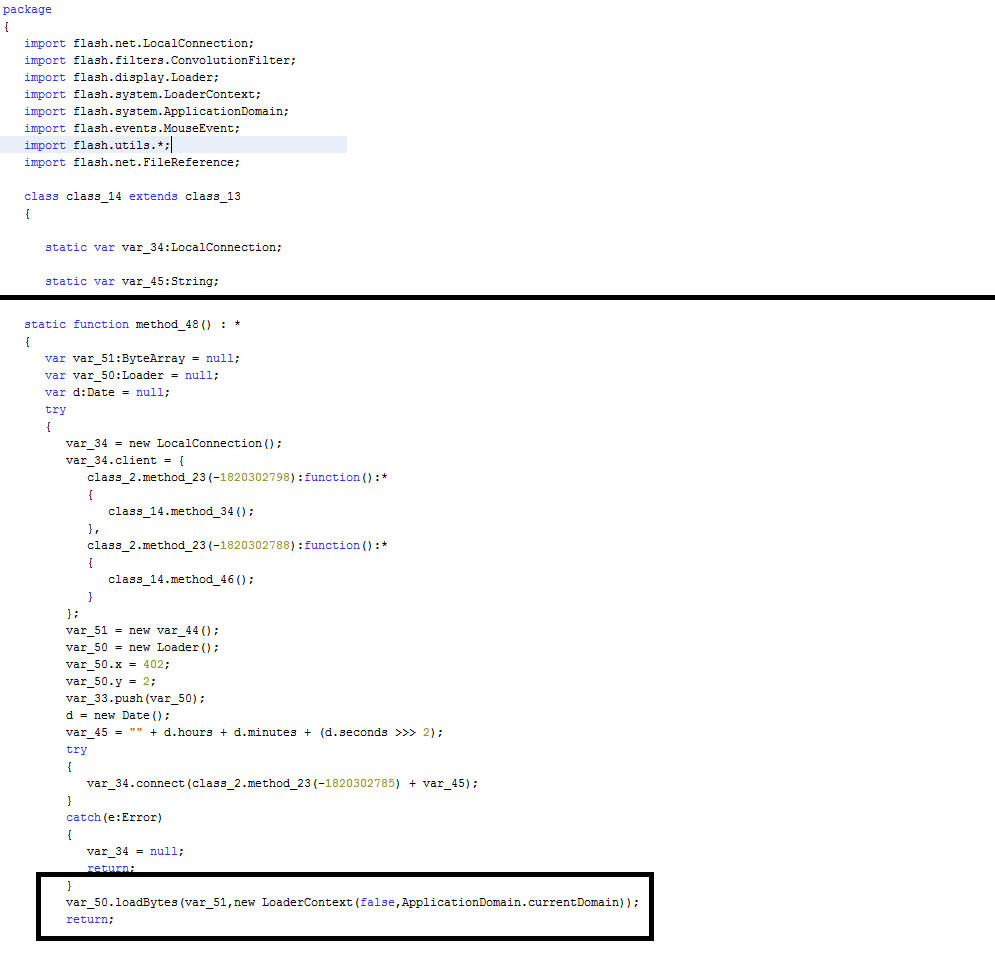
After creating the log file, the ransomware collects information about the processes using g_init_arg function and stores this information in the log file using log_write function.
The ransomware also retrieves the information of the infected system by using g_init function and stores it in the GINFO. GINFO stores the following information:
work_path, self_path, self_hash, os, os_version, os_arch, nic, locale, timezone
It also stores the following information in the GCONF:
- id, seed_sys, seed_hash, password, key_app_rsa_pub, key_rsa_size, cc_server_size, cc_timeout, cc_timeout_conn, url_list_size, url_dn_list_size
The ransomware then send the information stored in GCONF to its C&C server.
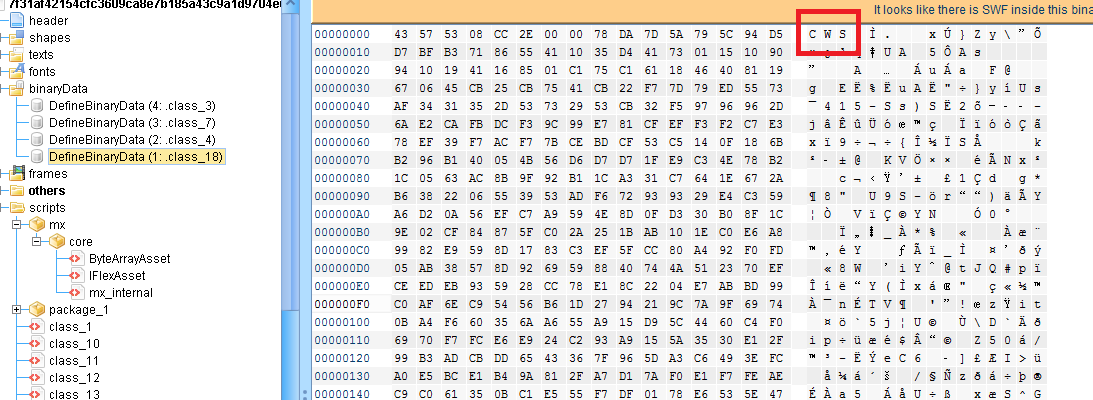
After doing the above configurations, the ransomware finally begins with its encryption routine.
File Encryption Routine
The ransomware performs encryption of the file by using RC4 encryption algorithm for which, it randomly generates the key on the local machine itself.
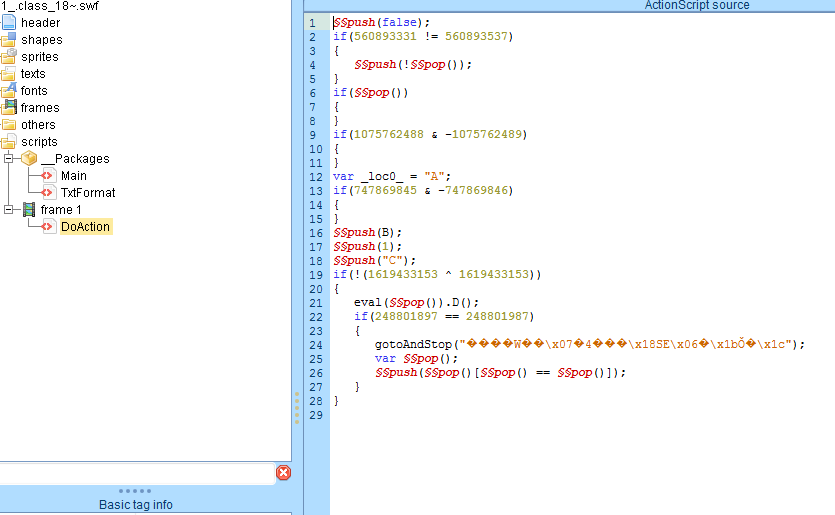
After performing RC4 the ransomware then encrypts the randomly generated RC4 key using AES EBC algorithm with randomly generated key as shown below:
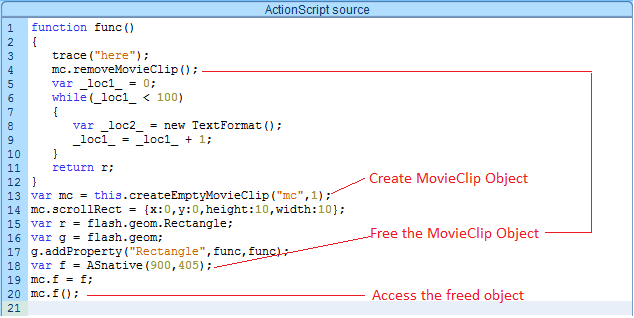
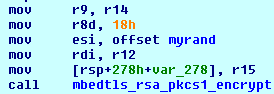
After encrypting the RC4 key using AES EBC, the ransomware encrypts the randomly generated AES key used to encrypt RC4 key, using RSA-2048 algorithm with its public key, thus making decryption of the encrypted files not possible without having the RSA-2048 private key.
The file encrypted by EREBUS ransomware contains the following information:
- 1. Header
- 2. Encrypted original file name
- 3. Encrypted AES key
- 4. Encrypted RC4 key
- 5. RC4 encrypted file data
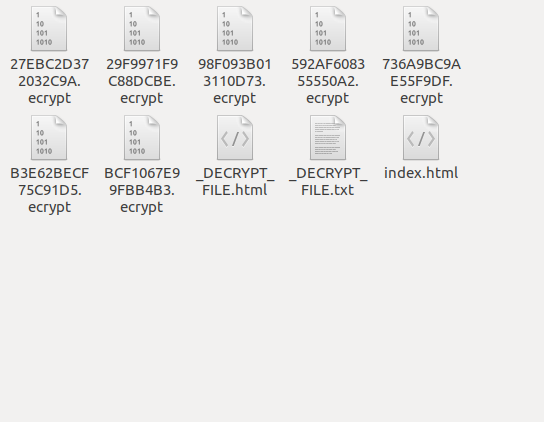
The ransomware then renames the encrypted file with .ecrypt extension and after encrypting the files in the folder, it drops the instruction files with the following names:
- 1. _DECRYPT_FILE.html
- 2. _DECRYPT_FILE.txt
- 3. index .html
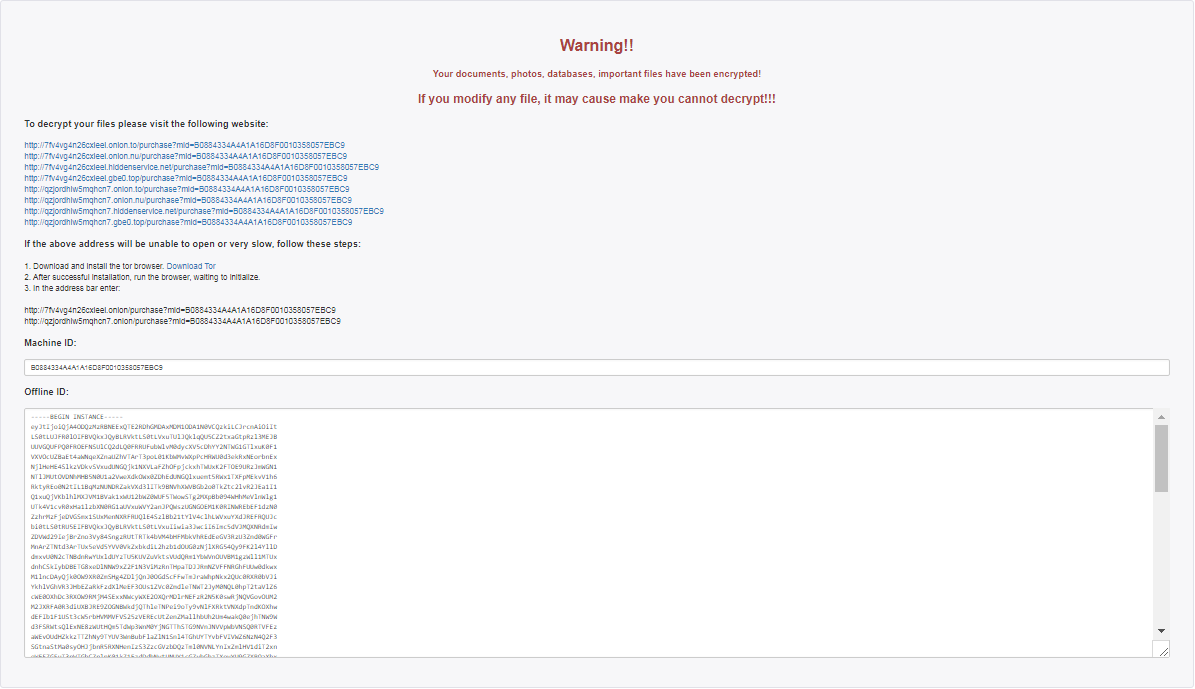
_DECRYPT_FILE contains following information:
The ransomware performs encryption on various extensions; the list of extensions is:

Following is the list of directories and filetypes the ransomware avoids encrypting:

After encrypting the files on the server, the ransomware delete itself from the infected server.
The _DECRYPT_FILE instructs to install TOR browser and visit below site for payment and decrypting the encrypted files on the server
- hxxp://7fv4vg4n26cxleel.onion.to/purchase?mid=B0884334A4A1A16D8F0010358057EBC9
- hxxp://7fv4vg4n26cxleel.onion.nu/purchase?mid=B0884334A4A1A16D8F0010358057EBC9
- hxxp://7fv4vg4n26cxleel.hiddenservice.net/purchase?mid=B0884334A4A1A16D8F0010358057EBC9
- hxxp://7fv4vg4n26cxleel.gbe0.top/purchase?mid=B0884334A4A1A16D8F0010358057EBC9
- hxxp://qzjordhlw5mqhcn7.onion.to/purchase?mid=B0884334A4A1A16D8F0010358057EBC9
- hxxp://qzjordhlw5mqhcn7.onion.nu/purchase?mid=B0884334A4A1A16D8F0010358057EBC9
- hxxp://qzjordhlw5mqhcn7.hiddenservice.net/purchase?mid=B0884334A4A1A16D8F0010358057EBC9
- hxxp://qzjordhlw5mqhcn7.gbe0.top/purchase?mid=B0884334A4A1A16D8F0010358057EBC9
SonicWALL Gateway AntiVirus provides protection against this threat via the following signature:
- GAV: Encoder.RSM (Trojan)
Share This Article

An Article By
An Article By
Security News
Security News